SBOM Manager Advanced Search View
Use the SBOM Search to understand where components and vulnerabilities exist across your catalog of SBOMs directly from the UI. Export the results to build reports to share anywhere you need them.
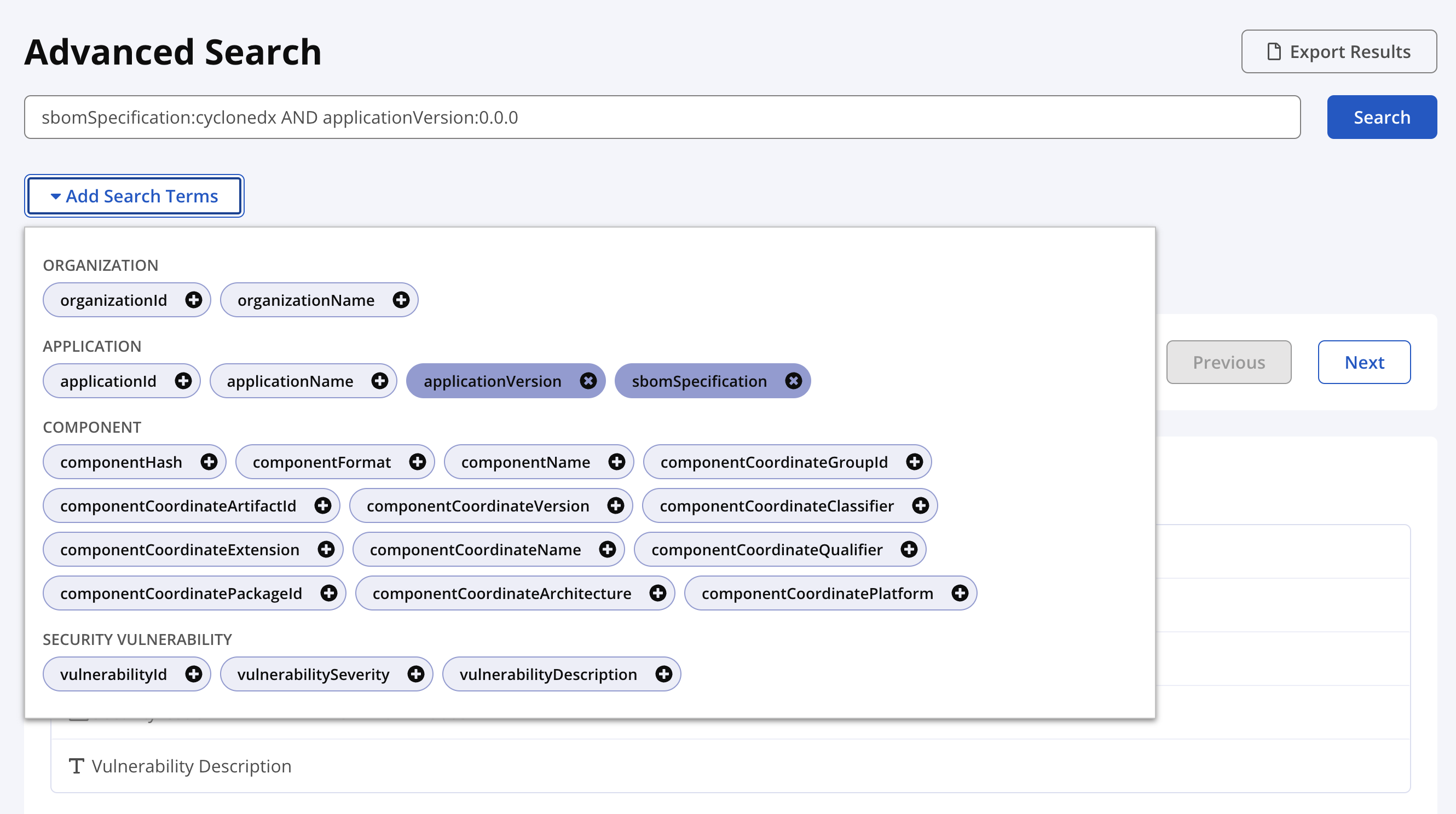
Advanced Search
Advanced Search helps you find configuration and component details through the Lifecycle, Developer, or SBOM Manager UI.
Repository Firewall
The Advanced Search does not provide results for Repository Firewall components. Use the Firewall Dashboard to search for quarantined components.
To script searches for Repository Firewall, use Firewall REST API.
Sonatype Lifecycle
The Advanced Search does not return policy violations. Use the Lifecycle Dashboard to search policy violations.
To script advanced searches for Lifecycle, use Advanced Search REST API.
Advanced Search is enabled by default, and the search index is created automatically. However, System Administrators can manually re-create the index from the System Preferences menu. To do so, complete the following steps:
Select the System Preferences icon (gear icon) from the top-navigation menu.
Select Advanced Search from the drop-down list.
Ensure that the Enabled checkbox in the Advanced Search Status field remains checked.
Select the Re-Index button to trigger the re-index operation.
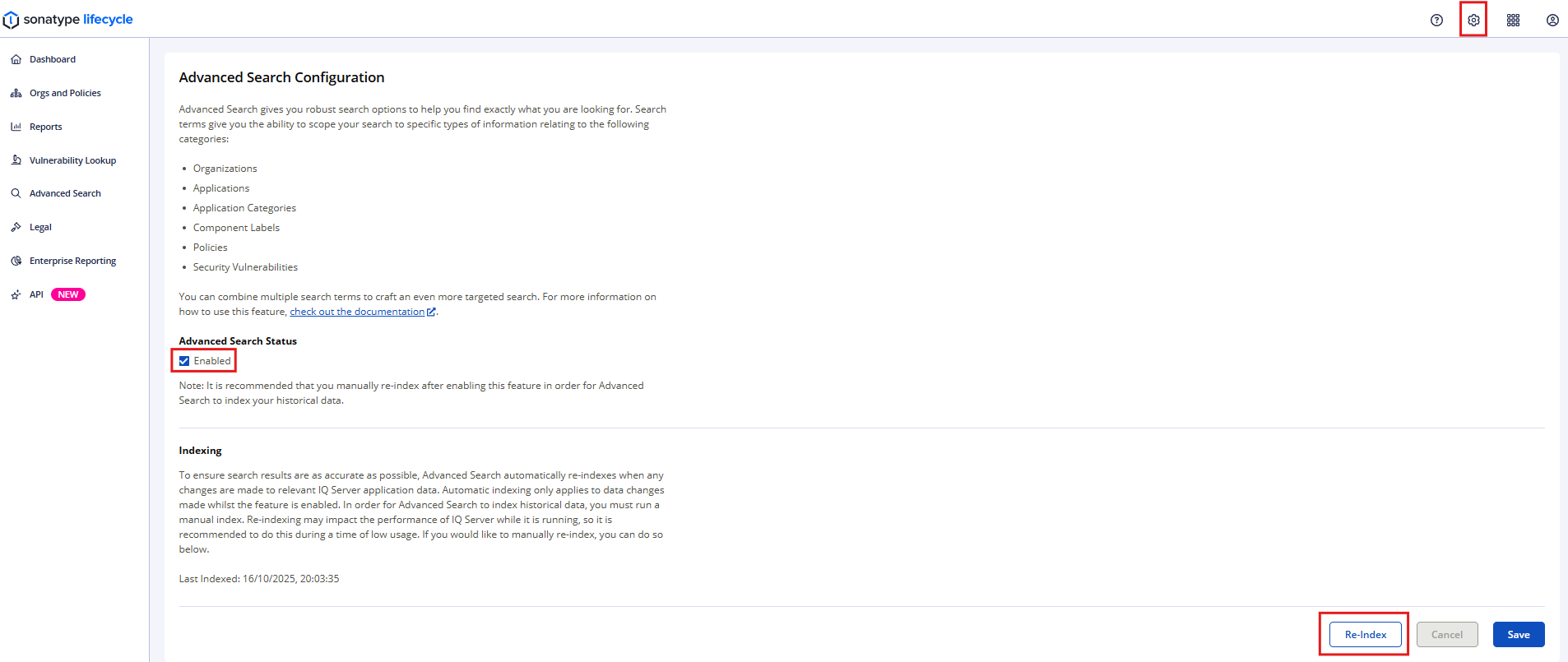
The Last Indexed date and timestamp will update when re-indexing is complete.
Performing a Search
Advanced Search lets you build precise queries by combining multiple search terms with the supported syntax. Use Query Builder for guided rules or type directly in the search box to find organizations, applications, components, or vulnerabilities by name or ID.
The Advanced Search page has two built-in ways to construct queries:
Query Builder
Add Search Terms
Query Builder
Query Builder guides you to add rules to build a query. You can add multiple rules through Add Search Item and join them with AND or OR logical operators. Each rule has the following fields:
Select Field: Filter by specific attributes such as Organization Name, Application Name, Application Category ID, and Component Hash.
Partial / Exact Match: Specify if you would like only exact matches or to include partial matches in your results.
Enter Value: Provide the string of text for which to search.
To build a query using Query Builder, take the following steps:
Select Use Query Builder to access the Build Query Rules screen.
Select the required attribute from the Field dropdown list (for example, Organization Name, Application Name, Application Category ID, Component Hash).
Select either Partial Match or Exact Match from the Match Type dropdown list. The Partial Match option wraps multi-word values in quotes and appends a wildcard.
Example: typing
testbecomesorganizationName:"test"*in the search box.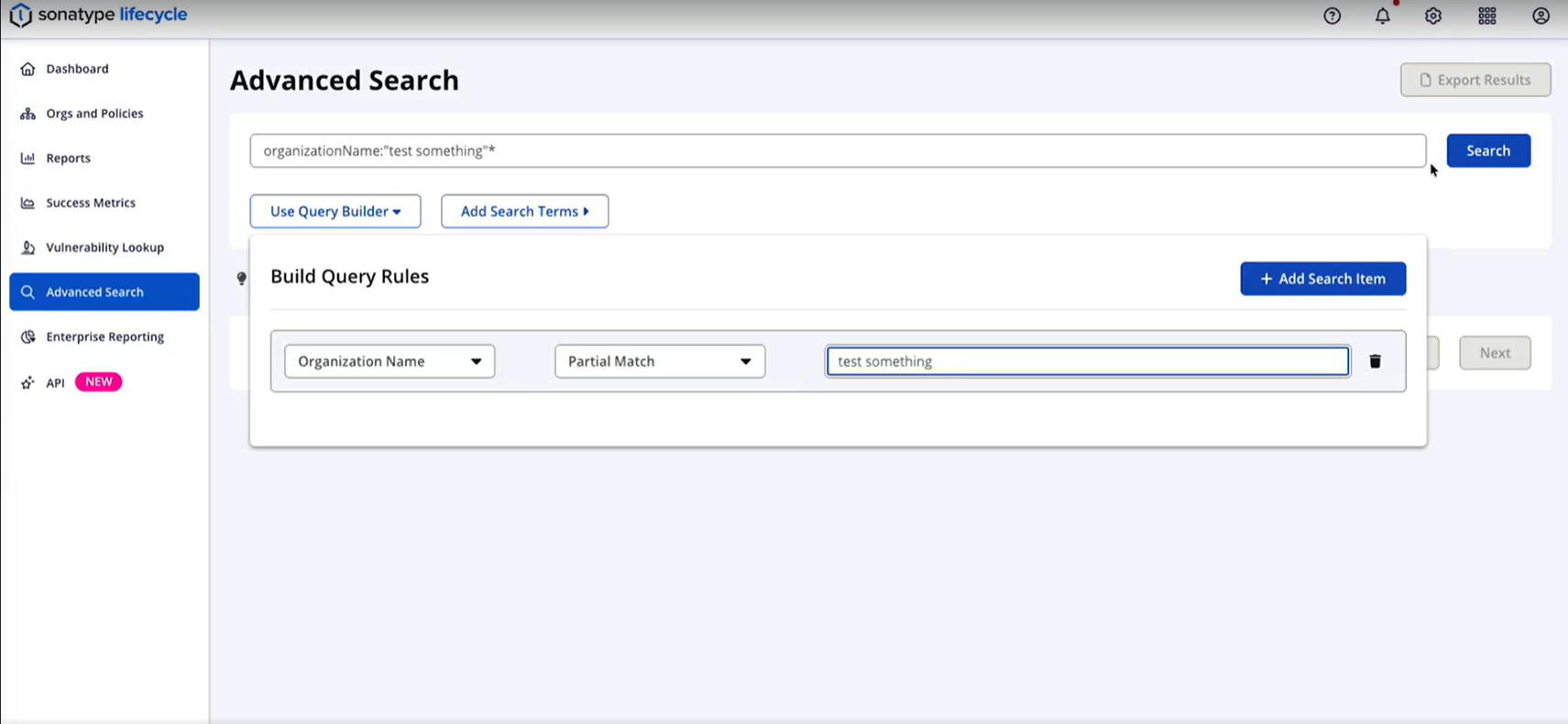
If you wish to add another rule, select Add Search Item and repeat steps 2-3.
Join the rules using AND or OR logical operator.
Select Search to perform the search.
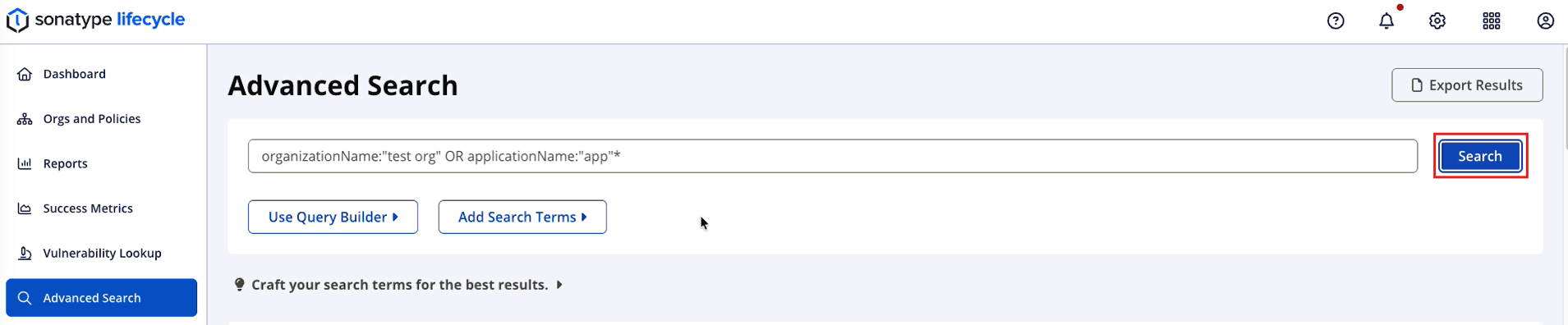
Review results and use Previous or Next to move between the pages.
Note
Use either Query Builder or manual editing for a single query. Combining them together can yield unexpected results.
Detailed examples of queries that return certain results are available directly in the Advanced Search UI as an expandable tip labelled Craft your search terms for the best results.
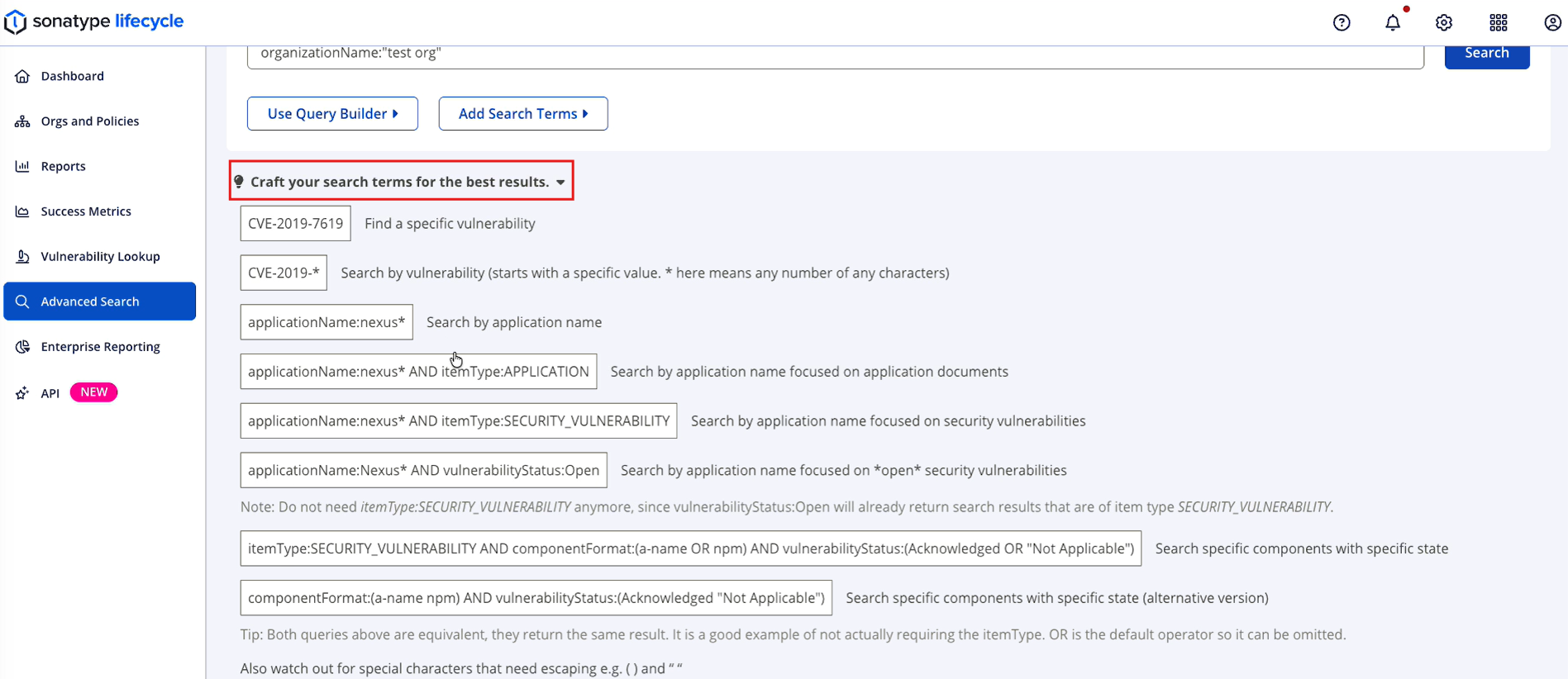
Add Search Terms
Selecting the Add Search Terms option opens a list of pre-formatted search query options (e.g., applicationId for searching on application ID, applicationName for searching on application name, etc.). Selecting a term inserts it as a properly formatted query field within the main Search box.
To use the Add Search Terms option, take the following steps:
Select Add Search Terms.
Select your desired search terms (e.g., organizationId, applicationId, etc.) from the list of options.
Properly formatted field tokens appear in the Search box as you select your desired terms. Enter values for each term after the colon to complete it.
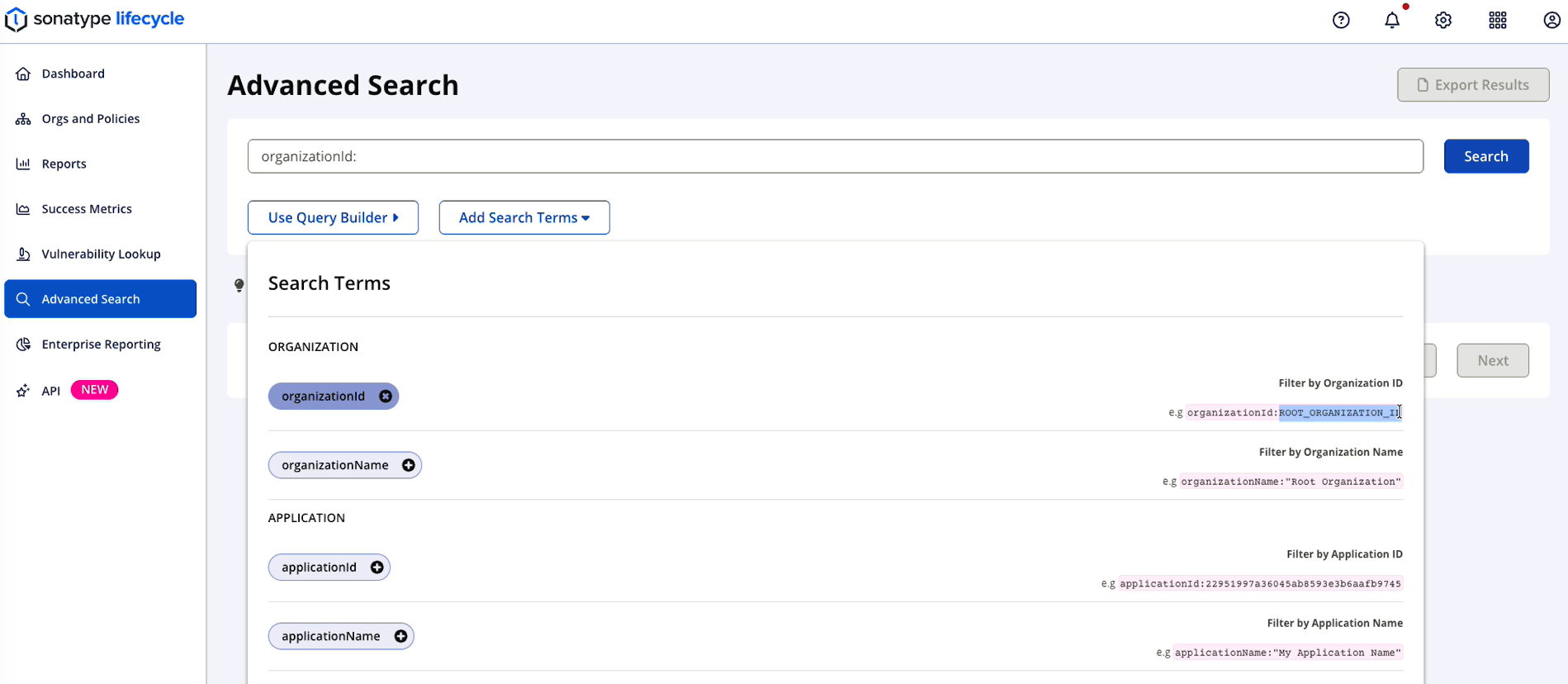
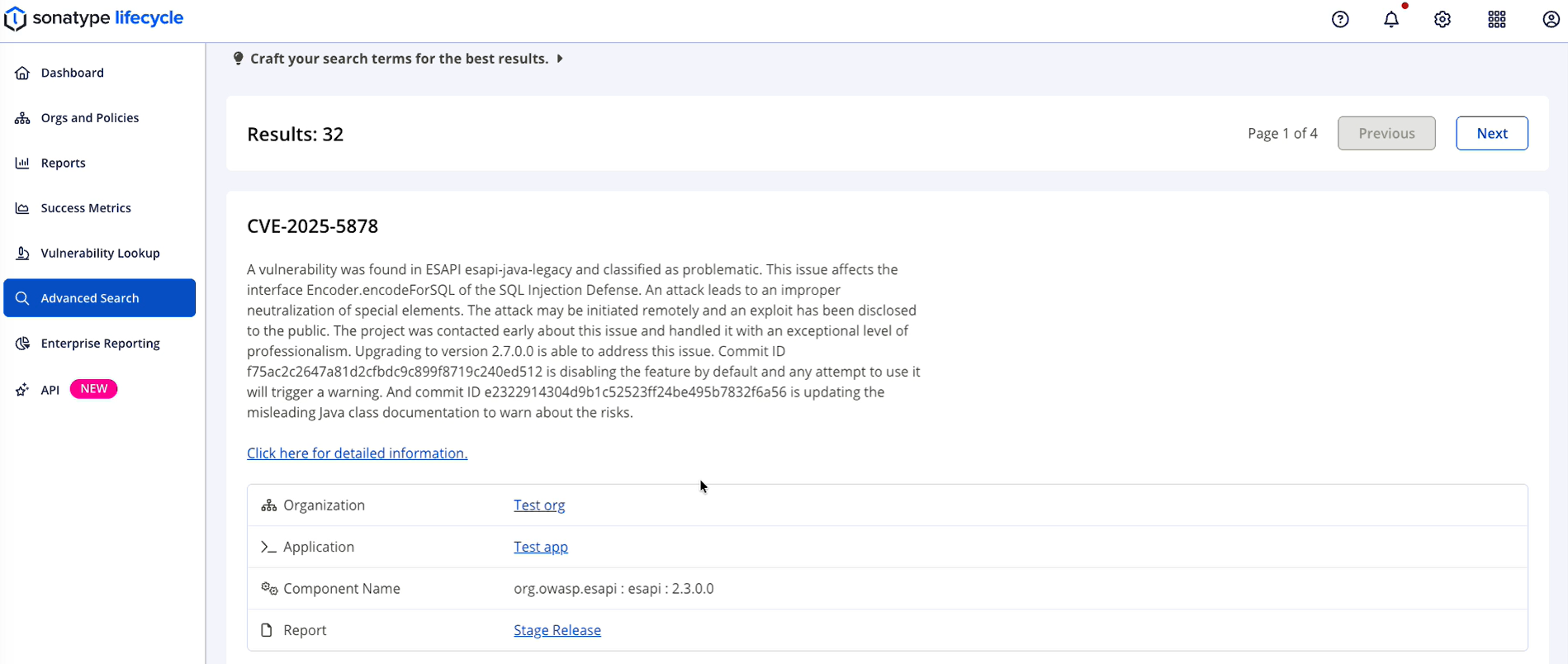
A list of results displays under your query.
Automatic Re-indexing
The Advanced Search automatically re-indexes when changes are made to the data. Automatic indexing only applies to data changes made while the feature is enabled.
Search Performance
Advanced Search retrieves results from large data sets. To limit risk to server performance, it enforces limits to the query results. You will see an error message asking you to narrow your search with additional filters.
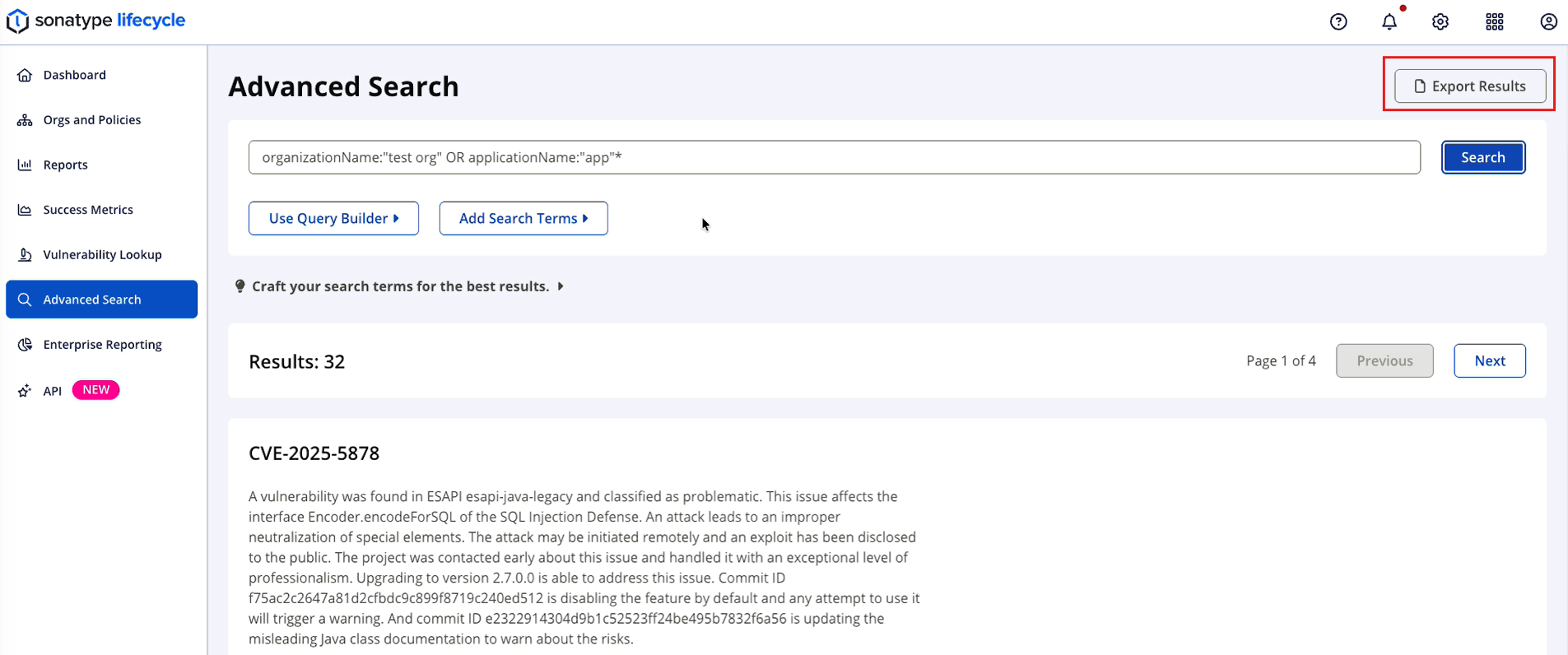
Exporting Advanced Search Results
You may export search results by selecting the Export Results button from the Advanced Search page. The search results are downloaded in a CSV file.
You can also export search results with the Advanced Search REST API.
Advanced Search Limitations
The Advance Search does not list all vulnerabilities known to Sonatype. The complete list of vulnerabilities are stored in Sonatype's proprietary data and is used during application analysis.
Refer to the tables below for search item types and examples when building a search query.
Field Name | Example |
|---|---|
organizationId | organizationId:ROOT_ORGANIZATION_ID |
organizationName | organizationName:"Root Organization" |
Field Name | Example |
|---|---|
applicationId | applicationId:22951997a36045ab8593e3b6aafb9745 |
applicationName | applicationName:"My Application Name" |
applicationPublicId | applicationPublicId:MyApplicationPublicId |
applicationVersion | applicationVersion:1.0 |
sbomSpecifications | sbomSpecifications:CycloneDx |
Field Name | Example |
|---|---|
applicationCategoryId | applicationCategoryId:319cde35ef9749f4ab99a6473ad10b74 |
applicationCategoryName | applicationCategoryName:Distributed |
applicationCategoryColor | applicationCategoryColor:yellow |
applicationCategoryDescription | applicationCategoryDescription:"outside the company" |
Field Name | Example |
|---|---|
componentHash | componentHash:f5149f0aaf01daf4bb2f |
componentFormat | componentFormat:maven |
componentName | componentName:"javax.mail : mailapi : 1.4.2" |
componentCoordinateGroupId | componentCoordinateGroupId:commons-fileupload |
componentCoordinateArtifactId | componentCoordinateArtifactId:mailapi |
componentCoordinateVersion | componentCoordinateVersion:1.2.16 |
componentCoordinateClassifier | componentCoordinateClassifier:dist |
componentCoordinateExtension | componentCoordinateExtension:jar |
componentCoordinateName | componentCoordinateName:"org.webjars bootstrap" |
componentCoordinateQualifier | componentCoordinateQualifier:cp37-cp37m-win32 |
componentCoordinatePackageId | componentCoordinatePackageId:loadash |
componentCoordinateArchitecture | componentCoordinateArchitecture:x86_64 |
componentCoordinatePlatform | componentCoordinatePlatform:ruby |
Field Name | Example |
|---|---|
componentLabelId | componentLabelId:0d3f4015332e4b298ac1ed95c12ff3a3 |
componentLabelName | componentLabelName:Architecture-Cleanup |
componentLabelColor | componentLabelColor:orange |
componentLabelDescription | componentLabelDescription:"relics of a build" |
Field Name | Example |
|---|---|
policyId | policyId:b4ca64a8b8264f03b65127016859b2a2 |
policyName | policyName:Component-Unknown |
policyThreatCategory | policyThreatCategory:security |
policyThreatLevel | policyThreatLevel:10 |
Field Name | Example |
|---|---|
reportId | reportId:a6860277aa844ab5af8bfef041f7e6e5 |
policyEvaluationStage | policyEvaluationStage:Build |
vulnerabilityId | vulnerabilityId:CVE-2014-3625 |
vulnerabilityStatus | vulnerabilityStatus:Open |
vulnerabilitySeverity | vulnerabilitySeverity:7.1 |
vulnerabilityDescription | vulnerabilityDescription:"directory traversal" |