Success Metrics Enterprise Dashboard
About the Data
Data Refresh Frequency: Updated daily at 7:00 am (UTC -05:00)
Displays Data for: For new installations, data will be visible after a week of scanning with version 184.
Minimum Requirements: Applications must be scanned at least once after upgrade to version 184. The dashboard currently shows data related to violations and remediations that are discovered after upgrade to version 184.
Overview
Sonatype Lifecycle collaborates with your teams to keep help mitigate the security, compliance, and quality threats to your DevSecOps pipelines. By utilizing the policy violation workflows, your teams can evaluate applications, remediate vulnerabilities or apply waivers to effectively prioritize and optimize and streamline development process. This approach ensures the delivery of secure and compliant releases within a reasonable time-frame.
The Success Metrics dashboard helps pinpoint areas of improvement within your DevSecOps teams, fostering greater synergy with Sonatype Lifecycle.
The Success Metrics dashboard provides:
Remediation overview for policy violations
Applications onboarded and scanned
Number of policy violations reported
Risk Ratio
Number of policy violations for each policy type and threat level
Detailed information on components and applications implicated by policy violations
The Success Metrics dashboard can lead to identify areas of improvement within your devSecOps teams leading to a greater synergy with Sonatype Lifecycle.
Get to Know Your Success Metrics Dashboard
The interactive dashboard provides multiple filter options to view the success metrics for your organization. You can filter on date range, organization name, application name, application category, policy threat level, policy type (Security, Quality, License, and Other), a specific DevSecOps stage and component type (format/ecosystem).
Stages available for filtering are release, stage-release, build, compliance and source. The build stage is selected by default.
NOTE: Lifecycle instances with over thousand applications may take longer to load.
Remediation Overview
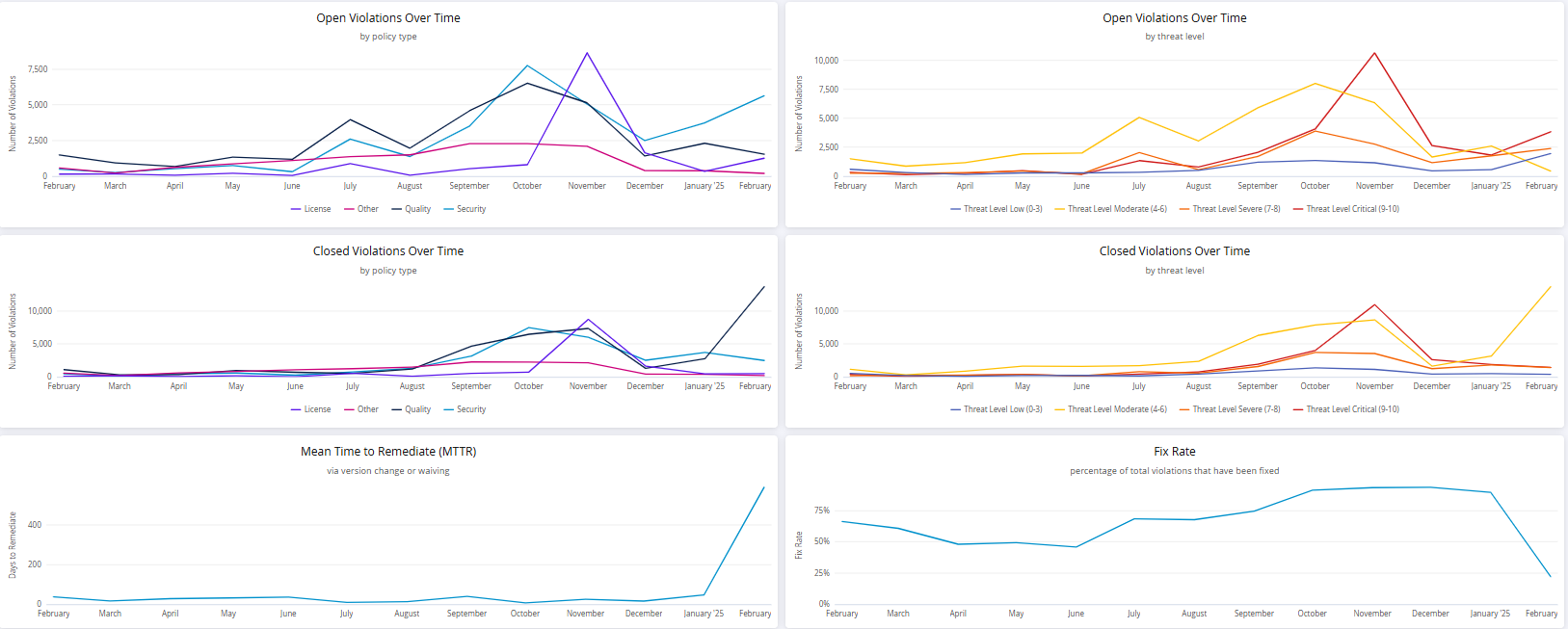
The Remediation Overview chart displays the number of open violations, closed violations and the Mean Time to Remediate (MTTR) for aggregated by policy types and threat levels and the Fix Rate.
The policy types displayed here include Security, Quality, License and Other. Click on the policy type labels (below the X-axis) to select/de-select the corresponding trend line on the chart.
The threat levels displayed here include Low (0-3), Moderate (4-6), Severe (7-8), and Critical (9-10). Click on the threat level labels to select/de-select the corresponding trend line on the chart.
The Fix Rate chart displays the percentage of violations resolved during the selected time period. Fixing violations includes changing the component versions (by upgrading, downgrading, removing the component or fixing the vulnerability.)
Drill Down for a Deeper Analysis
Click on any point on the trend lines to drill-down by a week-wise or day-wise chart.
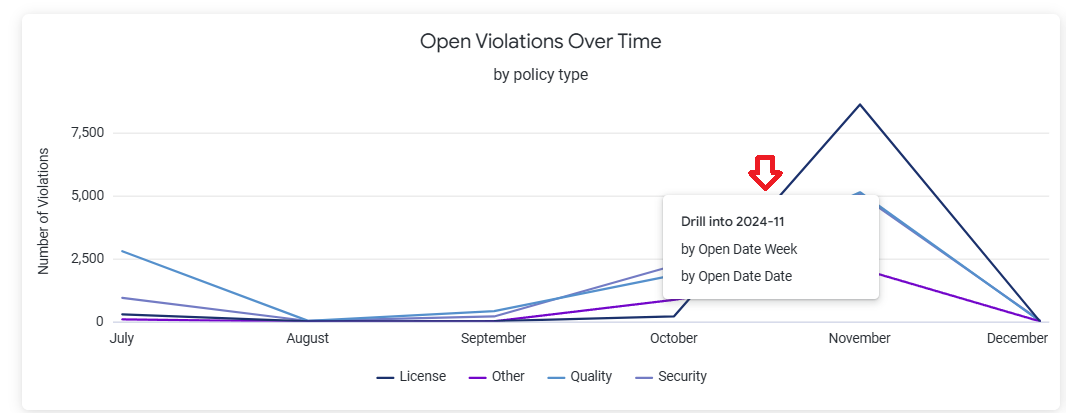
The drill-down view offers a deeper analysis of open violations over the selected time period, for each threat level as shown below. You can select Table from the top to view the results in a tabular format, instead of the chart.
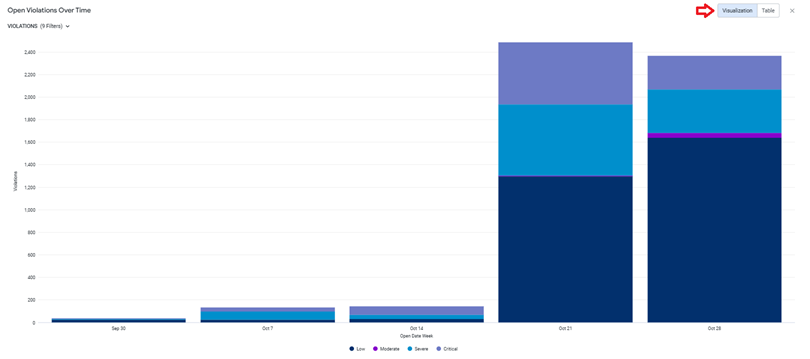
Remediation Status for Critical and Other Violations
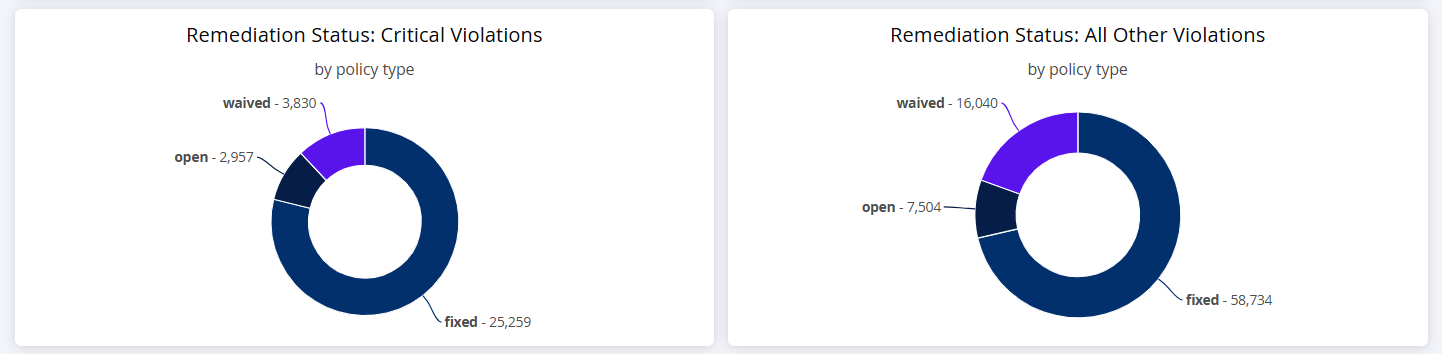
Remediation Status: Critical Violations chart shows a breakdown of the number of critical violations remediated (by upgrading, downgrading, removing the component or fixing the vulnerability), or applying waivers.
Remediation Status: All Other Violations chart shows a breakdown of the number of all other violations (excluding criticals) remediated by changing the component fixed violations or applying waivers.
Apps & Scans
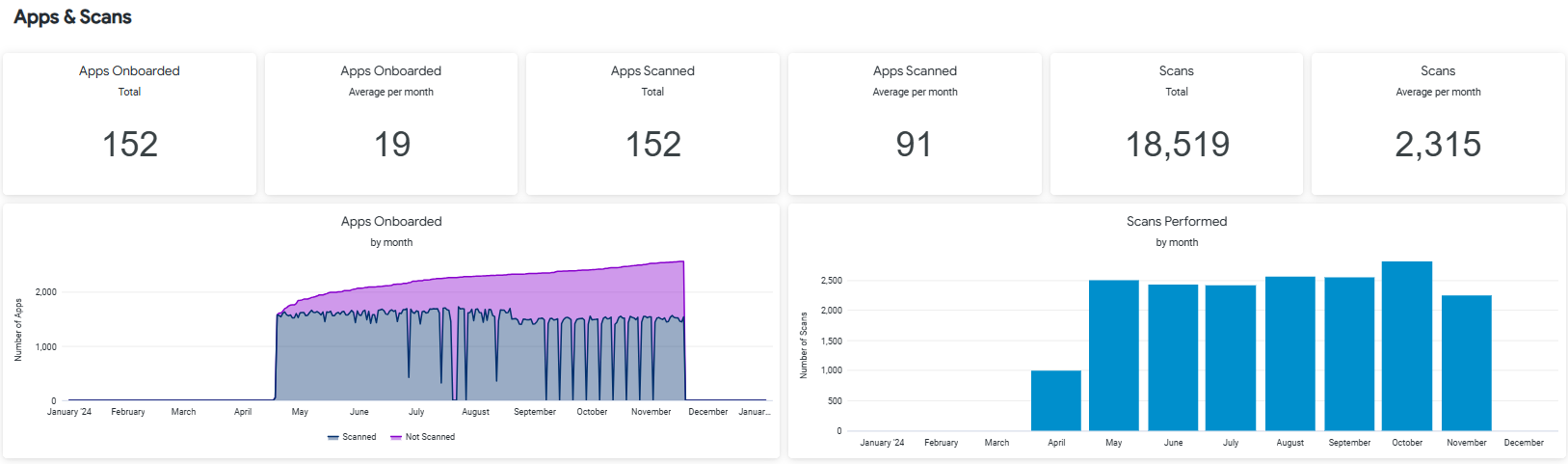
The Component filter does not apply to the visualizations in the Apps and Scans section.
Are Your Applications Being Scanned at Required Stages?
By selecting a specific stage in the Stage filter, you can ensure that most of your applications are being scanned at that stage.
Violations Overview
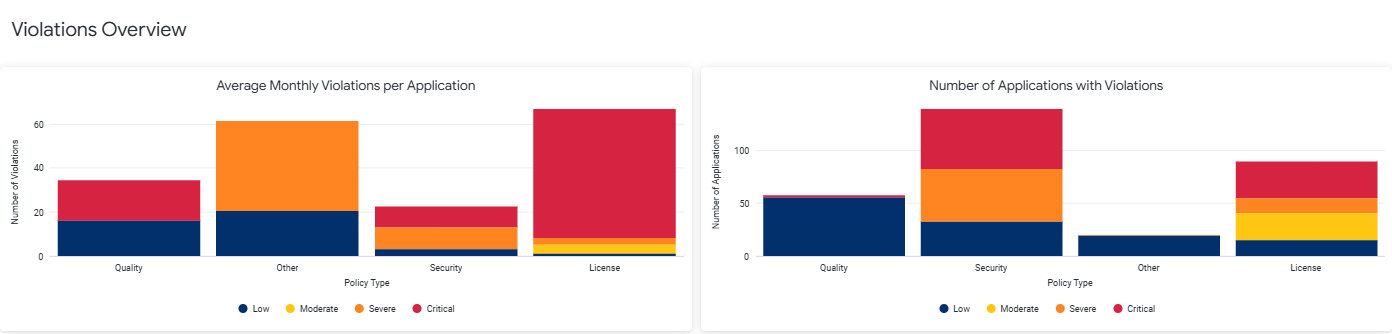
This section indicates the magnitude of policy violations aggregated at the application level.
The charts display a summary of average monthly violations and threat levels (Low, Moderate, Severe, and Critical) per application and the number of applications with violations for each policy type, i.e. Security, License, Quality and Other.
Risk Ratio
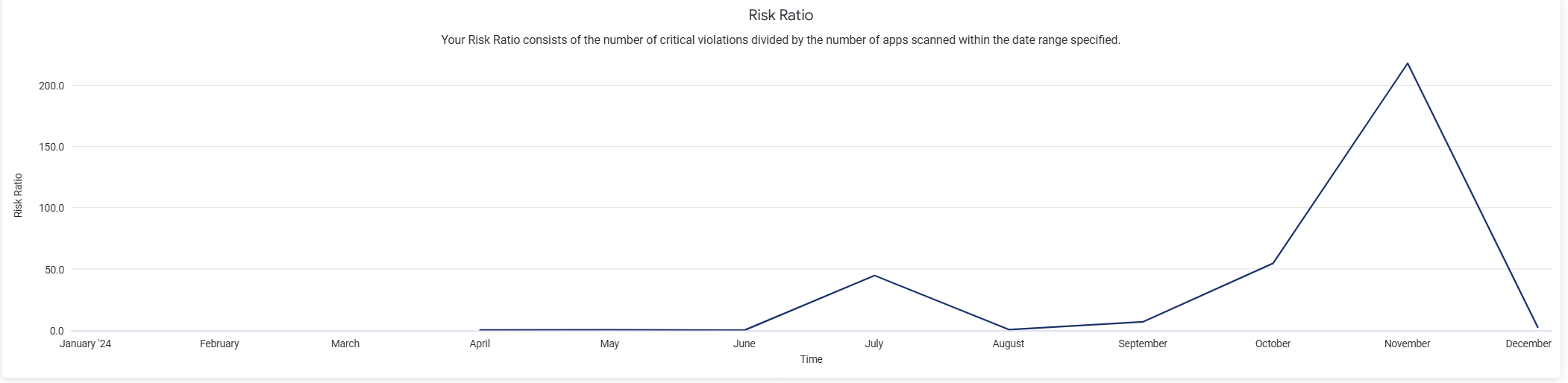
The Risk Ratio is a ratio of the number of critical violations to the number of applications scanned in the date range selected in the filter.
Is Risk Ratio High?
A prolonged high risk ratio is not a good indicator of your security posture and may need intensive remediation efforts. However, a spike may just be an indicator that a critical violation that could have occurred due to a specific component, was fixed promptly by your team.
Drill Down for a Deeper Analysis
Click on any point on the trend lines to drill-down by a week-wise or day-wise chart.
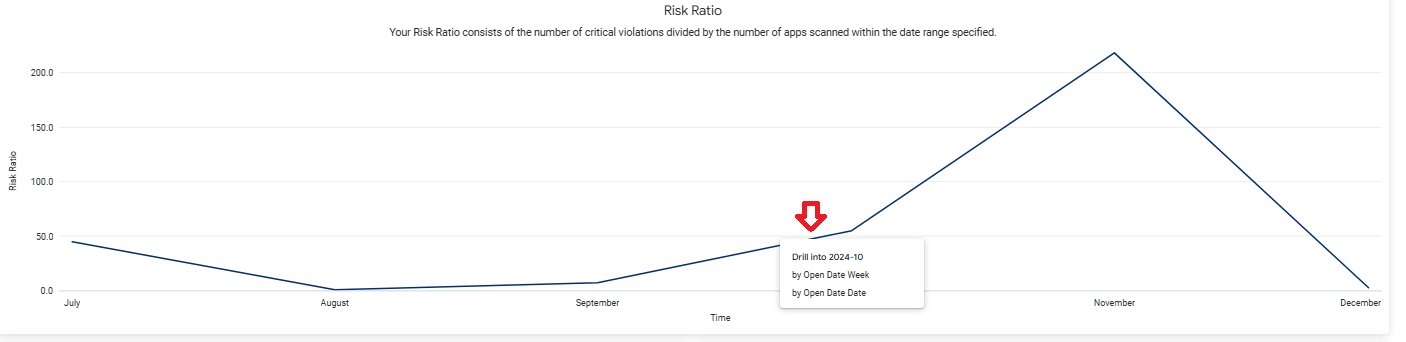
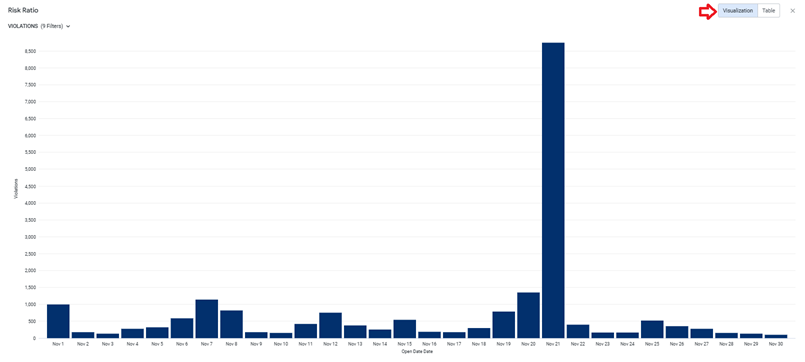
The drill-down view offers a deeper analysis of the risk ratio over the selected time period, for each threat level as shown below. You can select Table from the top to view the results in a tabular format, instead of the chart.
Violations Discovered
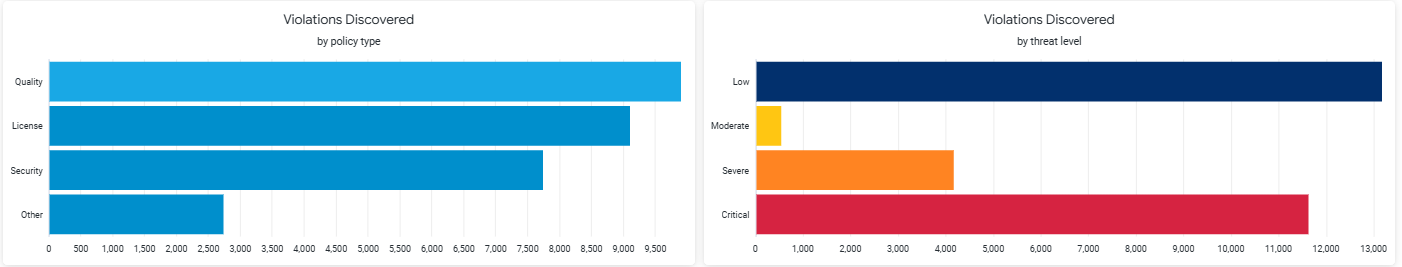
This section shows all discovered violations that match the criteria specified in the filter.
The charts show violations aggregated by policy types (Security, Quality, License and Other) and threat levels (Critical, Severe, Moderate, and Low).
Components
The Component Information Table
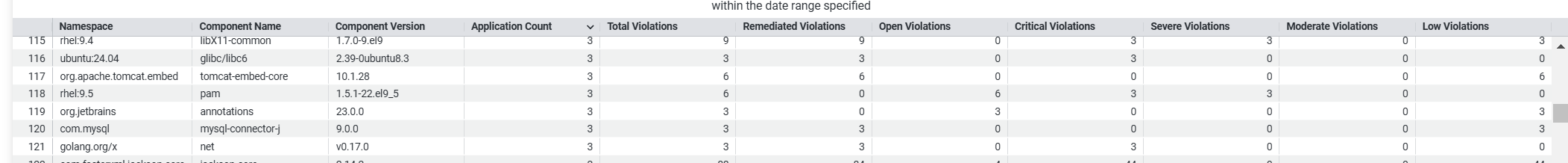
The component information table contains all components that have been implicated with a violation during the application scans that match the criteria specified in the filter.
Table column | Description |
|---|---|
Namespace | The namespace to which the component belongs |
Component Name | Name of the component causing the violation |
Component Version | Version of the component |
Application Count | Number of applications impacted |
Remediated violations | Number of violations remediated for the component |
Open Violation | Number of violations not remediated for the component |
Critical Violations | Number of violations with threat level "critical" (9-10) |
Severe Violations | Number of violations with threat level "severe" (7-8) |
Moderate Violations | Number of violations with threat level "moderate" (4-6) |
Low Violations | Number of violations with threat level "low" (0-3) |
The Application Information Table

Table column | Description |
|---|---|
Application | Name of the application containing the policy violation |
Component Count | Total number of components found in the application |
Total Violation | Total number of violations found in the application |
Total Remediated | Number of violations in the application that are remediated |
Open Violations | Number of components pending remediation in the application |
Critical Violations | Number of violations in the application with threat level "critical" (9-10) |
Severe violations | Number of violations in the application with threat level "severe" (7-8) |
Moderate violations | Number of violations in the application with threat level "moderate" (4-6) |
Low violations | Number of violations in the application with threat level "low" (0-3) |
Troubleshooting
Problem
Clicking on the browser Refresh button may give you the following error:
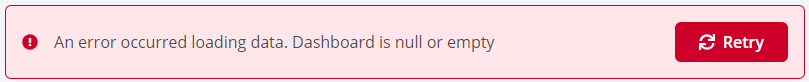
Solution
Click the Back button on your browser, from the page where you see this error, to go back to the Landing page Enterprise Reporting. Select the dashboard you want to view, to reload the visualizations.
To refresh the page, click on the refresh icon on the top right, instead of the Refresh button on your browser.
Problem
No data visible on the dashboard or any other issues with the dashboard.
Solution
Click on Copy to Support Info to Clipboard button and contact support with this information.