Integrate Firewall with Zscaler
Zscaler is a cloud-native cybersecurity platform to securely connect users, devices, and applications, regardless of their location. Think of it as a security checkpoint in the cloud that all your organization's traffic can pass through for inspection and protection.
Sonatype's Repository Firewall integrates with Zscaler to block actively verified malware components from being directly downloaded from public repositories. This integration protects your organization from malware found in the shadow downloads of users bypassing your Nexus Repository.
See Shadow Downloads Best Practices
Requirements
The configuration for blocking malware is automatic once the Repository Firewall and Zscaler integration is configured. This integration must be configured by an IQ Server Administrator user. Additional settings need to be manually set on in Zscaler.
To complete the setup, use a Zscaler account with one of the following roles:
Super Admin
Admin with the Custom URL Management role
Admin with Custom URL Management and Override Existing URLs roles
Set the URL filtering policy
A policy must to be manually added to block the verified malware components managed by the integration. Add a new url filtering policies are under the Policy → Web → URL and Cloud App Control menu.
Action: BLOCK
Groups: credentials using the client connector
Request Methods: Accept all applicable HTTP request methods
URL Categories: Include the following User-Defined categories added by the integration. These should be added automatically by the integration, however they may be configured manually when not present.
sonatype-maven-shadow-download-defense sonatype-npm-shadow-download-defense sonatype-pypi-shadow-download-defense sonatype-nuget-shadow-download-defense
See Configuring URL Filtering Policy
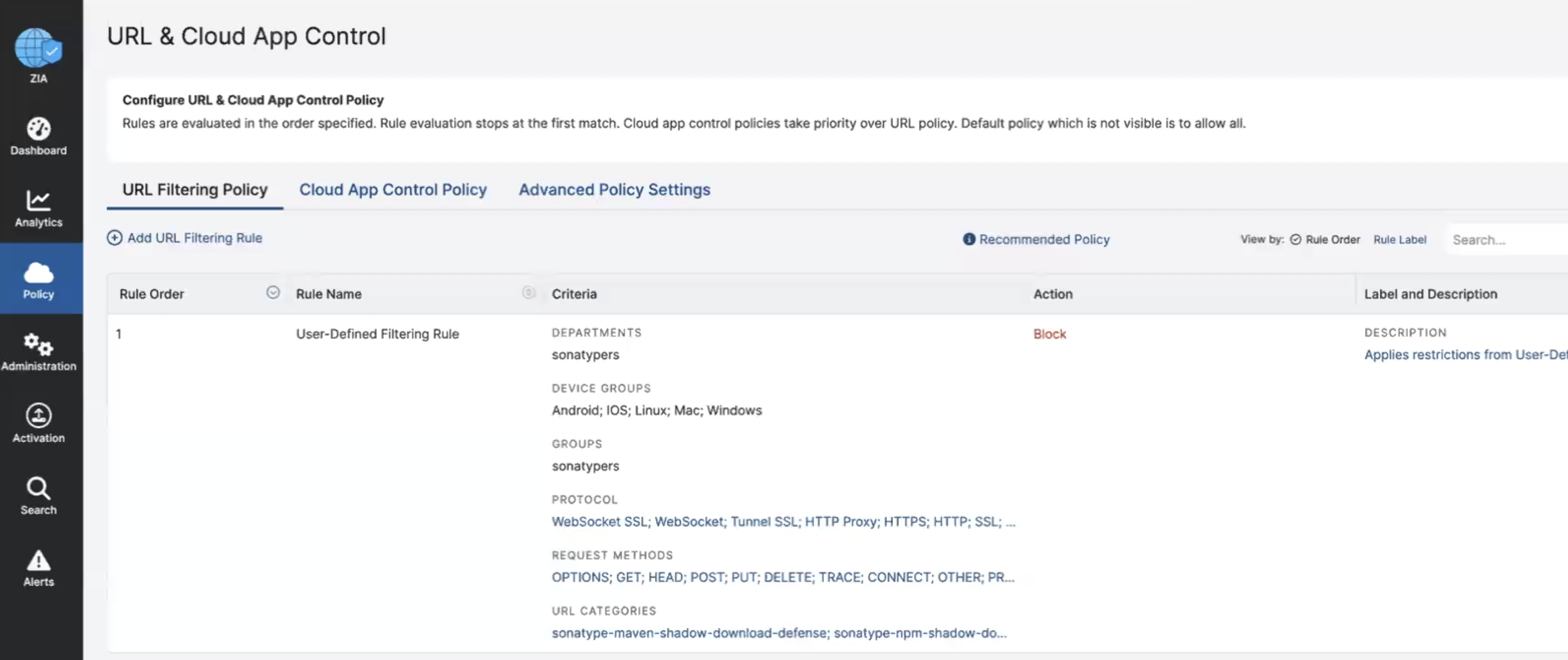
Enable SSL inspection on traffic
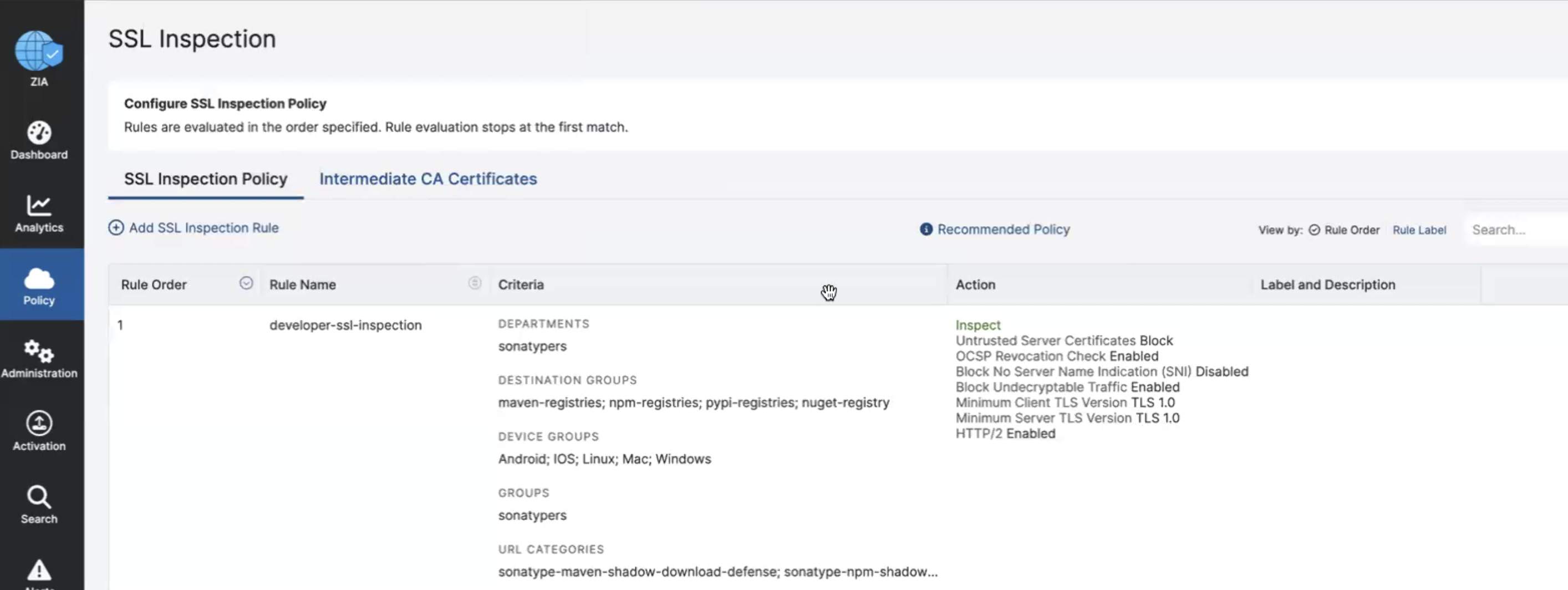
A policy must to be manually added to inspect SSL traffic coming from the client connectors to see the actual requested paths of the malware components. Add a new url filtering policies are under the Policy → Web → SSL Inspection menu.
Action: INSPECT
Groups: credentials using the client connector
Request Methods: Accept all applicable HTTP request methods
Destination Groups: Including the qualified domain names of your target format registries.
maven2-registries: repo1.maven.org, repo.maven.apache.org npm-registries: registry.npmjs.org pypi-registries: pypi.org nuget-registries: nuget.org
URL Categories: Include the following User-Defined categories added by the integration.
sonatype-maven-shadow-download-defense sonatype-npm-shadow-download-defense sonatype-pypi-shadow-download-defense sonatype-nuget-shadow-download-defense
Install Zscaler certificates on your developers' machines

Configuration
An administrator account is required to configure the Zscaler integration. The settings are found in the settings menu for Repository Firewall.
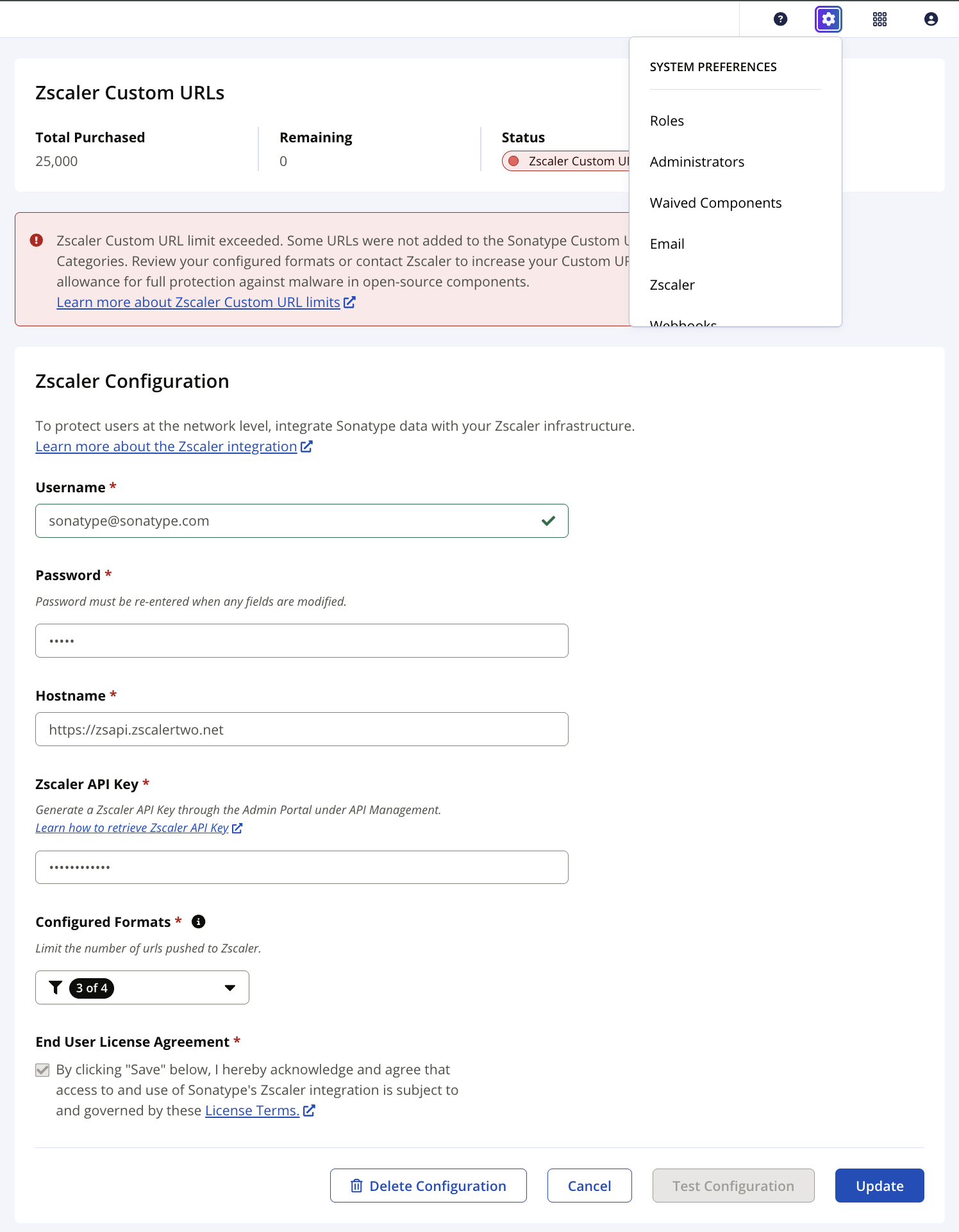
Credentials
Provide your Zscaler administrator account credicatials. This user must be in the Zscaler Global Administrators group.
Hostname
The hostname is the url for your zscaler deployment.
API Keys
Generating a Zscaler API Key involves accessing the API Management section within the specific Zscaler Admin Portal you are using. The exact navigation path and some options might differ slightly depending on the Zscaler product. Consult the Zscaler Help Portal for the specific product you are using.
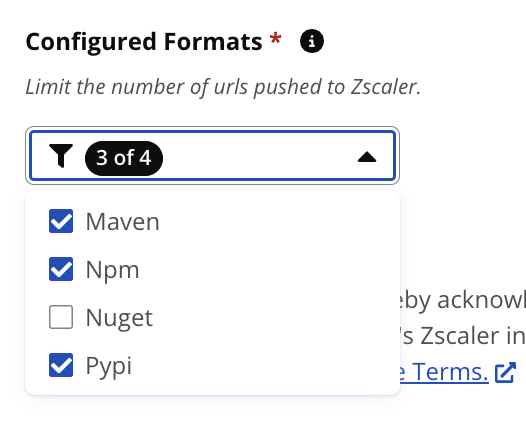
Configured Formats
Set the formats to be covered with Zscaler. Included formats use more available Zscaler custom URLs.
Trigger an Update to Zscaler
There is up to a 24-hour delay when configuring ZScaler before data is sent to the service. You may trigger the service to update immediately using the API.
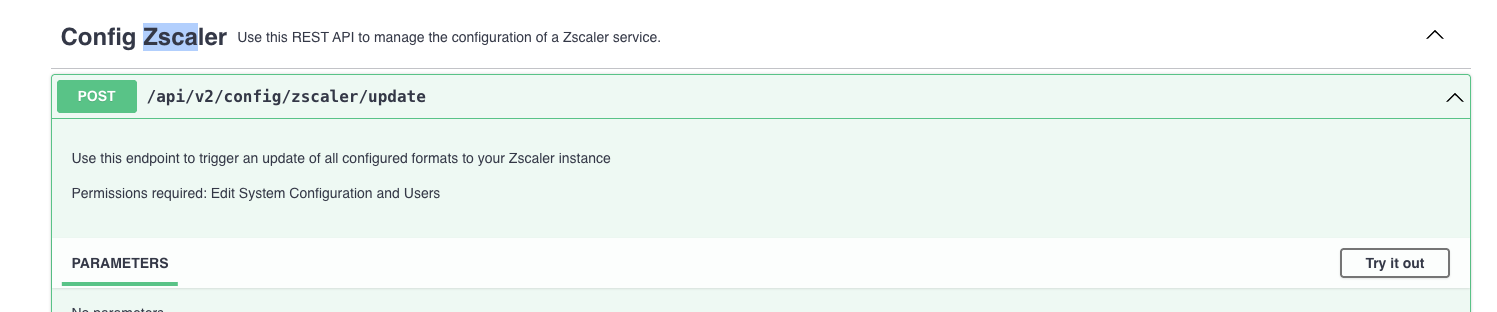
POST /api/v2/config/zscaler/update
Zscaler Custom URLs
The Zscaler integration uses custom URLs to restrict access to the active verified malware components covered by your configured formats. These are added as User Defined categories under the Zia Administrator → Resources → URL Categories with the following naming:
sonatype-{format}-shadow-download-defenseZscaler has limits on custom URLs for performance, scalability, and manageability of its security service. These limits ensure the platform can efficiently process vast amounts of internet traffic for all its users without degradation. When Zscaler does not have enough available custom URLs to catalog the known malware for a specific ecosystem, you are not fully protected.
The default limit for custom URLs/TLDs is 25K. Contact your Zscaler Account team to subscribe to up to an additional 50K custom URLs/TLDs.
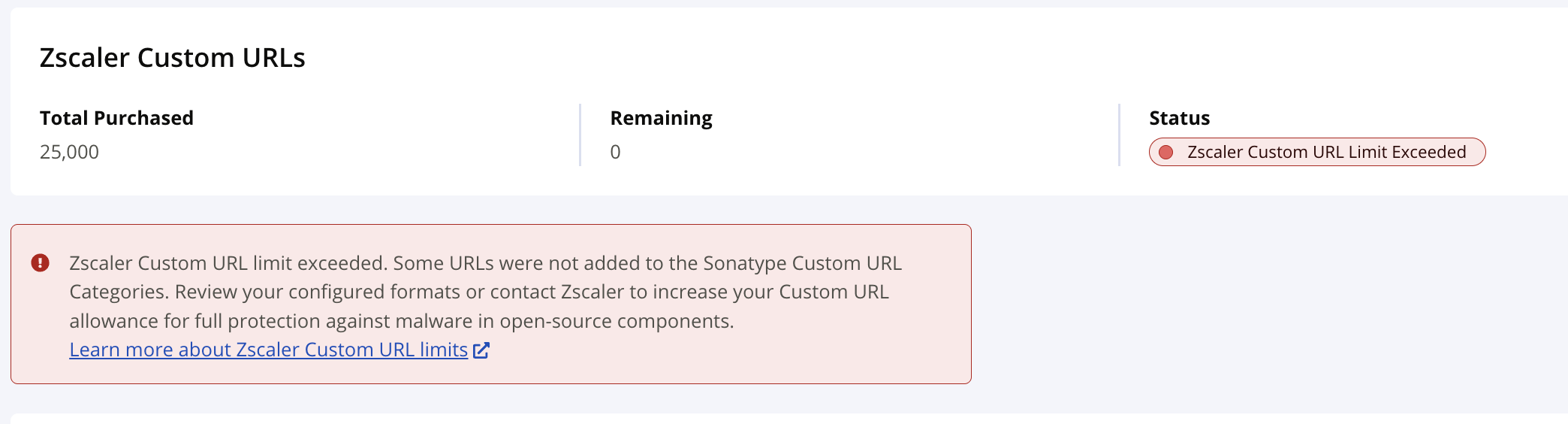
Total Purchased
The number of custom URLs allowed with your subscription.
Remaining
The number of custom URLs remaining.
Status
The status of the Repository Firewall integration.
Not Configured → The integration has not yet been configured and verified.
OSS Malware Catalog Synced → Zscaler is configured and malicious urls are under the current limit.
Zscaler Custom URL Limit Exceeded → The limit is reached and there are more malicious urls to push.
FAQ
The Zscaler integration is supported for the following formats for automatic Malware detection:
maven, npm, PyPi, nuget
Repository Firewall create custom User Define URL categories by component format. These endpoints are updated once daily.