Viewing Component Security and License Information in Nexus Repository 2
Nexus Repository 2
Note
Only available in Sonatype Nexus Repository Pro. Interested in a free trial? Start here.
One of the added features of Nexus Repository Manager Pro is the usage of the curated and up to date information from the Sonatype Data Services. This data contains security and license information about components and is accessible for a whole repository in the Repository Health Check feature.
The Component Info tab displays the security and license information available for a specific component. It is available in browsing or search results, once a you have selected a component in the search results list or repository tree view. An example search for Jetty, with the Component Info tab visible, is displayed in Figure 5.12, “Component Info Displaying Security Vulnerabilities for an Old Version of Jetty”. It displays the results from the License Analysis and any found Security Issues.
The License Analysis reveals a medium threat triggered by the fact that Non-Standard license headers were found in the source code as visible in the Observed License(s) in Source column. The license found in the pom.xml file associated to the project only documented Apache-2.0 or EPL-1.0 as the Declared License(s).
The Declared License details the license information found in POM file or other meta data. The Observed Licenses in Source lists all the licenses found in the actual source code of the library in the form of file headers and license files. This data is based on source code scanning performed and provided by the Sonatype Data Services.
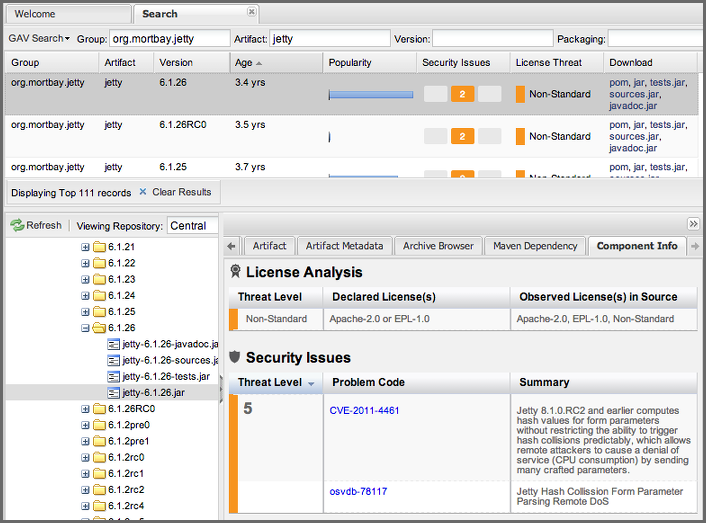 |
Figure 5.12. Component Info Displaying Security Vulnerabilities for an Old Version of Jetty
The Security Issues section displays two issues with Threat Level values 5. The Summary column contains a small summary description of the security issue. The Problem Code column contains the codes, which link to the respective entries in the Common Vulnerabilities and Exposures (CVE) list displayed in Figure 5.13, “Common Vulnerabilities and Exposures CVE Entry for a Jetty Security Issue”.
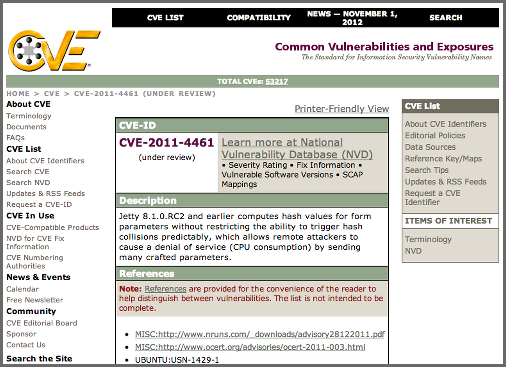 |
Figure 5.13. Common Vulnerabilities and Exposures CVE Entry for a Jetty Security Issue
Understanding the Difference, Nexus Repository Manager Pro and Nexus IQ Server integration. In this section, we’ve talked about the various ways component data is being used, at least at an introductory level. However, understanding the differences between the Sonatype Data Services usage in Nexus Repository Manager Pro and Nexus IQ Server may still be a little unclear. Rather you are likely asking, "What do I get with an integration of Nexus Repository Manager Pro and Nexus IQ Server?"
Policy Management
Your organization likely has a process for determining which components can be included in your applications. This could be as simple as limiting the age of the component, or more complex, like prohibiting components with a certain type of licenses or security issue.
Whatever the case, the process is supported by rules. Nexus IQ Server Policy management is a way to create those rules, and then track and evaluate your application. Any time a rule is broken, that’s considered a policy violation. Violations can then warn, or even prevent a release.
Here’s an example of the Nexus IQ Server features for Staging:
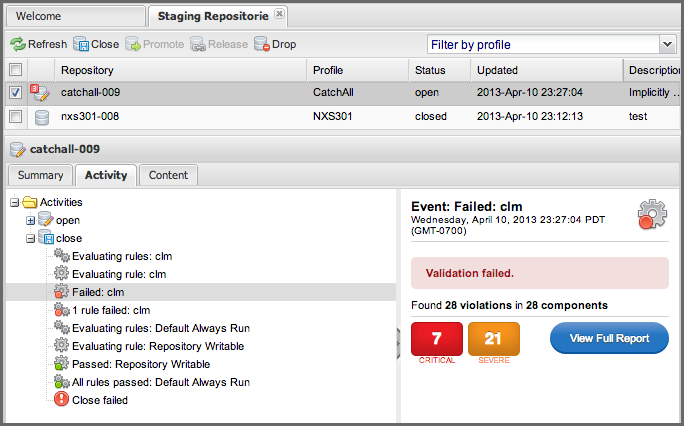 |
Figure 5.14. Staging Repository Activity with a Nexus IQ Server Evaluation Failure and Details
Component Information Panel
The Component Information Panel, or CIP, provides everything you need to know about a component. Looking at the image below, you’ll notice two sections. On the left, details about the specific component are provided. On the right, the graph provides information about the highest policy threat and popularity for each version. You can even click on each individual version in the graph, which will then display on the left.
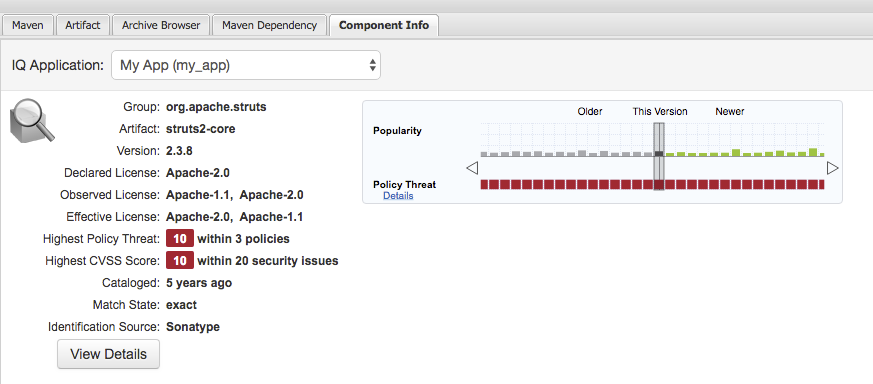 |
Figure 5.15. Component Information Panel Example
Note
The CIP is then expanded with the View Details button which shows exactly what security or license issues were encountered, as well as any policy violations.
Audit and Quarantine
The Audit and Quarantine features use Nexus IQ policy management to protect your development environment from serving risky, unwanted components. You can enable these features to identify, prevent and release such components that may compromise a proxy repository.