Repository Component Details view
Selecting an individual component on the Firewall Dashboard or Repository Results view displays the Component Details view.
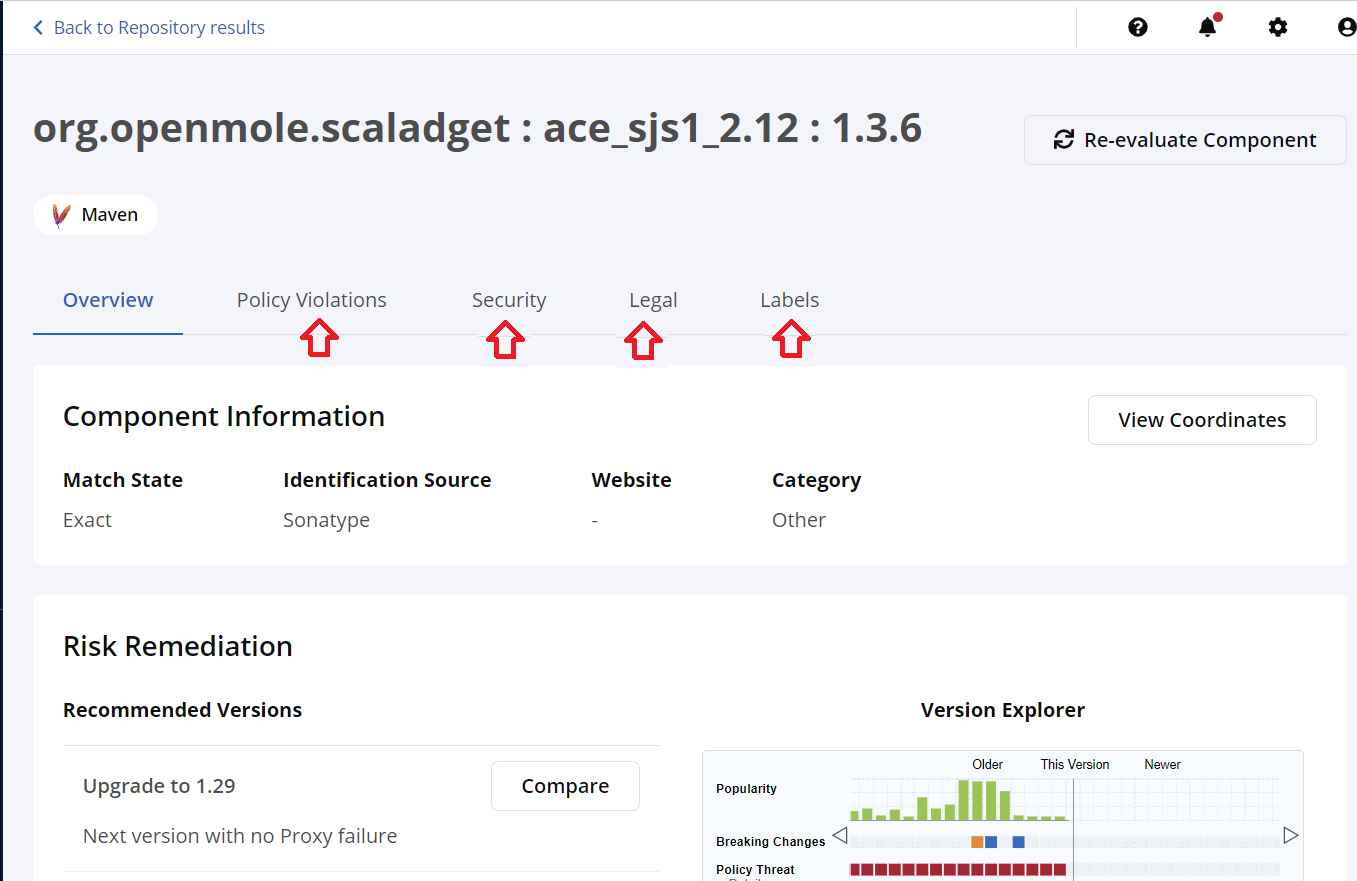
The top section of the component details view has the following panels.
Policy Violations: View all policies violated by the selected component, and view existing or apply new waivers for the component.
Security: View all security policies violated by the selected component, view the component vulnerabilities, and view existing or applied waivers for the component.
Legal: View the effective, declared, and observed licenses for the component, legal policy violations, review the legal obligations, and view existing or apply waivers for the component.
Labels: Assign and manage labels for the selected component.
Component Information contains the match state, identification source, and other component data. Select View Coordinates for the exact component coordinates.
The Risk Remediation section contains the version of the component that is recommended for safe use by our research team.
 |
Re-evaluating a component
Components are evaluated for policy violations when they are first requested through the proxy repository. Quarantined components are automatically re-evaluated every hour for the first 14 days for any changes into their metadata.
See Automatic Quarantine Release for details.
The Re-evaluate Component button may be used to manually re-evaluate the component after the 14-day window has passed or you cannot wait for the hourly automatic re-evaluation.
Selecting the Re-evaluate Component button will analyze the component again for policy violation. This is mostly used to release quarantined components when the failing policy violations have been waived.
Compare Versions table
The Compare Versions table is a comparative analysis of the current and selected component versions, to help decide the remediation action.
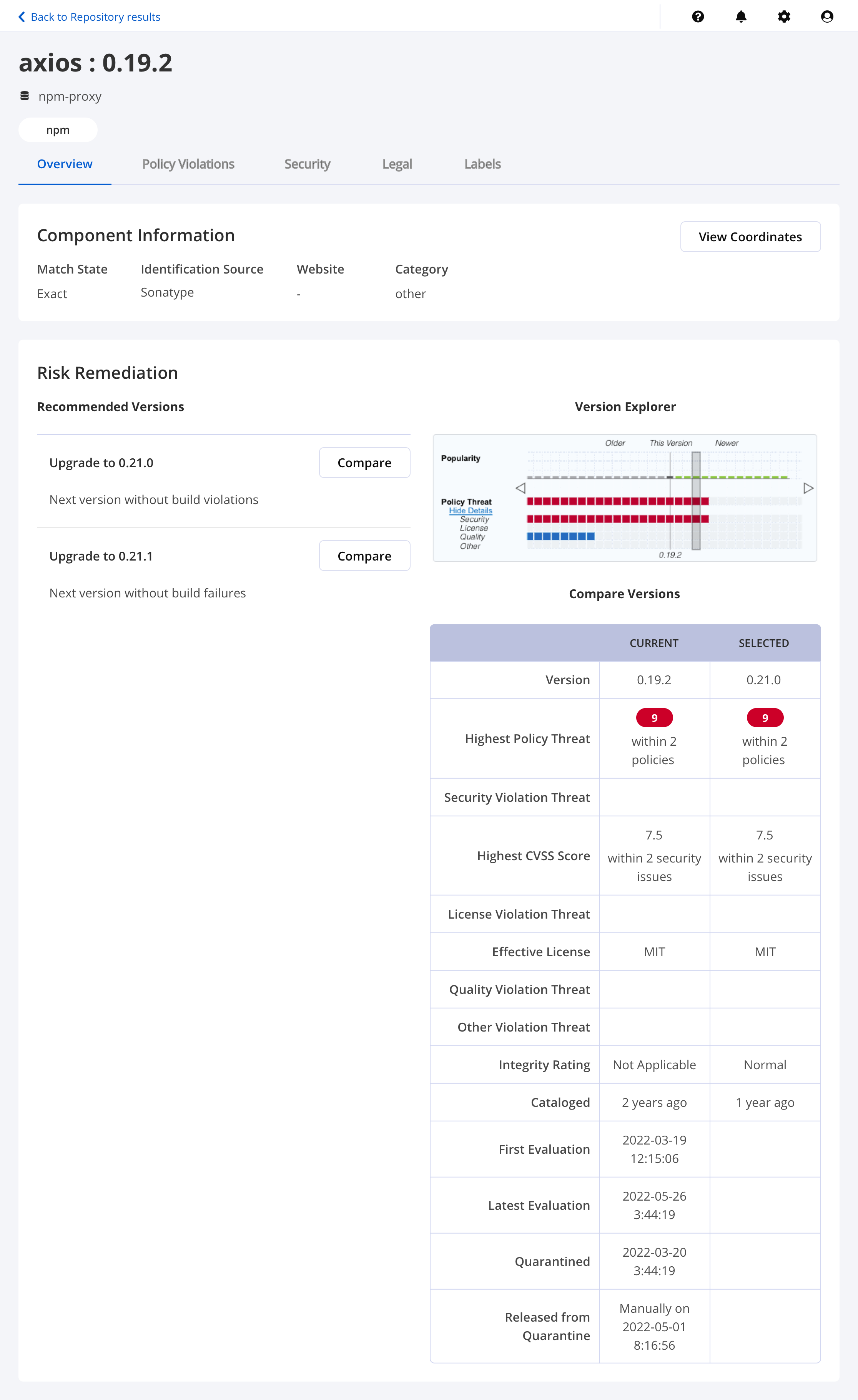 |
Component Profile | What it means |
|---|---|
Version | The version no. of the component |
Highest Policy Threat | The highest threat level policy that has been violated, as well as the total number of violations. The value may be NA if all threats have been waived. |
Security Violation Threat | The security violation threat level. |
Highest CVSS Score | The highest threat level security vulnerability and the total number of security vulnerabilities. The value may be NA if all threats have been waived. |
License Violation Threat | The license violation threat level. |
Effective License | Any licenses included in the Declared or Observed Group, or the overridden license. |
Quality Violation Threat | The quality violation threat level. |
Other Violation Threat | Other violation threat level. |
Integrity Rating | The level of suspiciousness (Suspicious, Normal) of this version is determined by our machine-learning intelligence. Versions that are marked suspicious may be malicious. The value may be Not Applicable if no integrity data is applicable. |
Cataloged | The age of the component is based on when it was first added to the source from which it was identified. |
First Evaluation | Date when the component was first evaluated. |
Latest Evaluation | Latest evaluation date for the component. |
Quarantined | Date when the component was quarantined. |
Released from Quarantine | Date when the component was released from quarantine. |