Sonatype for Fortify SSC
Note
Get the Sonatype Lifecycle integration with SSC on the Fortify Marketplace.
For IQ Server Java compatibility, refer to the Java Compatibility Matrix.
Architecture Overview
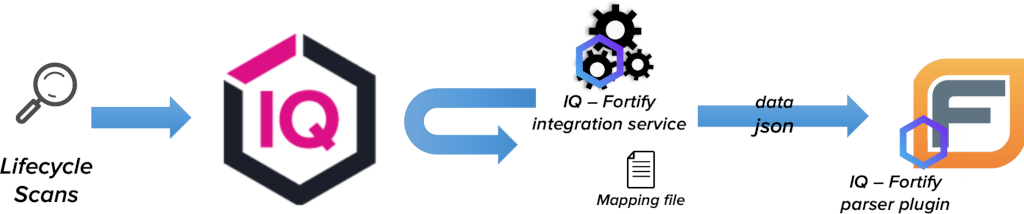 |
The integration has two main parts. Both of them are included in the installation bundle
IQ - Fortify parser plugin
IQ - Fortify integration service
IQ - Fortify Parser Plugin Installation
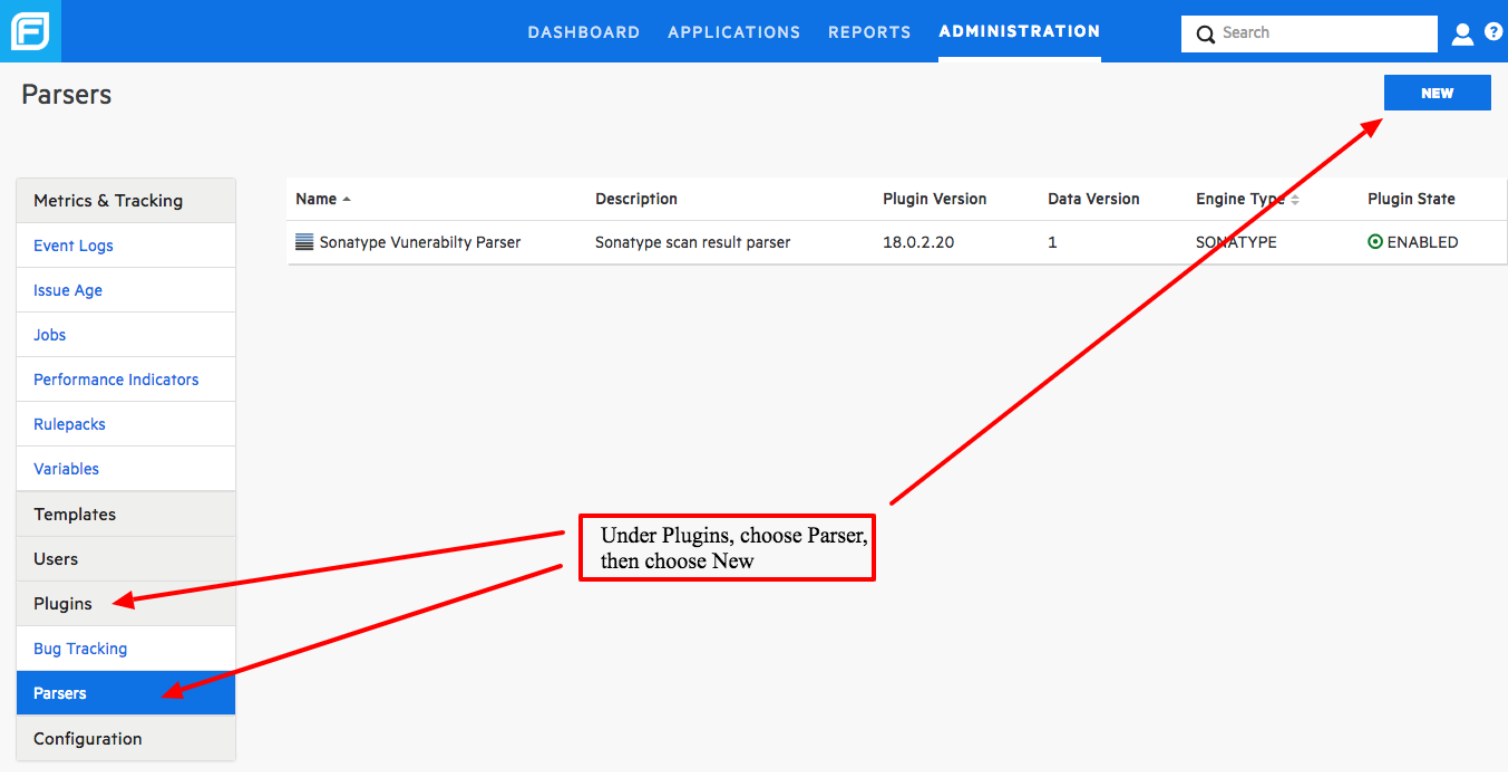
Go to your SSC installation and click on ADMINISTRATION
Then go to Plugins > Parsers
Click on NEW
You will find the following warning. Click on OK
In the next screen select BROWSE and select the plugin JAR file
By default, SSC disables any newly loaded plugin. Click on the Sonatype plugin and enable it.
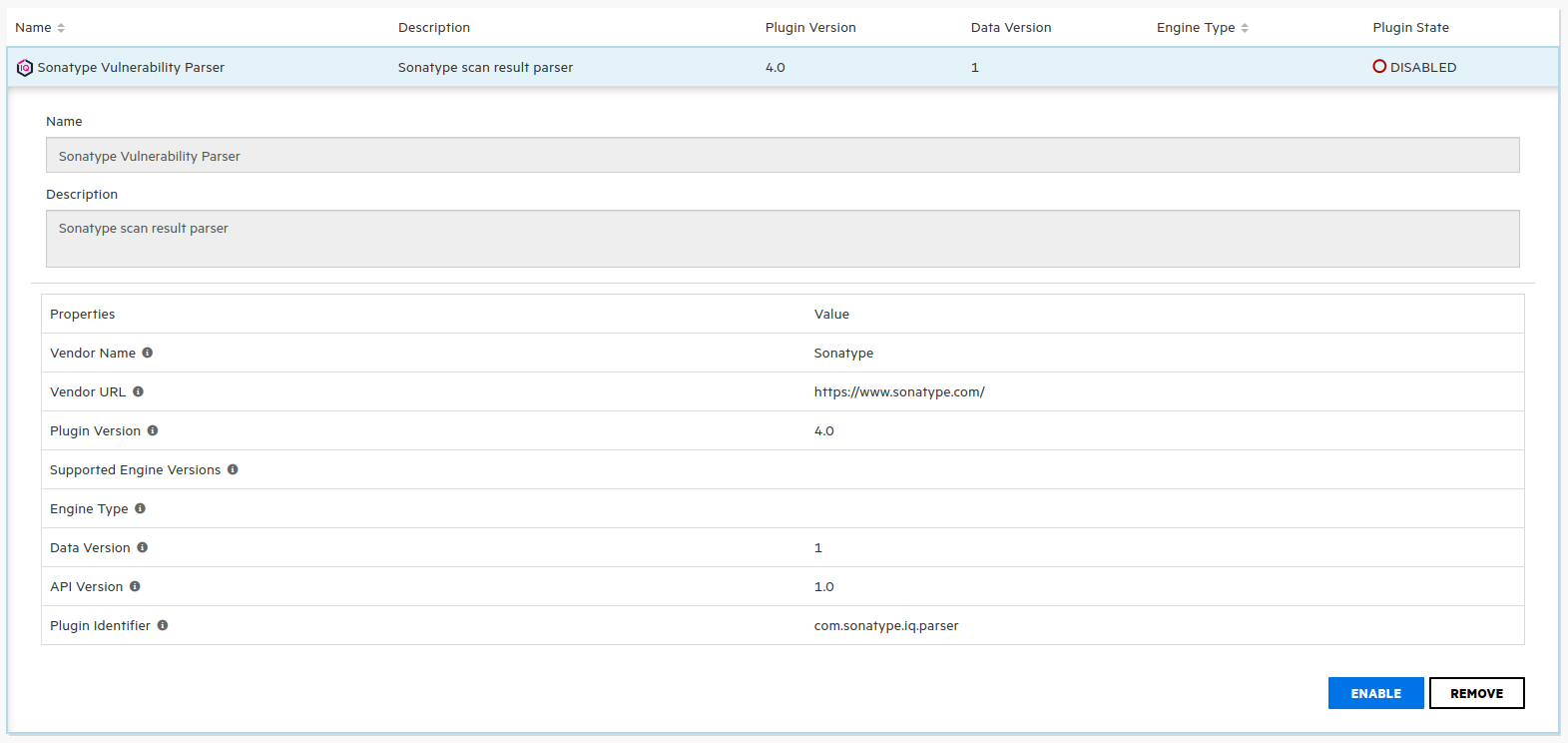
Finally, click on OK to close the warning.
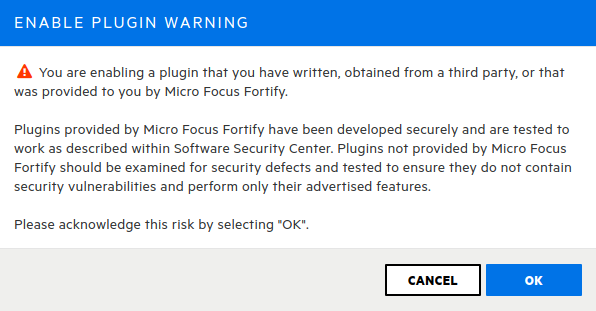
The Sonatype parser plugin should be installed and enabled.
 |
IQ - Fortify Integration Service Configuration and Execution
Both servers must be up and running in order to successfully export data from Lifecycle to Fortify SSC. Other versions of the servers may work, but they are not officially supported.
Service configuration
The integration services have multiple configurations used to access Lifecycle and Fortify SSC servers and fine-tune their behavior.
For this purpose, we have a file named iqapplication.properties. Those configurations are described in detail in this section. Also, you can find useful comments in the configuration file itself.
Note
Fields can also be provided via environmental variables. To convert a property name in the canonical form to an environment variable name:
Replace dots (.) with underscores (_)
Remove any dashes (-)
Convert to uppercase
Parameter | Description and notes | Example |
|---|---|---|
| Required Base URL where your IQ Server instance is running. | |
| Required IQ Server username. | admin |
| Required IQ Server password. | admin123 |
| Required Base URL where your Fortify SSC instance is running. | |
| Required CIToken generated by SSC for an Administrator User. | ODA0NWYzMTUtMzNmOS00ZDY 2LTlkODYtY2RlMDA5YWU1ODQ5 |
| Required Port where the integration service will be listening for requests. | 8182 |
Default: .work | Optional The directory will be generated in the working directory. | /home/sonatype/work |
Default: 8 | Optional Minimum threat level for being considered critical. | 8 |
Default: 4 | Optional Minimum threat level for being considered high. | 4 |
Default: 2 | Optional Minimum threat level for being considered medium. | 2 |
Default: mapping.json | Optional Mapping file to be used as input for the batch process. | /etc/mapping.json |
Default: policy | Optional Possible values: raw, vulnerabilities, policy | raw|vulnerabilities|policy |
Default: 4 | Optional Number of mappings being processed in parallel. | 4 |
Default: 32 | Optional Number of threads to be used for fetching vulnerability details and remediations for components. | 32 |
Default: true | Optional Whether or not to keep the cached files in the work folder. | false |
Default: true | Since 4.3.0 Optional Whether or not to run the synchronization in the background continuously. If set to false, other means of synchonization can be used, such as triggering the full cycle manually, executing on demand synchronizations or using webhooks from the IQ Server. | true |
Default: 1 | Since 4.3.0 Optional Duration between full synchronizations if syncProjectsContinuously is true. If a full synchronization takes longer than the value entered here, it will immediatly run again. | 1 |
Default: SECURITY, LICENSE, QUALITY, OTHER | Since 5.1.0 Optional Categories to synchronize. | |
Default: true | Since 5.1.0 Optional When true, a file named | true |
Default: false | Since 5.1.1 Optional Exits the service after a full sync. Supported only for continuous synchronization and when | true |
Default: 8 | Since 5.3.0 Optional Number of threads to be used to process Webhook requests. | 12 |
Default: false | Optional Unsuppress issues in SSC that does not have a waiver associated. Deprecated in version 5.0.0 | true|false |
Default: 30 | Optional Time in seconds to run the issue suppression/unsuppresion job. Deprecated in version 5.0.0 Starting in version 4.3.0, waivers will be retried in increments, up to 5 minutes. The value set for this property will not guarantee supression being tried every 30 seconds. Every individual synchronization will now wait in incrementals of 30 seconds, 1 minute, 2 minutes, 4 minutes and then afterwards 5 minutes until retry count is exhausted. This configuration still is relevant for how often the tasks are checked to see if they should be retried. | # Run every hour 3600 |
Default: 72 | Optional Maximum retries before the job discard unprocessed artifacts. Deprecated in version 5.0.0 | 72 |
Default: 0 0/360 6 * * ? | Optional By default, this job will run at 6 AM and then every 6 hours. Deprecated in version 4.3.0 Starting in version 4.3.0, scheduling job will continuesly run. The time to wait between every cycle can be configured by the property | # Run every three hours scheduling.job.cron=0 0 0/3 1/1 * ? |
The integration will synchronize all violation categories by default. However, you can customize it using iqapplication.properties to configure which categories will be synchronized. The field and possible values are as follows:
synchronisation.policy.violation.categories = SECURITY, LICENSE, QUALITY, OTHER
Running the integration service
Using a command line, go to the Integration directory. E.g. /home/sonatype/IntegrationService
Start the integration using this command:
./start.shIf you want to run it in the background, you can use:
nohup ./start.sh &The visual guide shows a quick example of unpacking and running the service.
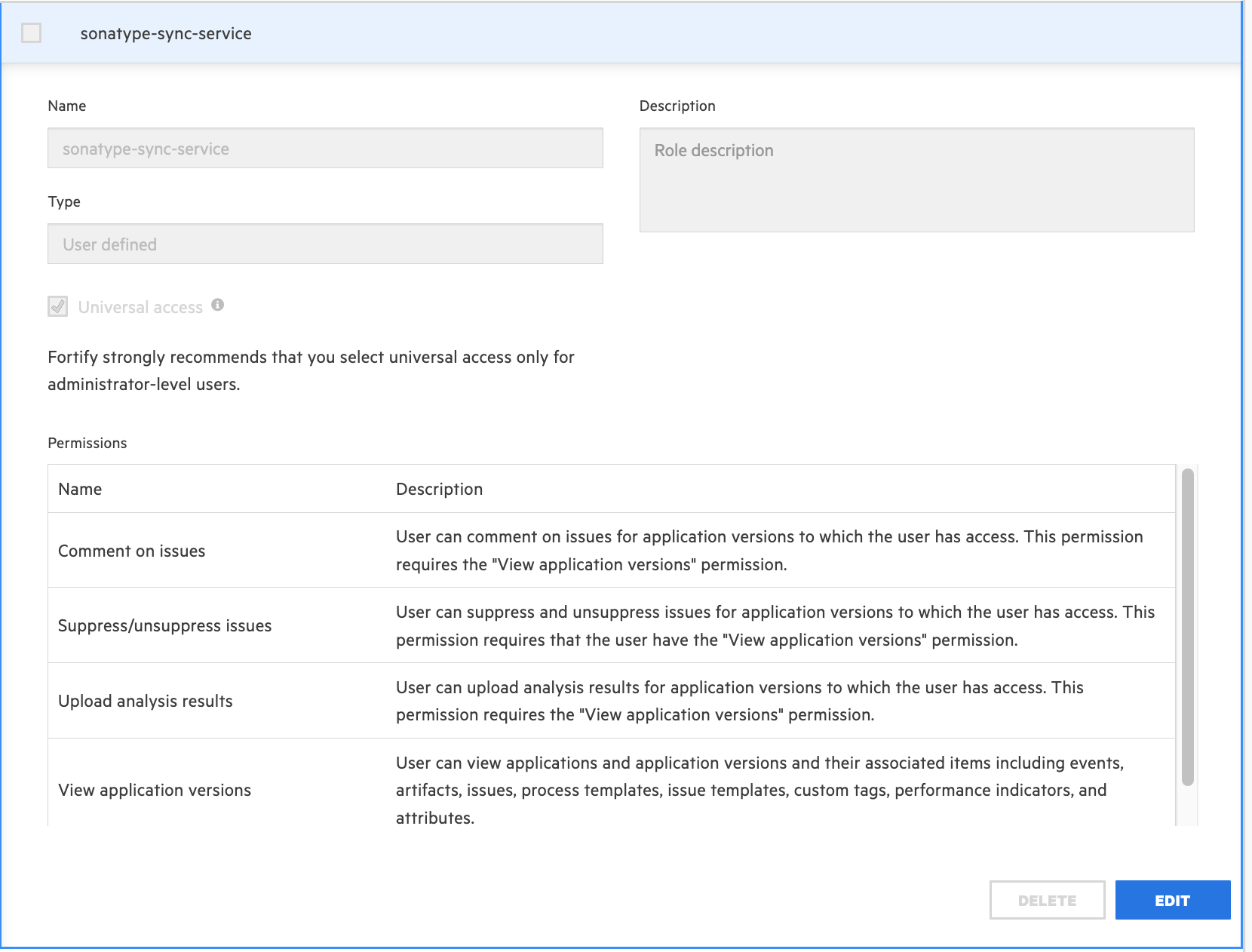
Permissions
The CI token owner must have universal access to the following permissions:
Comment on issues
Suppress/un-suppress issues
Upload analysis results
View application versions
Synchronization scheduler
Before 4.3.0
This service has a built-in scheduler that understands cron-like expressions. By default, it runs every six hours, but that can be configured using the scheduling.job.cron property.
Since 4.3.0
This service by default synchronizes all entries found in the mapping file with a duration of 1 minute between each run. This behavior can be changed by setting the synchronize.projects.continuouslyproperty to false or the duration between the cycles can be modified by using the scheduling.fixed.rate.minutes property. Modifying the synchronize.projects.continuously property has no effect on on-demand synchronization requests.
It is required to configure a mappings file (defined in the mapping.file property) to provide the parameters for the projects you want to synchronize in a scheduled fashion.
Since 5.1.0
You can enter either the new field fortifyApplicationId or keep using fortifyApplication.
The mappings file has the following structure:
[
{
"sonatypeProject": "test-app-01",
"sonatypeProjectStage": "build",
"fortifyApplication": "01-test-01",
"fortifyApplicationVersion": "001",
},
{
"sonatypeProject": "test-app-02",
"sonatypeProjectStage": "build",
"fortifyApplicationId": 6,
"fortifyApplicationVersion": "1.0",
}
]Parameter | Mandatory | Description |
|---|---|---|
sonatypeProject | yes | Public ID of the project that already exists in IQ Server |
sonatypeProjectStage | yes | Project stage in IQ Server |
fortifyApplication | either this or | Target application name in Fortify SSC |
fortifyApplicationId | either this or | Target application ID in Fortify SSC |
fortifyApplicationVersion | yes | Target application version in Fortify SSC |
overwrite | no | Unsuppressed issues in SSC that do not have a waiver associated. If this value is not present we take the value from the properties file |
Synchronization endpoint
It may happen that you want to synchronize an IQ project that is not already present in your mappings file, or you simply want to trigger a synchronization on demand. For those cases the integration exposes an endpoint to manually trigger these synchronizations. This is the endpoint definition:
Endpoint GET /startScanLoad
Parameter | Mandatory | Description |
|---|---|---|
sonatypeProject | yes | Public ID of the project that already exists in IQ Server |
sonatypeProjectStage | yes | Project stage in IQ Server |
fortifyApplication | either this or | Target application name in Fortify SSC |
fortifyApplicationId | either this or | Target application ID in Fortify SSC |
fortifyApplicationVersion | yes | Target application version in Fortify SSC |
overwrite | no | Unsuppressed issues in SSC that do not have a waiver associated. If this value is not present we take the value from the properties file |
saveMapping | no | Take the current request and save it as a mapping. The mapping will be saved only if the synchronization is executed successfully |
Note
If one of the mandatory parameters is missing in the request, the integration will perform synchronization using all the values found in the mappings file (like in the scheduled job).
In this specific case, even if the saveMapping is true, the request won't be saved since we do not have a full mapping to save.
One-time Project Synchronization endpoint
To synchronize a desired project adhoc, use this endpoint. It will synchronize the provided project in all stages immediately. The mapping information for the provided project must exist in the mappings file.
Endpoint GET /startScanLoadSingleProject?sonatypeProject={sonatypeProjectPublicId}
Parameter | Mandatory | Description |
|---|---|---|
sonatypeProject | yes | Public ID of the project that already exists in IQ Server |
One-time Report Synchronization Endpoint by scanId
Since 5.4.0
Use this endpoint to synchronize a single IQ report into Fortify SSC by its scanId.
Endpoint
GET /startScanLoadSingleReport?scanId={scanId}Prerequisites
A mapping file must exist (the file configured by
mapping.file) and it must contain exactly one mapping.The mapping must include the following properties:
[ { "sonatypeProject": "test-app", "fortifyApplication": "test-app", "fortifyApplicationVersion": "1.0" } ]
Behavior
Invoking the endpoint synchronizes the report identified by the provided scanId into the Fortify application/version specified in the single mapping shown above (e.g., test-app / 1.0).
Recommended Configuration
Set these properties when you’re using the ad‑hoc scanId flow:
synchronize.projects.continuously=false killProcess=true loadfile.cache=false
Set
synchronize.projects.continuously=falseso the background scheduler does not try to run the usual mapping‑file sync while you’re doing a one‑off report sync viascanId. This only disables the continuous schedule; it does not affect on‑demand endpoints.Set
killProcess=truesince there’s no point keeping the service running after this one‑time operation completes.Set
loadfile.cache=falseto avoid keeping temporary cached artifacts for this one‑off run.
Integrating IQ Webhook with Fortify SSC Sync Service
Refer to Integration of IQ Webhook with Fortify SSC Sync Service for details.
About the Scan Report
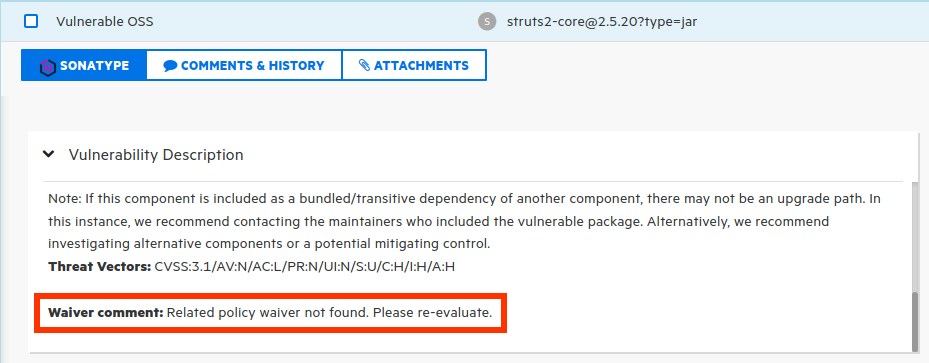
Waiver Comment
If you encounter a waiver comment: "Related policy waiver not found. Please re-evaluate", it means you had a waived issue in your IQ server and the waiver was removed.
To get rid of this comment, you can go to your IQ instance, reevaluate the report, and run another synchronization.
 |
Since 5.0.0
This comment now appears in the "Comments & History" section.
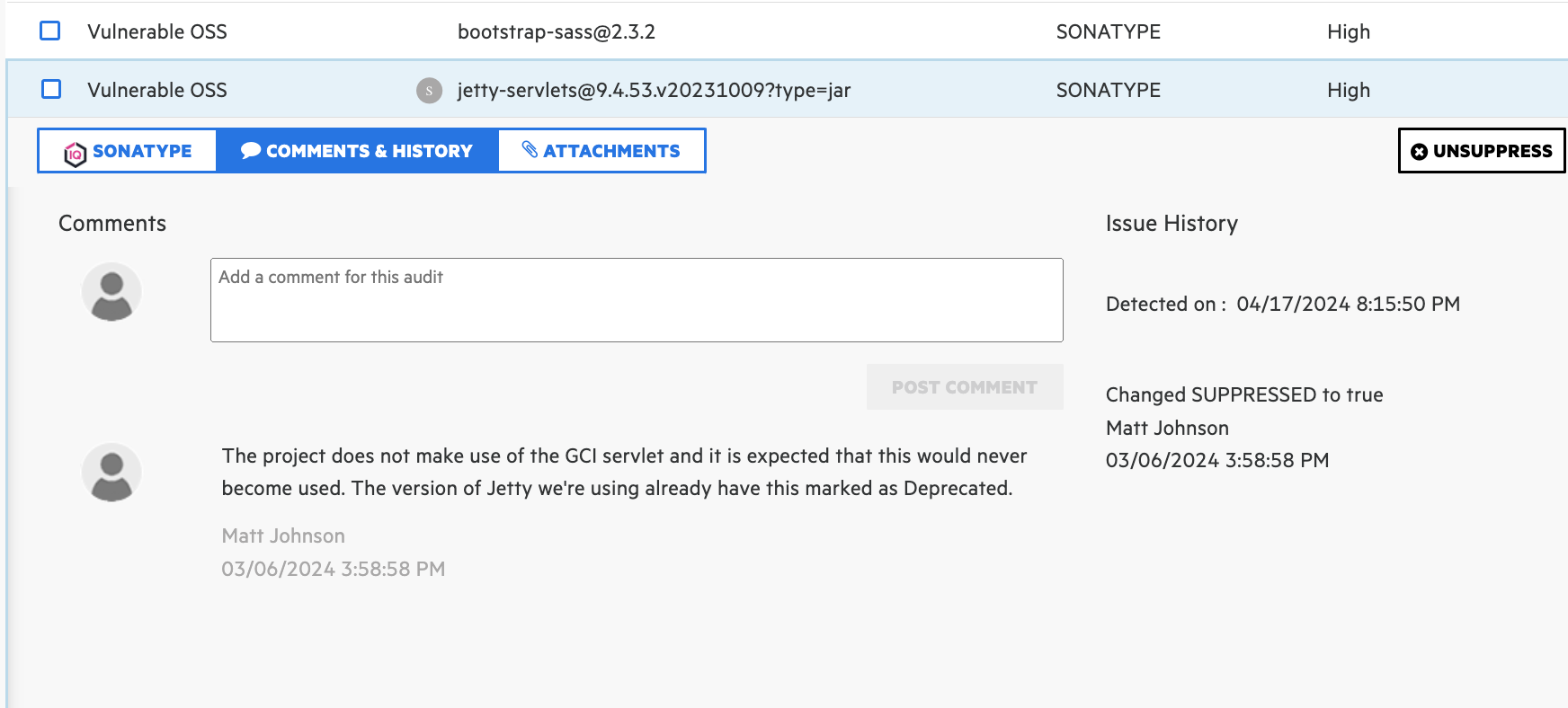 |
Remediation information
Since 5.1.0
The remediation information is now displayed in a separate field for better visibility.
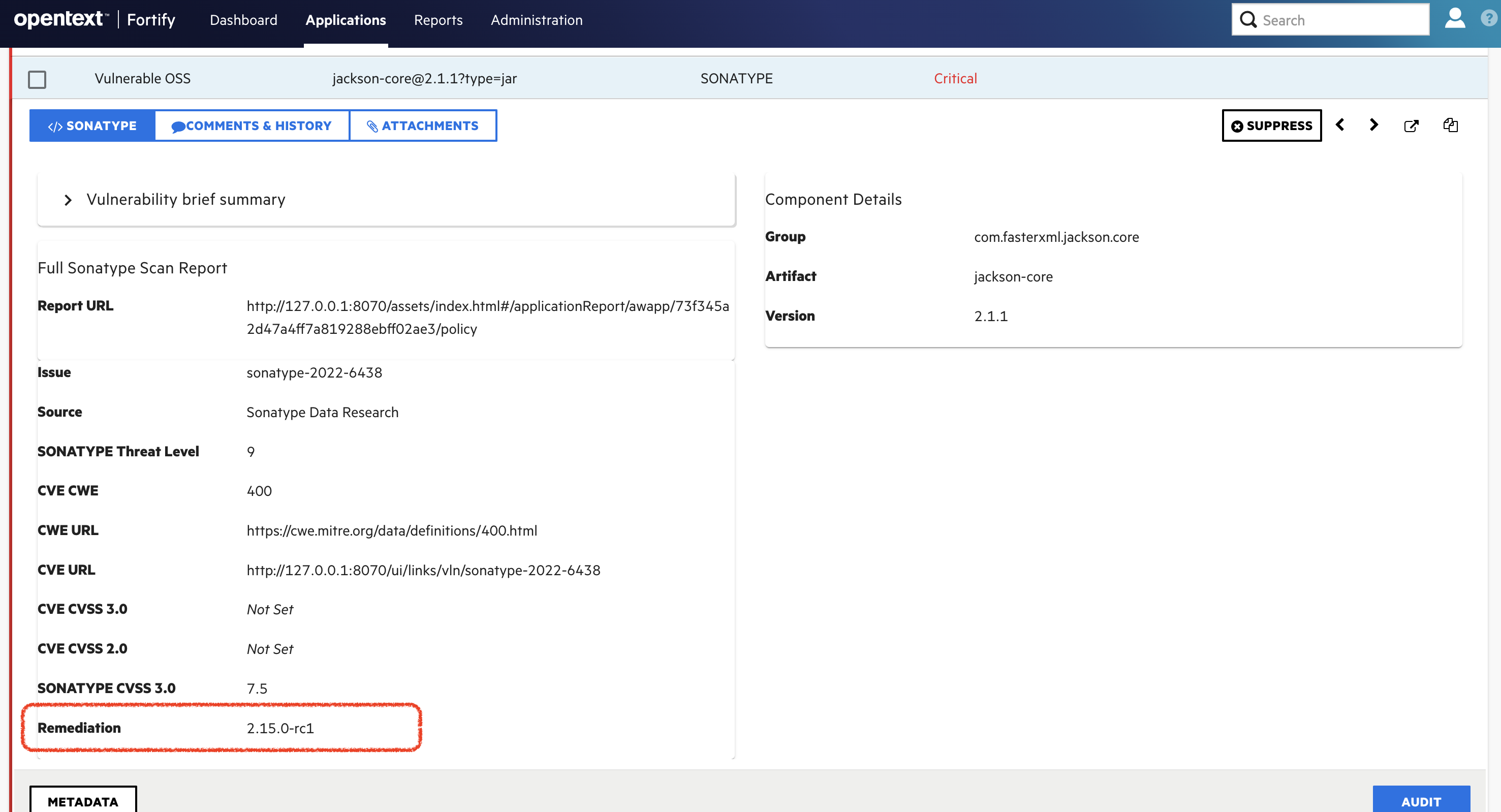
Continuous Monitoring
Reports generated by Continuous Monitoring in IQ Server are skipped if they don't reveal any new information compared to the most recently synchronized report.