SBOM Component Details View
The component detail view summarizes component metadata found from the source SBOM and Sonatype data services. Use this view to verify and report risk associated with components reported in your SBOM.
Use the VEX workflow to annotate any reported and discovered vulnerabilities from within your SBOM.
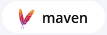
Displayed under the component name; the parent organization, application, file name, and imported date for the SBOM this component. Use the top breadcrumb to return to the bill of materials view.
Component Identifiers
Color-coded identifiers help you rapidly identify relational information about the component. A list of possible tags is provided in the table below:
Tag Icon | Definition |
|---|---|
| The public ecosystem from which the component is found |
PackageURL | A unique identifier containing the component coordinates |
 | Indicates the component is a direct dependency |
 | Indicates the component is a transitive dependency |
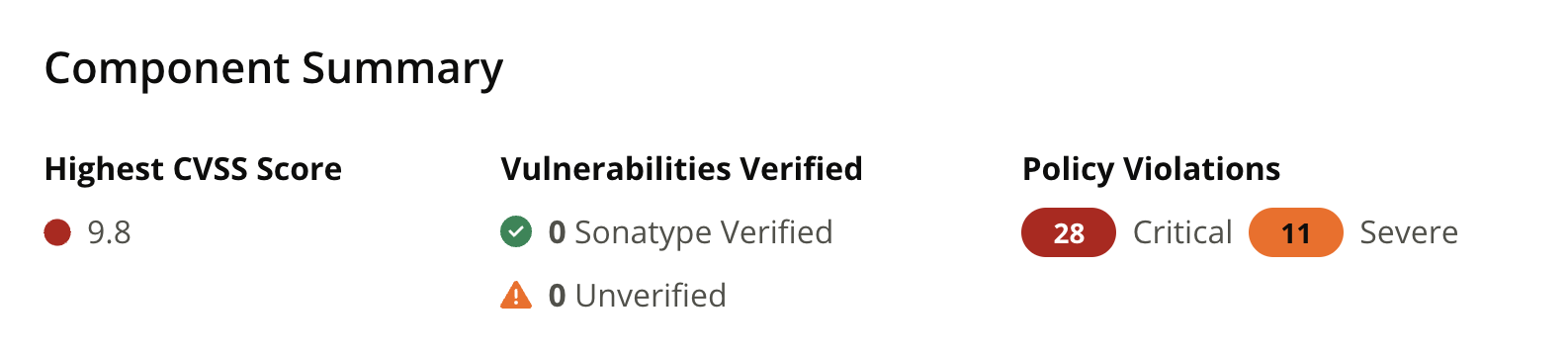
Component Summary
The component summary section provides risk analysis details for the component.
Field | Description |
|---|---|
Highest CVSS Score | Displays the score for the highest threat level security vulnerability as well as the total number of security vulnerabilities. |
Vulnerabilities Verified | The component vulnerabilities reported in the SBOM. Sonatype-verified vulnerabilities are confirmed risks associated with the component. |
Policy Violations | The total number of critical and severe policy violations on the component. |
Disclosed Vulnerabilities and Sonatype Identified Vulnerabilities
The disclosed vulnerabilities section provides a table of vulnerabilities included in the original SBOM for components not known to Sonatype. The Sonatype identified vulnerabilities section lists vulnerabilities of the component and is updated through Continuous Monitoring.
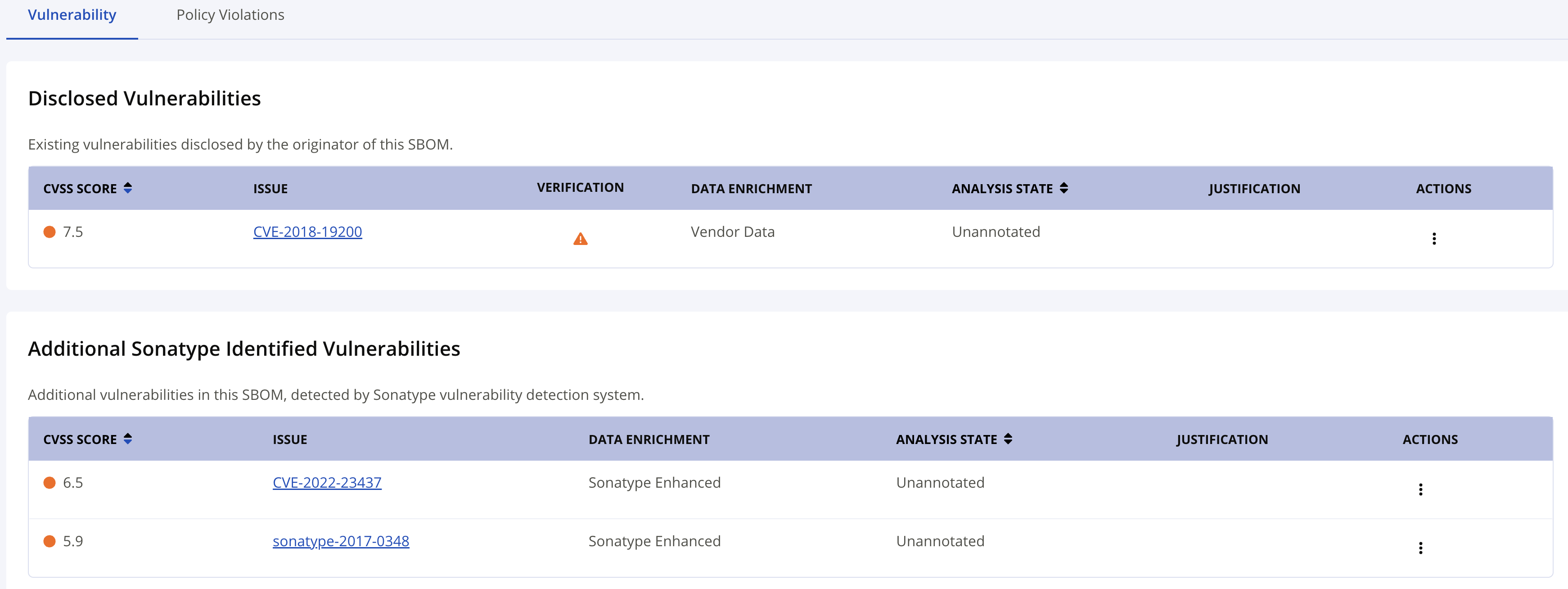
Field | Description | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVSS Score | The Common Vulnerability Scoring System (CVSS) score for the specified vulnerability. See Reference Policies for details on CVSS scoring. | ||||||||||||||||||||
Issue | The issue identifier is assigned to the vulnerability. Select the identifier to expand a panel providing details for this vulnerability. | ||||||||||||||||||||
Verification |
| ||||||||||||||||||||
Data Enrichment |
| ||||||||||||||||||||
Analysis State | Analysis status aligns with Vulnerability Exploitability Exchange (VEX) standards. The analysis states how you know a vulnerability has been addressed.
| ||||||||||||||||||||
Justification | Analysis Status and Justification align with VEX standards. Justification provides additional information to further illustrate findings and mitigation controls.
| ||||||||||||||||||||
Actions | These actions are for use in the VEX workflow:
These options are only displayed when available. For instance, the edit and delete options are not shown when no annotation is present. Similarly, the copy option will not display when there is no previous annotation to copy. |
Vulnerability Details
Details about the vulnerability expand and appear in a side panel when you select an Issue ID.
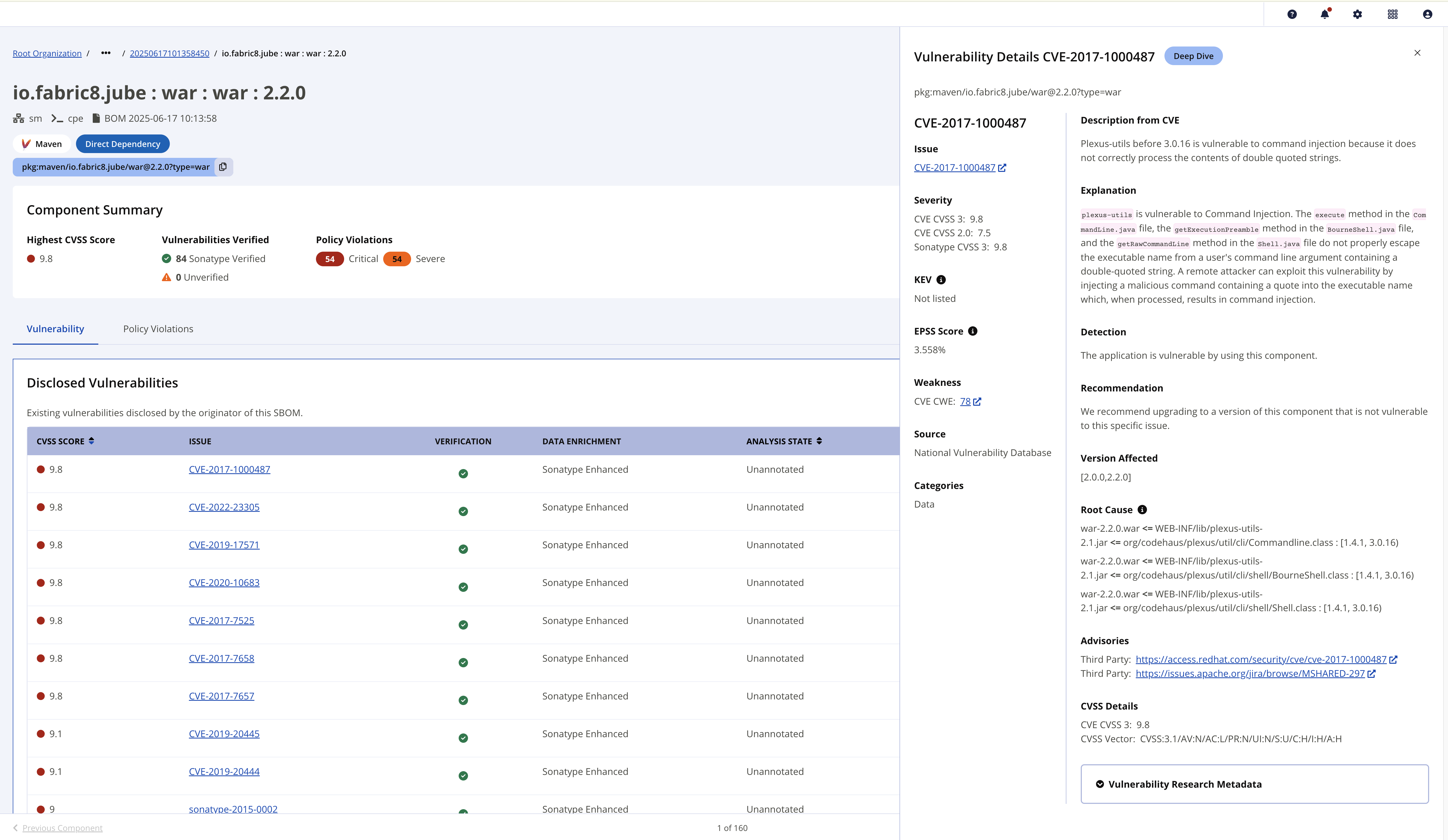
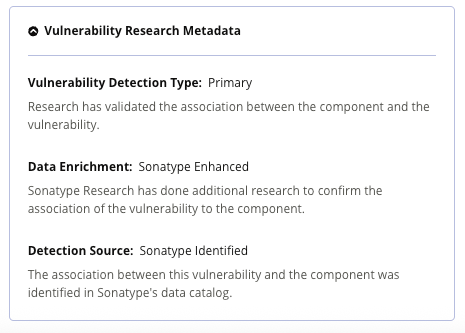
The Vulnerability Details panel includes description, explanation, detection, recommendations, affected versions, root causes, advisories, and CVSS details. As of release 193, there's now a collapsible Vulnerability Research Metadata section with information such as vulnerability detection type, data enrichment, and detection source, and a new pill at the top indicates the security research type (for example, Fast Track or Deep Dive). (See Sonatype Vulnerability Data for full definitions.) Additionally, KEV (Known Exploited Vulnerabilities) status and EPSS (Exploit Prediction Scoring System) data are displayed.
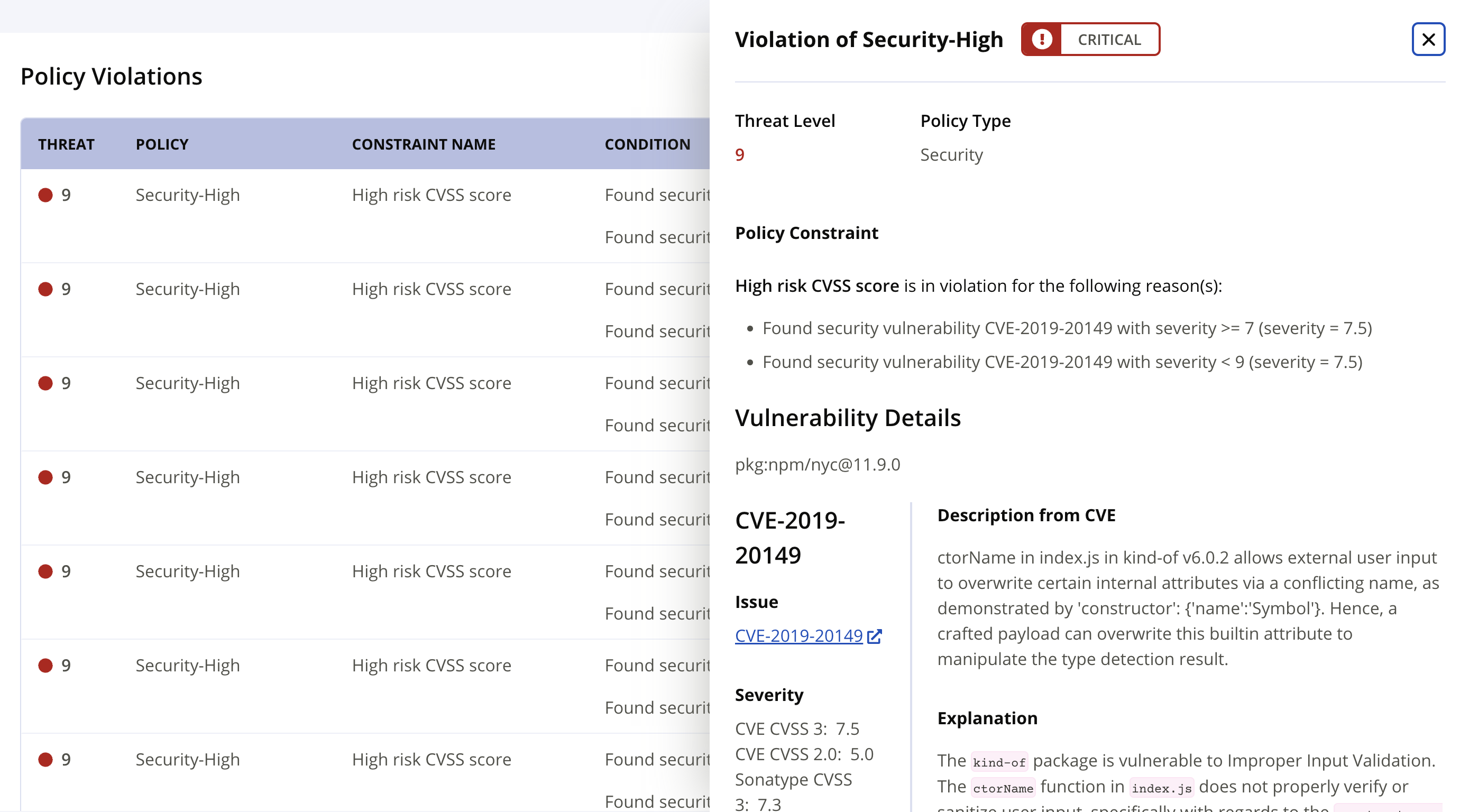
Policy Violations
The policy violation tab lists the policy violations for the component. The violations may be selected to open the violation details view.