Malware Risk
Nexus Repository detects malware within your repository and warns users when malicious components are found. We highly recommend Nexus Repository administrators remove the artifacts as quickly as possible to limit these malicious components' impact on their environment.
Recommended Action
Ensure that the Repository Firewall is configured with the
Security-Maliciouspolicy and set to fail at the proxy stage.Do not rename the policy, as this task relies on this name to filter Repository Firewall results to produce a CSV report.
Enable and run the
Automatic Malware ManagementTask.From the Malware Risk Dashboard, download the CSV file containing the malware components that were discovered.
Delete the malware component from the repository.
Allow up to 24 hours for the Malware banner to update.
Discovered Malware Banner
Users logging into Nexus Repository see a warning banner when Malware components are found in their repositories. We recommend users contact their system administrators to report the discovery and request they remove the components immediately.
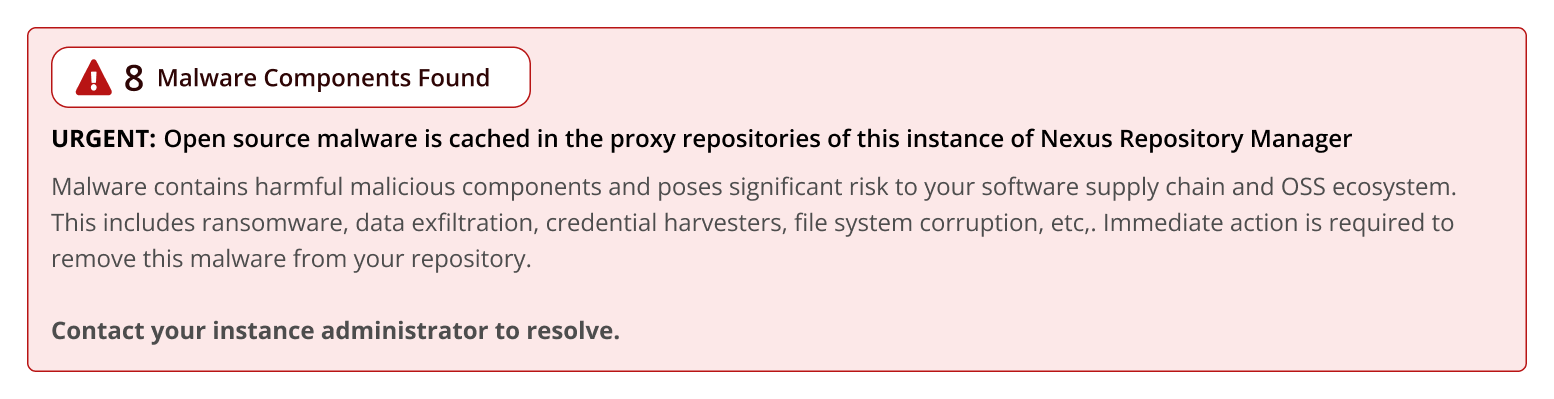
The banner is updated every 24 hours.
Automatic Malware Management Task
The Automatic Malware Management task enhances the security of your repository by identifying potentially malicious components found in your proxy repositories.
This task integrates with your existing Repository Firewall solution to analyze components and flag potential threats. Use Repository Firewall to block your users from downloading malware in the first place.
Requires Repository Firewall Configuration
Using this task requires the Repository Firewall solution. This task fails when a connection to the Repository Firewall cannot be established. This task requires the Repository Firewall enabled with the Security-Malicious policy set to fail to function as expected.
Use the 'Enable Malware Cleanup' option to automatically remove discovered malware
This option auto-deletes identified malware components from the repository when discovered.
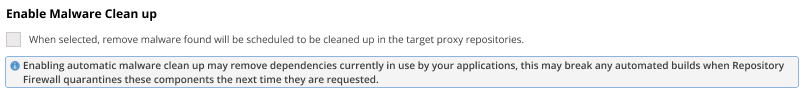
Components that are deleted may be actively used for your application builds. While auto-deleting malware components put your builds at risk of failure, preventing malware components from being released outweighs this risk.
Focus on npm and PyPI
Most malware is discovered on proxies to npm and PyPI repositories. We recommend targeting these repositories first to keep these critical repositories current.
Malware Risk supports the following languages: npm, Maven, PyPI, Nuget
Discrepancies with the malware banner
This task takes time to complete depending on the number of repositories analyzed. During this time the malware banner may report a different quantity than those included in the download list. This discrepancy will most likely resolve itself when the task has time to run and the malware banner is updated once every 24 hours.
A similar issue is when the CSV file lists malware that has been previously deleted for audit reasons. Some components may be found in the CSV that were previously reported on the malware banner but are no longer.
Only need to run once a day
This task should be scheduled to run no more than once a day.
Error when disabling the task
Nexus Repository reports an error in the system status when this task is disabled. Enable the task to keep your repositories protected.
Performance Considerations
Selecting all repositories may result in a long-running task depending on the number of proxy repositories and components in those repositories. For larger deployments, consider setting up multiple tasks to run against larger repositories independently.
See Tasks documentation for details on adding this task.
Malware Risk Dashboard
Only available in Sonatype Nexus RepositoryTM Pro. Interested in a free trial? Start here.
Nexus Repository Pro Administrators have access to the Malware Risk Dashboard which includes details of malware risk in their repositories and how to protect their organization.
This information is available for Repository Firewall users.
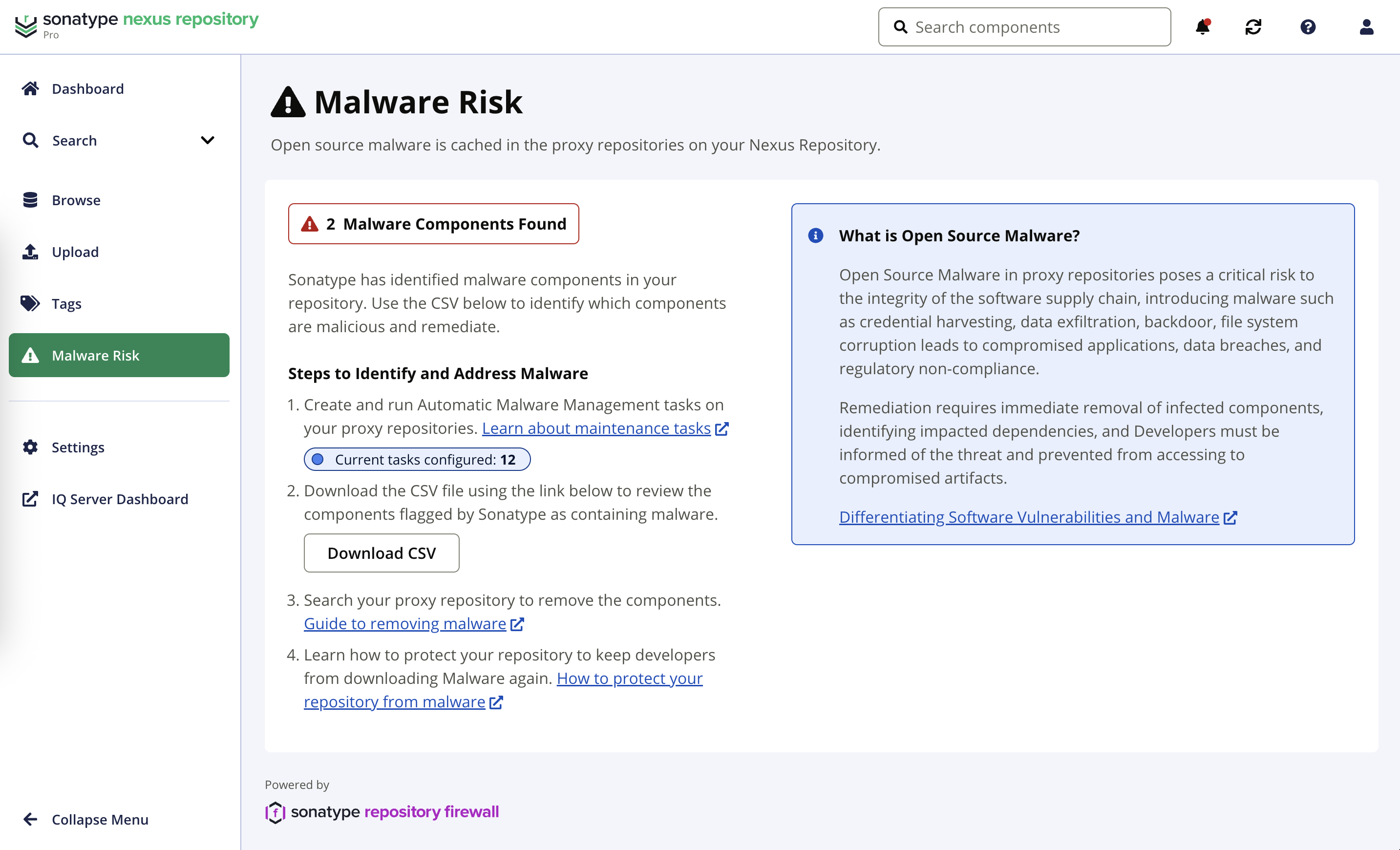
Open Source Malware Protection Status
This dashboard reports the risk of malware found by Sonatype in public ecosystems. The dashboard reports the number of proxy repositories currently protected from Malware using Sonatype Repository Firewall.
Steps to Remediate
Use the following steps to find and remove malware components from your repository.
Download the CSV file using the link below to review the components flagged by Sonatype as containing malware.
Search your proxy repository to remove the components.
Protect your repository to keep developers from downloading Malware.
Download the CSV File
The CSV file contains the following data. you may use to identify and locate the malicious components. This is a consecutive running list that includes identified components and their status on when they have been deleted.
Id, Repository Id, Asset Id The internal database identifiers for the discovered malware.
Format The format for the component.
Properties Includes the component hash and path to locate the component as well as the IP address and account name of the user who initially downloaded the component.
Recorded Time Timestamp of when the malware component is discovered.
Deleted Time Timestamp of when the malware component is removed.
What is Malware Risk?
Open-source malware is deliberately crafted to execute harmful actions that can severely compromise your system and significantly increase risk. These packages are designed to look legitimate but are malicious entities that often do not even pretend to be working code. They infiltrate software supply chains by exploiting the automation in build or dependency managers, frequently executing on download.
Once downloaded, the damage is often already done. Even one malicious component is too many as it may compromise your entire build pipeline by stealing data, installing more malware, and hijacking systems, sometimes without immediate detection. The more malicious components you have, the greater the risk of exposure, and the more complex it becomes to manage and remediate.
The severity of these threats cannot be overstated. Even when discovered and removed from repositories like PyPI or npm, the absence of a CVE complicates efforts to track and address the threat, leaving systems vulnerable and risk mitigation challenging.
Difference from Open Source Vulnerability
An open-source vulnerability is a weakness that can be exploited to gain unauthorized access to a system or network to cause damage or manipulate it somehow. They are not intentionally malicious.
Packages with vulnerabilities may be used when they do not violate existing policies, and in many cases, a different version of the package can be used that does not have the vulnerability. Regardless, vulnerabilities, whether intentional or not, can leave a system vulnerable to attack. When a vulnerability is identified it is assigned a CVE so developers know about the vulnerability.
Learn more from our closer look at Differentiating Software Vulnerabilities and Malware