Custom Vulnerability Attributes
The security team may augment vulnerability data provided by Sonatype products using custom vulnerability attributes. They may customize the details and attributes of a vulnerability to aid developers in remediation and prioritization.
Modify the severity score to align with your applications temporal or environmental states.
Provide research done on a vulnerability and custom remediation instructions for your developers
Use custom CWE-ID as a policy constraints to enforce remediation or development practices
Customizing the CVSS Vector String and Severity
The CVSS vector string is a combination of base metrics (reflect the exploitability, impact, and scope of the vulnerability), environmental metrics (reflect the confidentiality), integrity and availability of information systems, and temporal metrics (reflect the exploit code maturity, remediation level, and report confidence).
See the FIRST.ORG CVSS Specifications for details.
Modify the temporal metrics or environmental metrics to match the specific impact and requirements of your infrastructure
Override the base metrics with your own research
We have added the ability to add custom CVSS Vector String and Severity. Customizing this data is useful when you want to add temporal or environmental metrics to the CVSS vector string.
For instance, if your developers are using a component vulnerable to CVE-2022-22965, and you have evidence that a proof of concept exploit exists but also know there is an official fix, you can modify the CVSS vector string to reflect this data.
AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
to
AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C
The severity should then be adjusted from 9.8 to 8.8 to reflect the temporal information.
Add a new policy with a constraint on the temporal metric representing the "official fix", "RL:O", to require developers prioritize vulnerabilities with an official fix.
Customizing the Custom Remediation
Provide remediation instructions and research details to developers on a vulnerability.
For example, if your developers are using org.apache.tomcat : tomcat-catalina : 10.0.0-M3 they are susceptible to CVE-2021-24122. However, that vulnerability is only accessible if the application is serving resources from a Windows NTFS file system. As part of your custom remediation, you can instruct developers to check with an authorized individual who can validate that they are using the component on a non-Windows NTFS file systems before granting a waiver.
Similarly, the text box can be used to provide proof of research or mitigation. For instance, if your developers are using com.fasterxml.jackson.core : jackson-databind : 2.10.0 it is susceptible to CVE-2020-9548 if developers are still using the deprecated default typing methods from 2.9.x.
Within the custom remediation box the developer may show how they migrated from version 2.9.x to 2.10.0 and that they are no longer calling the deprecated methods. This is done by providing links to a Jira ticket or even links to code commits in SCM. When providing this level of detail it is recommended that changes be scoped to the application, as these details would have to be provided on a per-application basis.
Customizing the CWE-ID
The CWE-ID is a community-developed list of software and hardware weakness types. The CWE classification and taxonomy serve as a common baseline for weakness identification and remediation efforts across developer and security practitioner communities.
Learn more about CWEs at mitre.org
Customize the CWE-IDs to reflect the weakness identification and remediation efforts specifically for your development environment.
By customizing the CWE-ID you have greater control over policy enforcement. For instance, if you have a policy requiring all data query logic to be sanitized (policy constraint on CWE-ID 943) and you have developers using org.hibernate : hibernate-core : 5.4.20.Final which is vulnerable to CVE-2020-25638, you can edit the CWE-ID to also include CWE-ID 943 expanding the default category of CWE-ID 89. Conversely, you could also narrow the category of a hibernate SQL injection weakness and use CWE-ID 564 if you wanted to have policy specifically around vulnerabilities of that category.
Scopes and Application Category
Customize vulnerability attributes at any scope (ROOT, Organization, or Application) or with an application category. When adding environmental metrics to a CVSS vector string, we recommend applying those changes either on an application category (e.g. air-gapped applications might require "MAV:P" metric), or application scope.
Conversely, temporal metrics can be applied to all scopes so ROOT would be the most common choice. Confirm the applicable scope of your changes before saving the customized vulnerability attributes.
Steps to Customize Vulnerability Attributes
This feature is available to users with Edit IQ Elements permission.
1. Click on the "Customize" button to start customizing the vulnerability details. The "Custom" indicator for the vulnerability attributes in the left panel indicates whether that attribute has been customized previously.
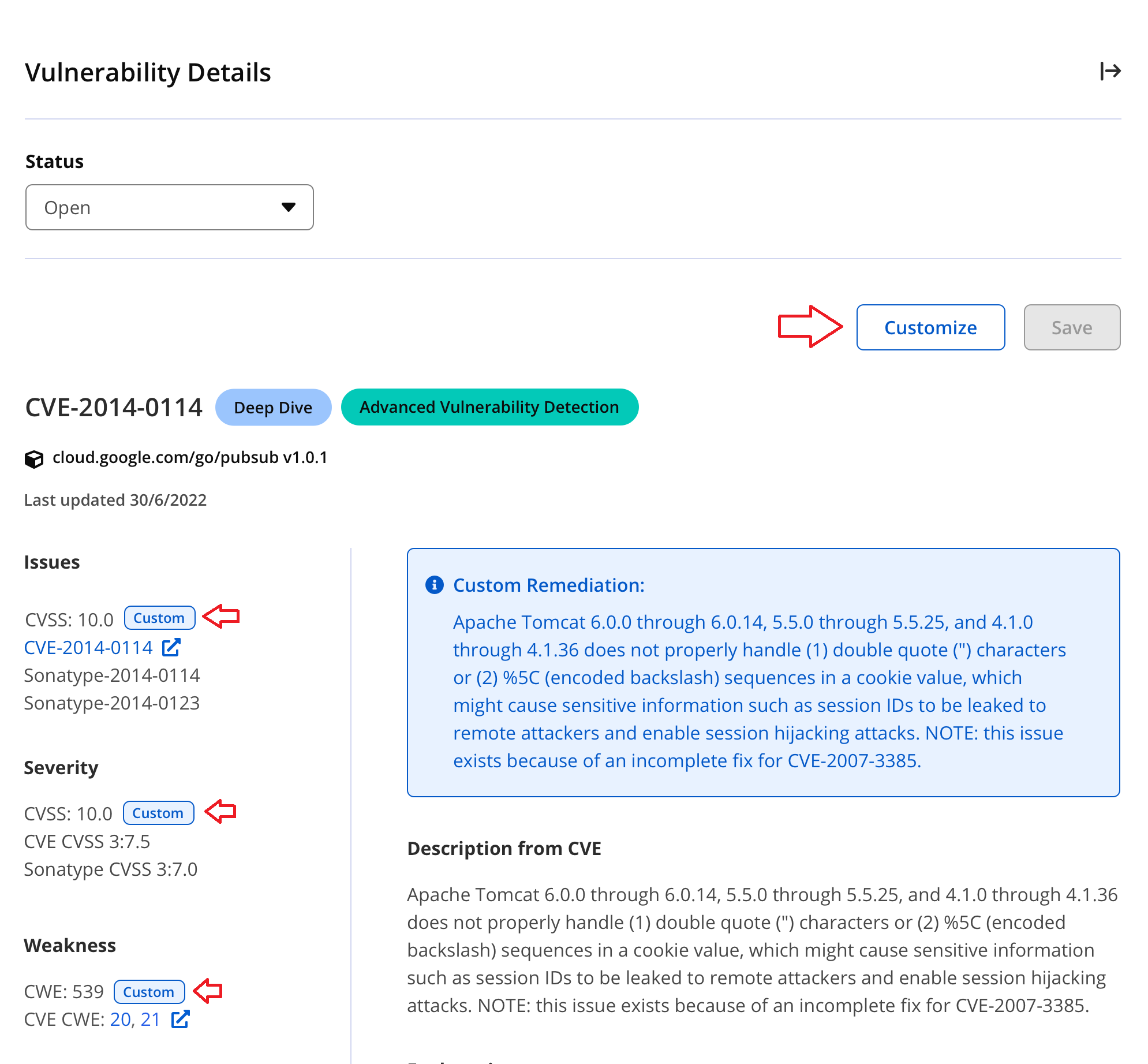 |
2. A "Edit <Vulnerability Attribute>" button on the right top section for each vulnerability attribute appears. Click on the edit button for the vulnerability attribute you want to customize.
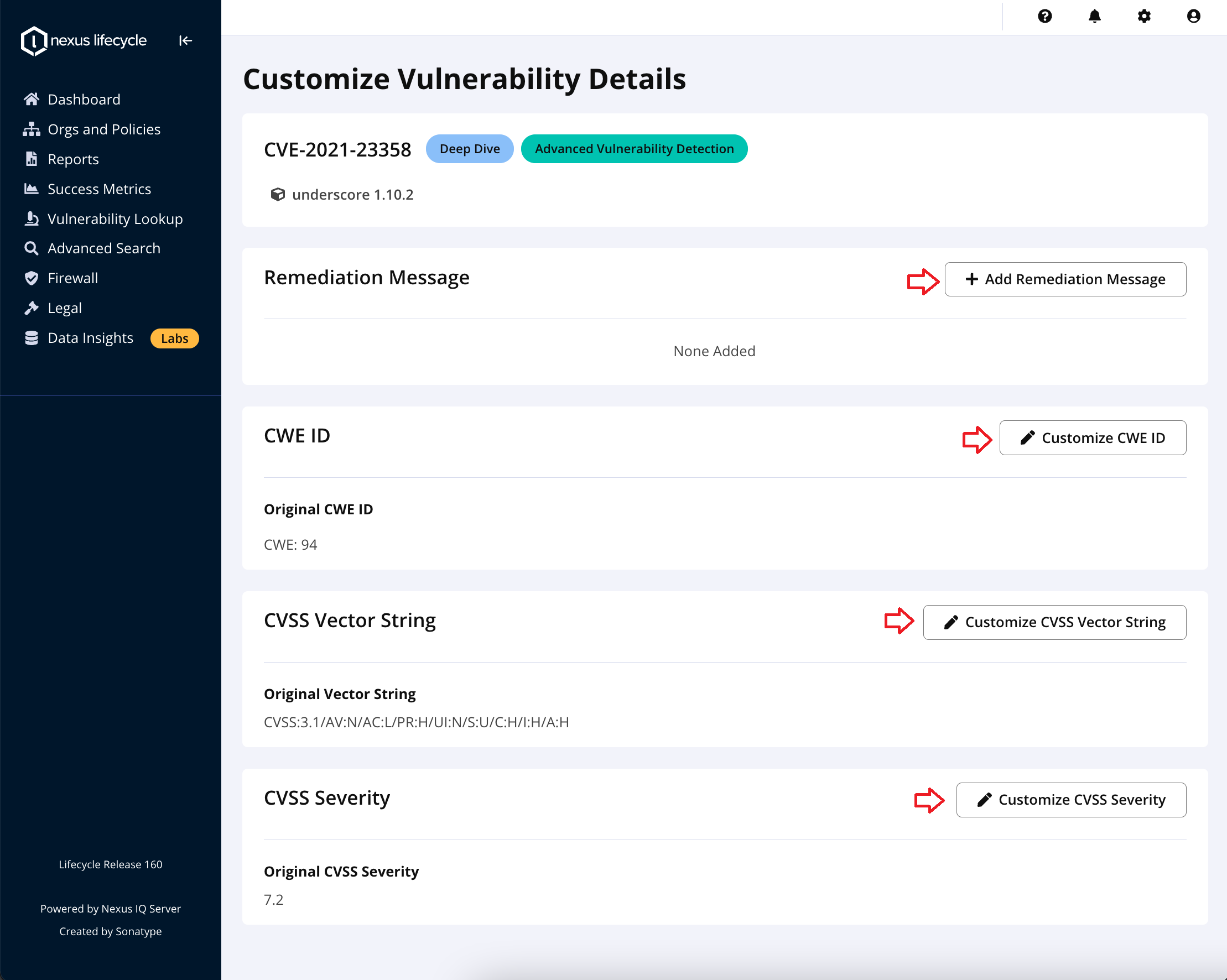 |
3. Click on the "Edit Remediation Message" to customize the remediation for this vulnerability.
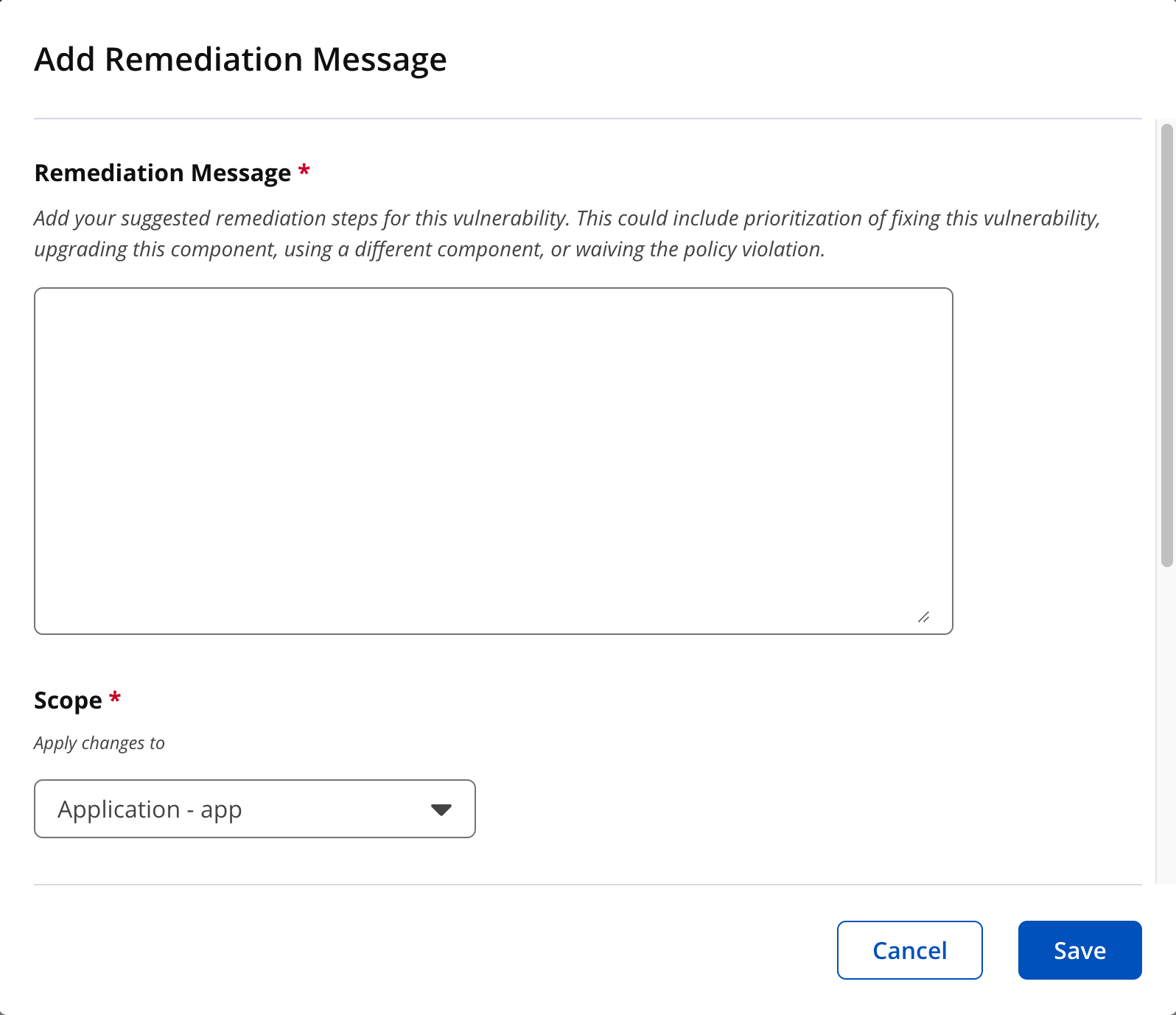 |
Enter the customized remediation message. Select the appropriate scope, i.e. root, organization or application from the dropdown. Select the application category to which this customization will be applicable. Click "Save" to complete the customization of the remediation message.
4. Click on "Customize CWE ID" to customize the vulnerability attribute CWE ID.
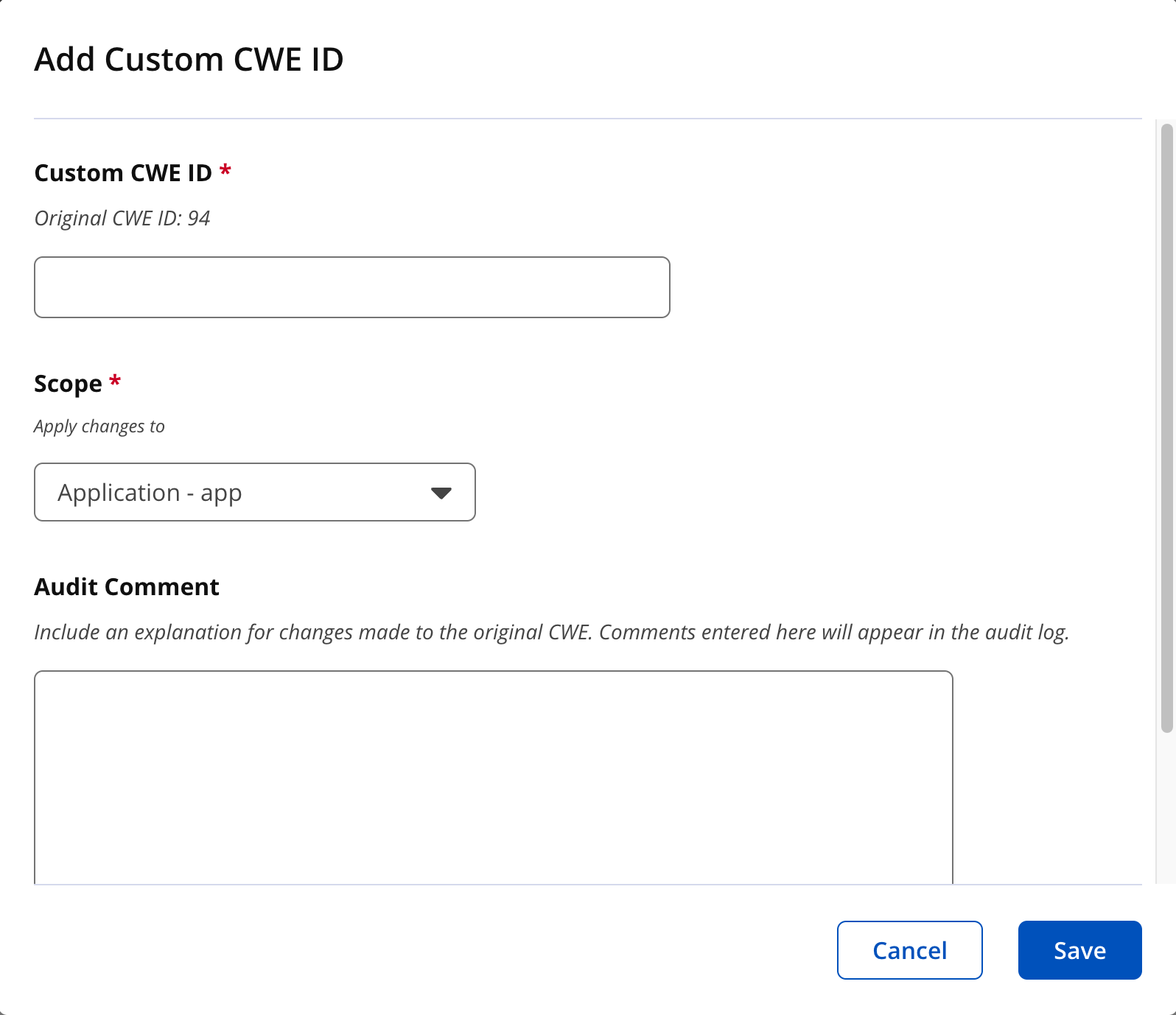 |
Enter the custom CWE ID. Select the appropriate scope, i.e. root, organization or application from the dropdown. Enter the "Audit Comments" to explain the reason for customizing this vulnerability attribute. Audit comments will appear in the audit log for traceability and accountability. Click "Save" to complete the customization.
5. Click on "Customize CVSS String " to customize the CVSS strings and severity for this vulnerability.
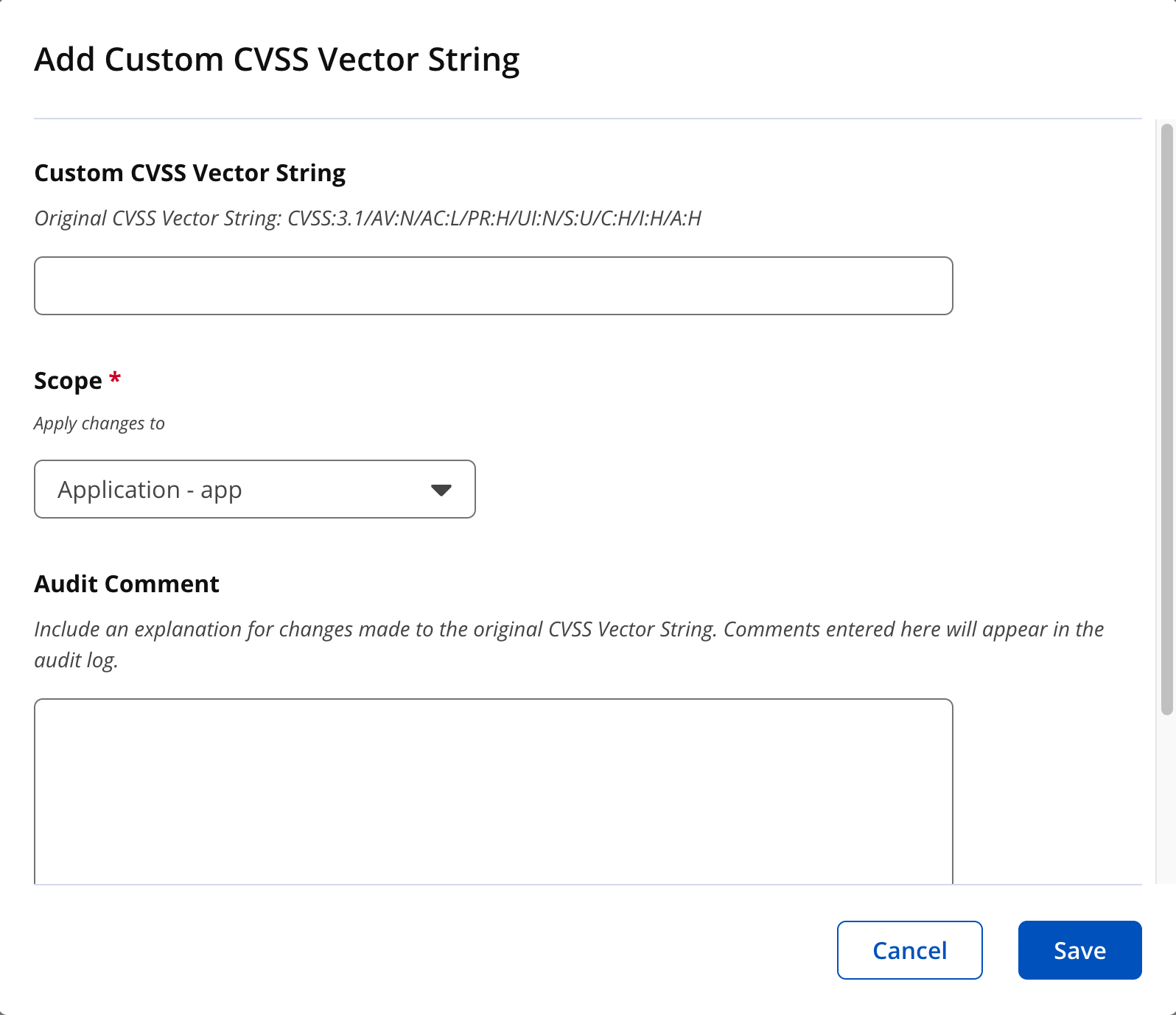 |
Enter the custom CVSS vector string. Select the appropriate scope, i.e. root, organization or application from the dropdown. Enter the "Audit Comments" to explain the reason for customizing this vulnerability attribute. Audit comments will appear in the audit log for traceability and accountability. Click "Save" to complete the customization.
6. Click on "Customize CVSS Severity" to customize the CVSS severity for this vulnerability.
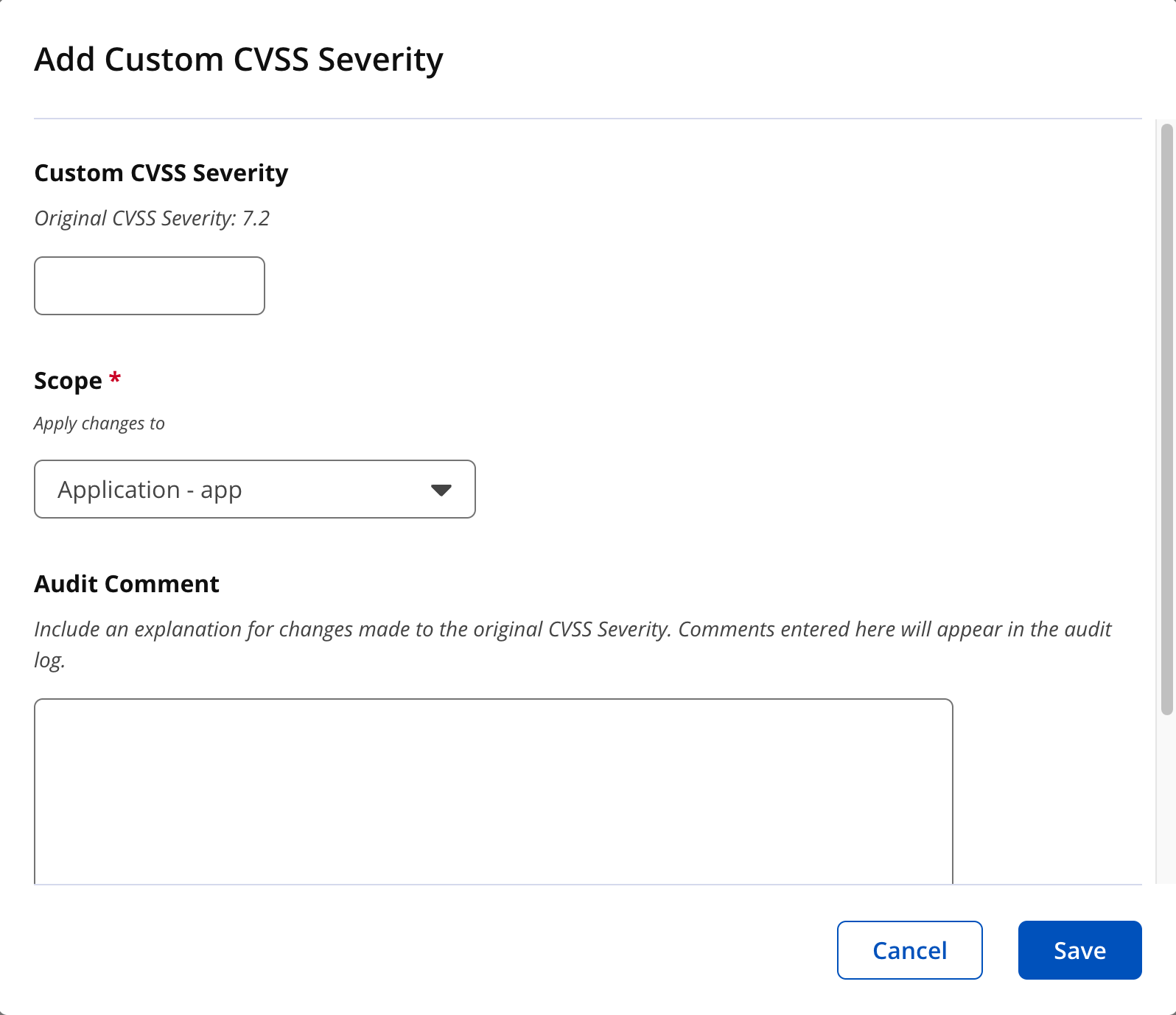 |
Enter the custom CVSS severity. Select the appropriate scope, i.e. root, organization or application from the dropdown. Enter the "Audit Comments" to explain the reason for customizing this vulnerability attribute. Audit comments will appear in the audit log for traceability and accountability. Click "Save" to complete the customization.