Sonatype Nexus Repository 3.73.0 Release Notes
Released October 10, 2024
Highlights in This Release |
|---|
Common Vulnerabilities and Exposures Fix Sonatype Nexus Repository 3.73.0 introduces a re-encryption feature to mitigate CVE-2024-5764. This feature allows administrators to change the encryption key used to protect passwords and other confidential information. Read more below Support for Rust / Cargo Format (Pro Only) Sonatype Nexus Repository Pro now supports Rust / Cargo format hosted, proxy, and group repositories. Note that component upload can only be accomplished via Malware Warning Banner Sonatype Nexus Repository now proactively detects deliberately malicious open-source components designed to mimic legitimate packages while causing harm. Read more below |
Note
For a limited set of users, upgrading to Sonatype Nexus Repository 3.73.0 may fail due to javax.crypto.IllegalBlockSizeException: last block incomplete in decryption during the process of secret encryption introduced in this version. See this support article for troubleshooting help.
What’s New and Noteworthy in This Release?
Support for Rust / Cargo Format (Pro Only)
Nexus Repository Pro 3.73.0 introduces native support for Rust / Cargo, empowering developers to streamline dependency management and enhance the ability to reproduce builds. Leverage hosted, proxy, and group repositories to centralize your Rust dependencies, while Cargo's sparse protocol ensures efficient package fetching. Enjoy compatibility with Cargo versions 1.68+ and robust security and management capabilities, including SSL configuration, user token support, cleanup policies, and more. Pro features like staging, tagging, content replication, and Firewall integration further enhance your workflow.
Note that native Rust / Cargo support is not compatible with the existing community plugin, and data migration is not supported. Component upload is currently limited to the cargo publish command.
See our Rust / Cargo format help documentation for full details.
Note that 3.73.0 administrators may see a Cargo Bearer Token Realm available in the Realms user interface. This is a non-functional Realm that will be removed in our next release.
This feature was made possible through your feedback in the Sonatype Ideas Portal.
Malware Warning Banner
Sonatype Nexus Repository now proactively detects open-source malware components within your repositories to enhance the security of your software supply chain and help you monitor malware risk.
What is malware risk? Open-source malware refers to deliberately malicious open-source components designed to mimic legitimate packages while causing harm, such as data theft or system hijacking. This differs from unintentional vulnerabilities, which are weaknesses in code that can be exploited. Even one malicious component is too many and can compromise your entire build pipeline. The more malicious components you have, the greater the risk of exposure, and the more complex it becomes to manage and remediate. The severity of these threats cannot be overstated. Even when discovered and removed from repositories like PyPI or npm, the absence of a CVE complicates efforts to track and address the threat, leaving systems vulnerable and risk mitigation challenging.
As of release 3.73.0, when Sonatype Nexus Repository identifies malware components, a warning banner alerts both administrators and users in the Nexus Repository interface. This banner updates every 24 hours to reflect the latest malware detection status.
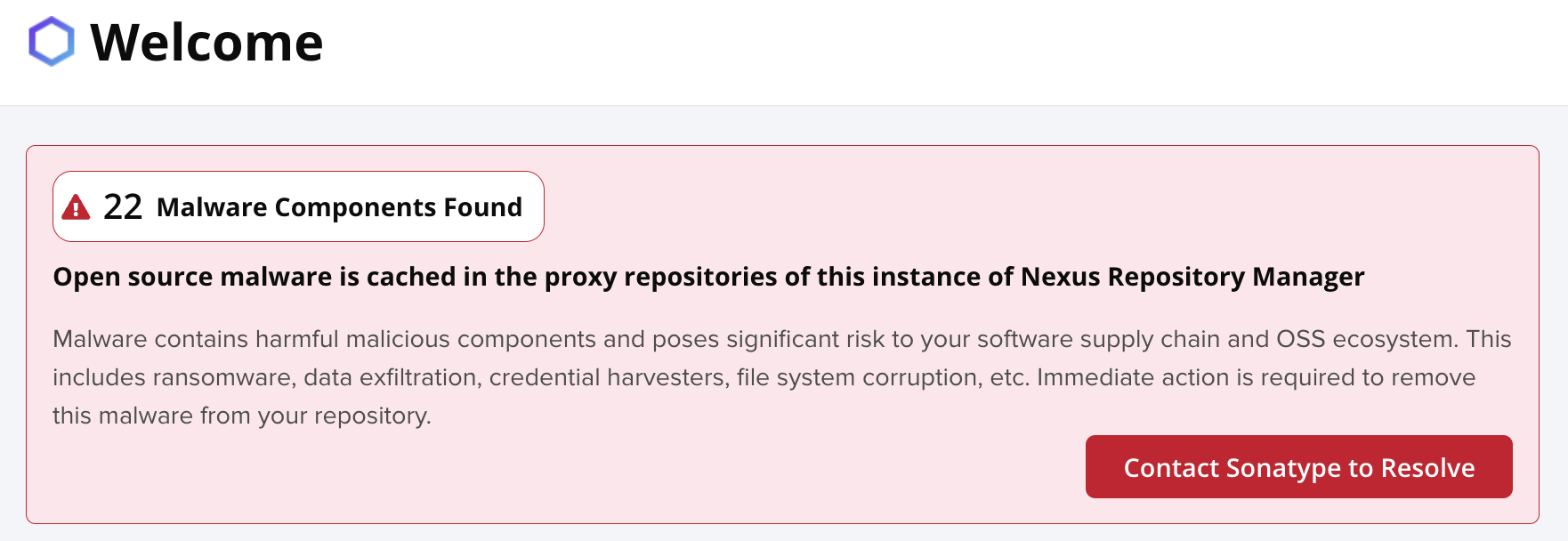 |
Administrators should contact Sonatype using the button within the banner for guidance on remediation; non-administrators seeing a banner should alert their system admins so that they can contact Sonatype.
See our Malware Risk help documentation for full details.
Re-Encryption for Sensitive Data
Sonatype Nexus Repository now offers enhanced security through the re-encryption of sensitive data. Nexus Repository employs reversible encryption to store sensitive data like passwords for certain features. By default, Nexus Repository uses a static key for this encryption. However, administrators can now change the encryption key used to protect passwords and other confidential information, adding an extra layer of protection.
If you have not configured and run re-encryption and are still using the default key, you will see a health check warning with the message "Nexus was not configured with an encryption key and is using the Default key" after upgrading to 3.73.0+. Follow the steps in the re-encryption help documentation to resolve the warning.
This feature also mitigates CVE-2024-5764. See the re-encryption help documentation for full feature details details.
New Parent ID Index
As part of our efforts to improve getByDisplayPath query performance, we have added a new index on parent_id that runs on startup. The new index may slow startup time for large deployments but will allow the retrieval of data based on node_id and parent_id in a very efficient way.
Dependency Changes
Upgrade pax-url-aether from 2.6.7 to 2.6.12
Upgrade protobuf-java from 3.25.3 to 3.25.5
Upgraded keycloak-saml-* and keycloak-admin-client from 12.0.3 to 18.0.2
Bug Fixes
Issue ID | Description |
|---|---|
NEXUS-44488 | You can no longer enable user tokens via capabilities and must use the user token UI or API. |
NEXUS-44370 | Switched order of staging delete and move operations to avoid a concurrency issue when running staging move and cleanup unused asset tasks at the same time. |
NEXUS-44350 | The database migrator utility correctly migrates the |
NEXUS-44337 | Resolved an issue that was preventing the option to retain a select number of previous versions when running cleanup from working as expected. |
NEXUS-44017 | The jmx.json is now included in support zips. |
NEXUS-44005 | Cleanup preview works as expected in H2 environments without an unexpected UI timeout. |
NEXUS-43977 | Changed |
NEXUS-43780 | Updated Helm chart with examples of how to configure the environment variable and key file for the secret encryption keys. |
NEXUS-43764 | After migrating from OrientDB to PostgreSQL, the browse rebuild task only runs once. |
NEXUS-43758 | After migrating to a PostgreSQL database, the search rebuild index task only runs once. |
NEXUS-43687 | Anonymous users are not able to browse after pulling a Docker image unless they log in. |
NEXUS-43648 | Special characters encode as expected for raw proxy repositories. |
NEXUS-43413 | The Maven rebuild metadata task provides meaningful error messaging when it encounters invalid versions. |
NEXUS-43253 | Made adjustments to improve |
NEXUS-43022 | Grouping multiple proxy PyPi repositories works as expected. |
NEXUS-42751 | Logs exceeding the 30MB file size limit are truncated with a truncated marker/ |
NEXUS-42704 | Nexus Repository cleans up yaml metadata as new metadata is generated. |
NEXUS-42207 | There are no longer UI errors when IQ is configured with Firewall audit and quarantine disabled. |
NEXUS-37772 | Yum metadata updates as expected after a cleanup policy removes rpms. |
NEXUS-21389 | Removed inaccurate information about the maximum number of users that the users REST API will return. |