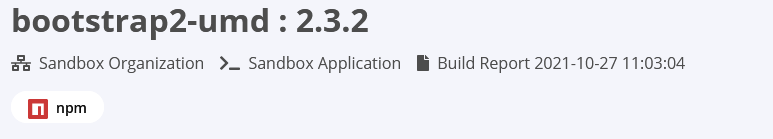
Component Details Page
The Component Details Page is where you can drill down on individual components that appear in your scanned applications, along with the policy violations associated with them.
Tags
At the top of the Component Details Page, underneath the name of the component, are a few important details, including the hierarchy location of the application that was scanned and a timestamp for when the report was generated.
 |
Underneath, you'll see tags, which are color-coded identifiers that can help you rapidly determine some important biographic and relational information about the component. A list of possible tags is below.
| Indicates the ecosystem the component is sourced from, if applicable. |
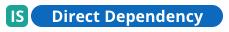
 | Indicates the component is a direct dependency. |
 | Indicates the component is a transitive dependency. |
 | Indicates the component is an innersource dependency. |
 | Indicates the component is an innersource direct dependency. |
 | Indicates the component is an innersource transitive dependency. |
If the component has any Labels applied to it, they'll be included with the tags. You can identify labels by the icon at the start of the identifier, like in the example below.
 |
Overview
Component Information Section
In the Component Information section, you'll see some basic information about the component. The table below outlines the details provided by the Component Information section.
Cataloged | The age of the component is based on when it was first added to the source from which it was identified. |
|---|---|
Match State | How the component was matched in comparison with IQ Server's database of extant components (exact, similar, or unknown) |
Occurrences | The number of times the component was found in the application. Click the link to see the paths where the component was found. This information is provided to help you detect accidental shipping of duplicate component archives or a misconfiguration of your actual report creation target. |
Identification Source | What is the component identification based on:
|
Category | What the component is used for, as categorized by Sonatype. Possible values include designations like "Data Protocols," "Logging," "Networking Utilities," etc. This is the same category that can be used to set a policy's constraint. |
Note that details on the left side of the section are contextual to the ecosystem from which the component was drawn. For example, a component from Maven will show "Group" and "Artifact" identifiers, but a component from npm will show the "packageId" identifier instead.
Note
When scanning an SBOM that contains a proprietary component, whilst it may not violate the “unknown components” policy, it is still identified as “unknown” by Lifecycle.
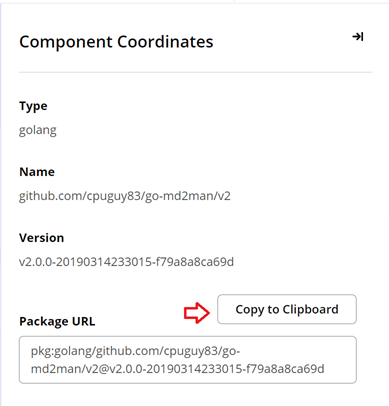
View Coordinates
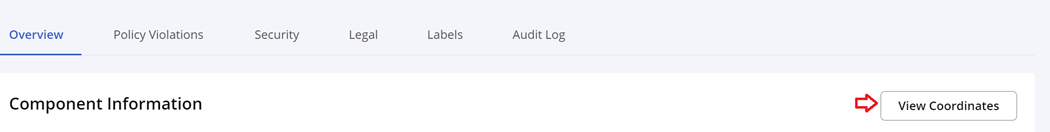
Click on the View Coordinates button in the top right section of Overview for detailed component coordinates.
The Copy to Clipboard button allows copying long and complicated package URL for use in other places.
Version Explorer
The right side of the Version Explorer allows you to quickly view details about other versions of the component. The current component is indicated by the vertical gray bar. The popularity of the component is indicated by the green bars at the top. The more popular a component is, the larger the bar.
Color markers show expected policy violations. The colors here match the policy violation colors you see elsewhere in IQ Server. For expected policy violations, red markers indicate a very high-risk level, while orange, yellow, and blue markers indicate lower risk levels. No marker indicates no threat.
Breaking Changes also appears in the Version Explorer. Yellow, orange, and red markers indicate increasing numbers of breaking changes, while blue markers indicate no breaking changes. Note that Breaking Changes is currently only available for the Maven ecosystem.
Golden Version
NOTE: The Golden Version recommendation is currently available for the Maven ecosystem only.
Sonatype's Component Intelligence scores a component version as the Golden Version if it falls under the recommended-non-breaking-with-dependencies category of recommendation. This is a safe-to-use version of the component (including its dependencies) with no resulting breaking changes, that can be used for upgrade to remediate the reported policy violation.
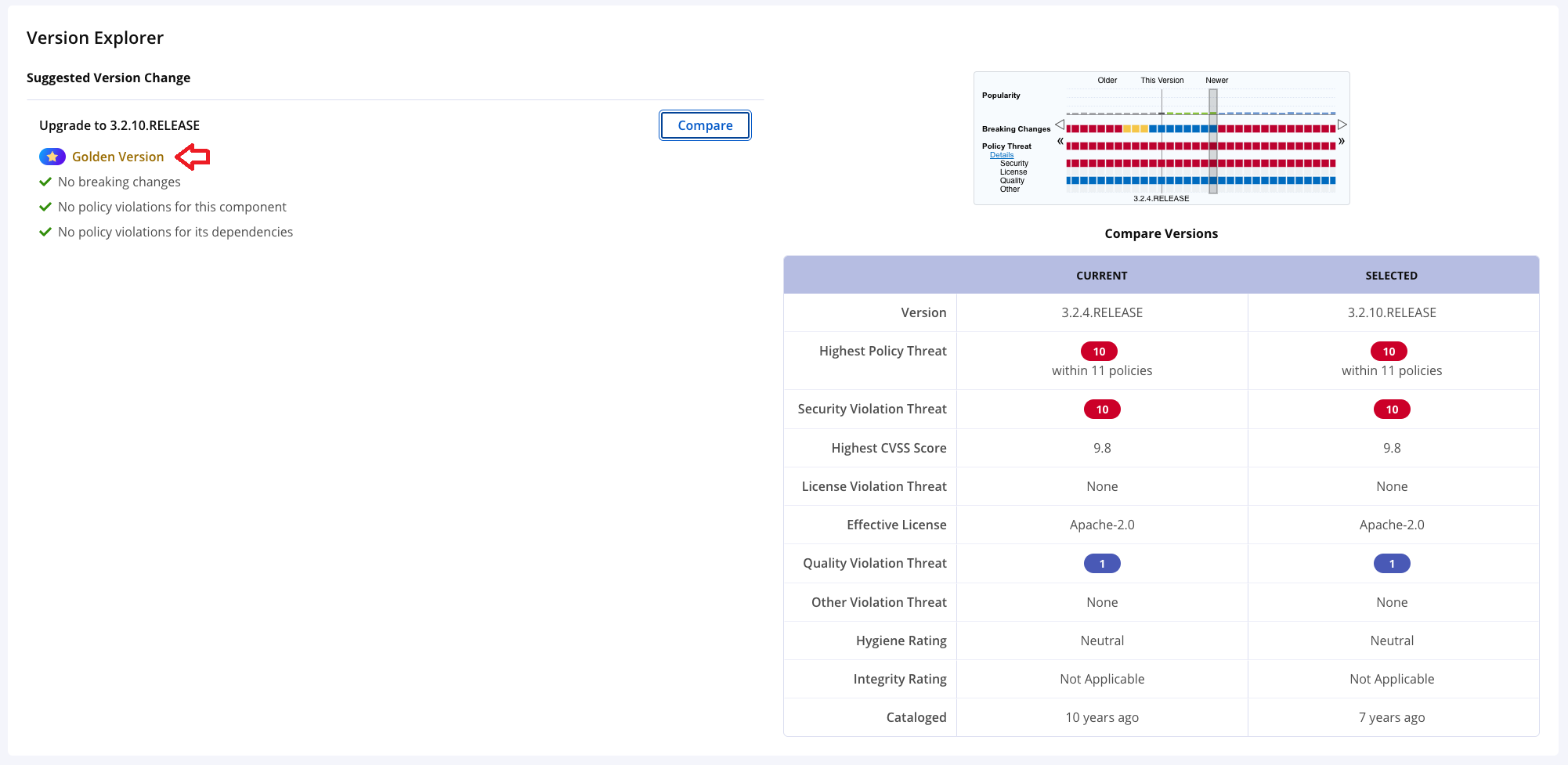
Compare Versions
The Compare Versions table shows details about the component currently being used in your application. If you click another version of the component in the Version Explorer or click "Compare" in the Recommended Versions section, information about that version of the component will populate in the right-hand column. This allows you to rapidly and thoroughly compare your original component with possible replacements.
The table below outlines the details provided in the Compare Versions table.
Version | The version number of the selected component. |
|---|---|
Highest Policy Threat | The highest threat level policy that has been violated, as well as the total number of violations. The value may be NA if all threats have been waived. |
Highest CVSS Score | The highest threat level security vulnerability and the total number of security vulnerabilities. The value may be NA if all threats have been waived. The value may be None if the component hasn't violated any security policies. |
License Violation Threat | The highest threat level license policy violation and the total number of license policy violations. The value may be NA if all threats have been waived. The value may be None if the component hasn't violated any license policies. |
Effective License | Licenses included in the Declared or Observed Group, or the overridden license. |
Quality Violation Threat | The highest threat level quality policy violation and the total number of quality policy violations. The value may be NA if all threats have been waived. The value may be None if the component hasn't violated any quality policies. |
Other Violation Threat | The highest threat level other violations and the total number of other violations. The value may be None if the component hasn't violated any other policies |
Hygiene Rating | The quality (Laggard, Exemplar, None) of an open-source project. This is calculated based on the projects that exhibit the best and worst behaviors to producing quality open-source software. |
Integrity Rating | The level of suspicion (Suspicious, Normal) of this version as determined by our machine-learning intelligence. Versions that are marked suspicious may be malicious. The value may be Not Applicable if no integrity data is applicable. |
Cataloged | The age of the component is based on when it was first added to the source from which it was identified. |
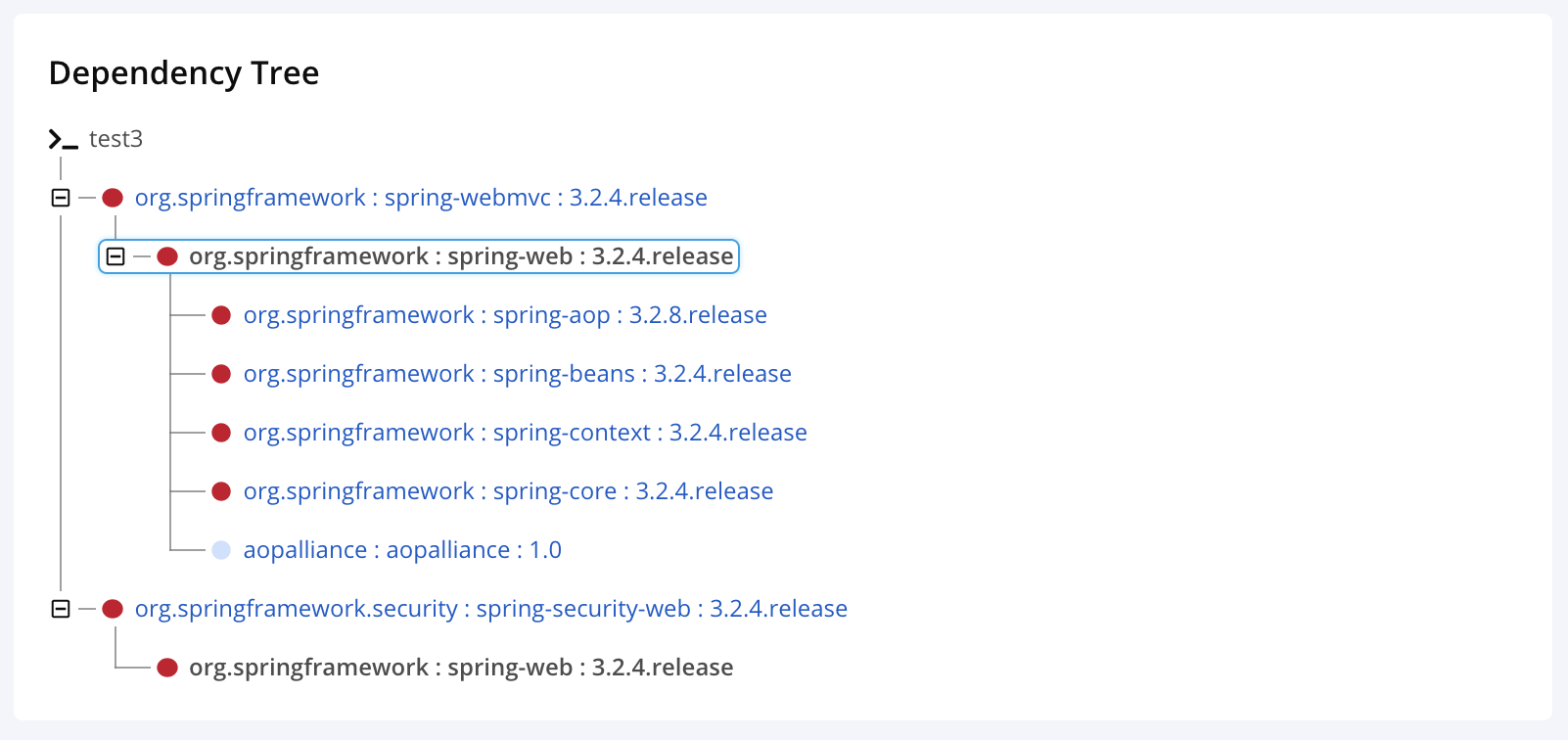
Dependency Tree section
The Dependency Tree section lets users analyze dependency relationships within a subtree of the Application Composition Report Dependency Tree. The subtree is comprised of all occurrences of the current component, its ancestors, and its descendants.
Clicking on a dependency takes the user to the Component Details Page for that component.
 |
Note
The Dependency Tree section is only available for Maven and npm ecosystems.
Policy Violations Tab
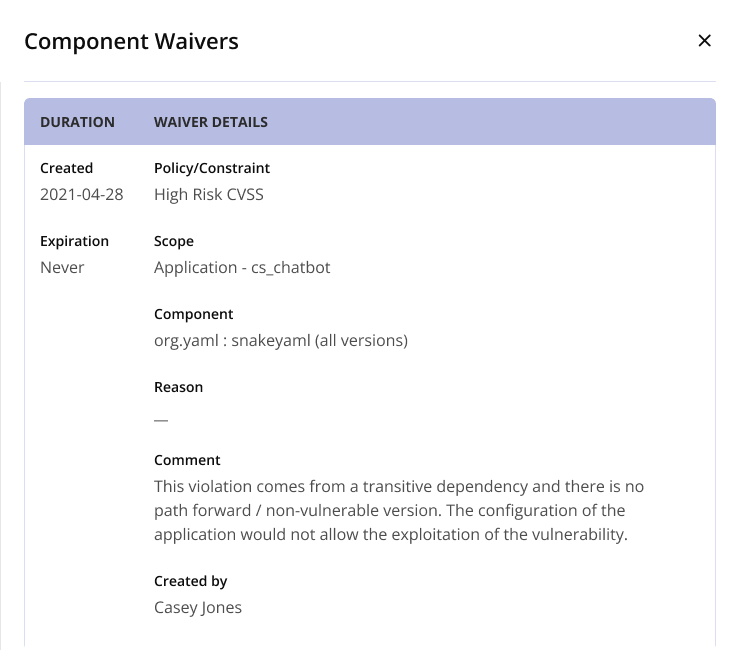
The Policy Violations tab shows all policy violations associated with the component. Clicking on the "View Existing Waivers" button on the right will show a pop-up that lists any active waivers associated with this component.
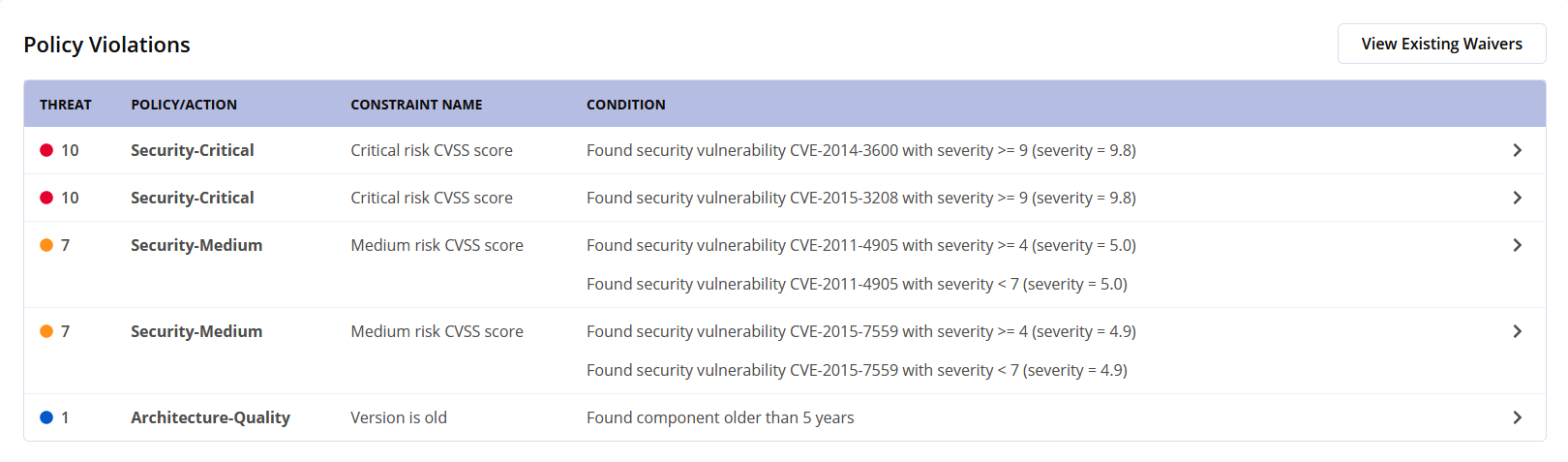 |
Click on the View Existing Waivers button to view the Component Waivers pop-up. It contains waiver details including the policy/constraint name, the date created on, expiration date (if applicable), scope of the existing component waiver, name of the component the waiver applies to, the reason for applying the waiver, created by username and comments.
Violation Details Popover
Clicking on a violation in the Policy Violations tab brings up the Violation Details popover.
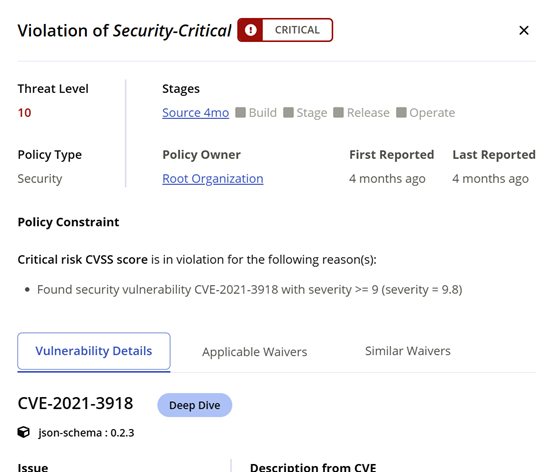
Here, you can see more information about the violation, including:
First Reported indicates the date of the policy evaluation when this violation was first detected. If a previously reported violation is remediated (or waived), but is seen again in a policy evaluation report at a later date, the First Reported date is the new (later) date, and will not match the First Reported date in the previous violation.
Stages: the stage of the build where the policy violation was found
Policy Owner: the part of the organization hierarchy that owns the policy.
Note
Remember, the organizational hierarchy has "Root Organization" at the top, "Organization" below that, and "Application" at the bottom. If the Policy Owner is the "Root Organization", then the policy is being applied to all Organizations and Applications. Likewise, if the Policy Owner is "Application", then the policy is being applied only to the current application.
The Policy Constraint section shows exactly how IQ Server's knowledge about the component interacts with the policy in question.
Condition: the policy condition that was set (which you can think of as part of the if/then statement.)
Constraint: which is a grouping of active Conditions. In the example you see above, the Constraint consists of just one condition, and that condition is the presence of a security vulnerability.
If the policy violation isn't security related – for example, if the policy is about licensing or architecture – then the Violation Details popover ends here.
Vulnerability Details Section: is seen if the policy violation is security-related. The bottom of the popover shows the vulnerability described in more detail. Details are pulled from applicable sources, like the National Vulnerability Database and Sonatype's own proprietary research, in order to describe why the component is vulnerable and how it could be exploited.
Vulnerability Details
The enhanced Vulnerability Details page includes the vulnerability research metadata for the selected vulnerability.
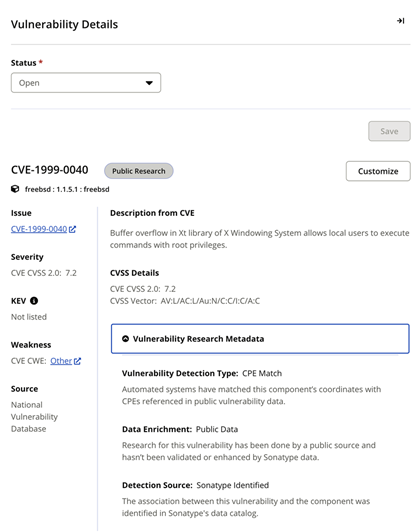
Vulnerability Detection Type: Indicates the process of vulnerability identification, primary, secondary, AST, or Other . Refer to Sonatype Vulnerability Data for details.
Data Enrichment: Indicates the data sources used for establishing the vulnerability.
Detection Source: Indicates if the vulnerability exists in Sonatype's data catalog or is provided by an external source.
KEV: Indicates that the vulnerability is listed in the KEV (Known Exploited Vulnerabilities) catalog.
If a policy for KEV status is violated (refer to set policy constraints for KEV status), it will appear under the Policy Constraint header.
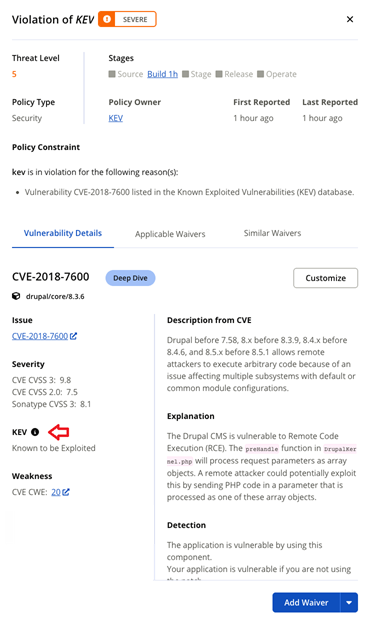
EPSS: A data-driven model that assigns each CVE a percentage probability of being exploited in the wild within the next 30 days. Refer to policy constraints for more details.
Managing Waivers
Click on the Applicable Waivers or Similar Waivers tab to view waivers related to the policy violation for this vulnerability.
Click on the Request Waiver button to request waivers for a component. If you're authorized, it's also where you'll add waivers.
The Reachability Column
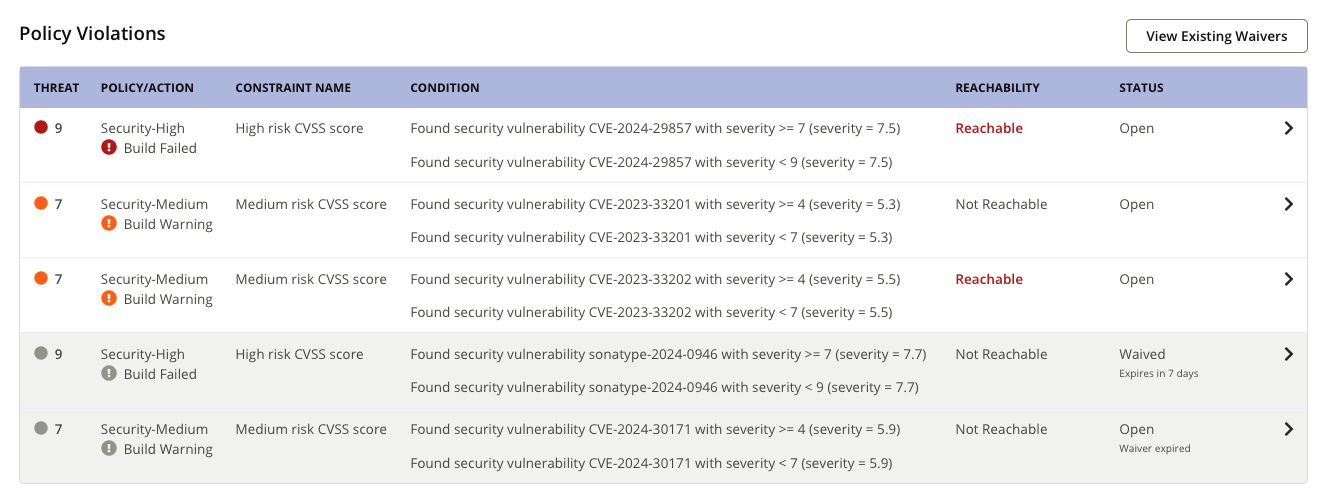
Reachability: The Reachability column indicates if the policy violation is found to be Reachable, based on Reachability Analysis. It can have the following values:
Reachability | Description |
|---|---|
Reachable | The policy violation is triggered by a component that is found to be reachable. It should be remediated to reduce risk. |
Not Reachable | The policy violation is triggered by a component that is found to be not reachable. Remediation of this violation is not a priority, and a waiver can be applied. |
Unknown (displayed as ' - ') | Reachability Analysis was not performed. |
What is the Violation Status Now?
The Open status under the Status column, indicates that a previously applied waiver to the violation has expired in the last ten days.
The Waived status under the Status column contains additional information on the number of days after which the waiver will expire.
Security Tab
The Security in the Component Details Page can be used by the Security team members who want a focused look at only the issues pertaining to their role. The Security tab can be thought of as condensed, specialized offshoots of the Policy Violations tab.
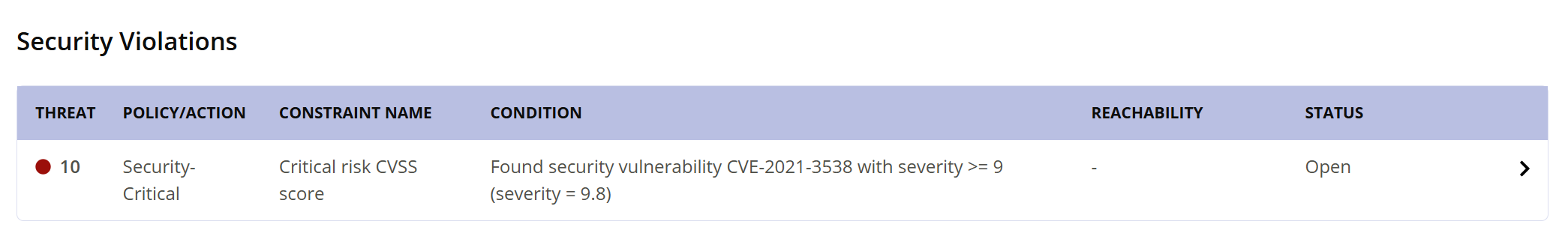
Security Violations
You can view a list of Security Violations in this section. No other violations are displayed in this tab. No other violations are displayed in this tab. Just like in the Policy Violations tab, clicking a violation brings up the Violation Details window.
Vulnerabilities
This section displays a list of all vulnerabilities associated with the security violation.
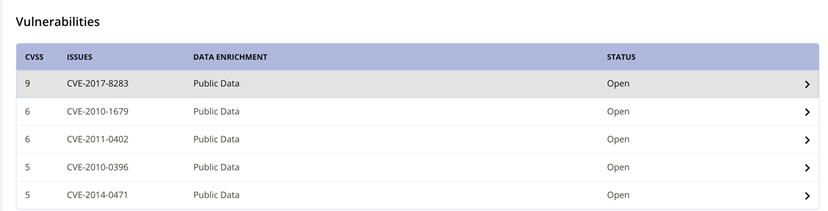
Data Enrichment: Indicates the data sources used for establishing the vulnerability. Possible values for Data Enrichment include:
Public Data, if the vulnerability is found to be reported in public data sources.
Sonatype Enhanced, if the vulnerability is detected by Sonatype Vulnerability Detection system.
Vendor Data, if the vulnerability has been reported in an SBOM and is not found in public data sources or detected by Sonatype Vulnerability Detection system.
Click on a Vulnerability row for more details.
Legal Tab
The Legal tab in the Component Details Page can be used by the Legal team members who want a focused look at only the issues pertaining to their role. The Legal tab can be thought of as condensed, specialized offshoots of the Policy Violations tab.
In the Legal tab, you can view the License Detection box, which shows the Effective and Declared Licenses of the component, and a list of Legal Policy Violations. No other violations are displayed in this tab. Just like in the Policy Violations tab, clicking a violation brings up the Violation Details window.
Labels Tab
The Labels tab allows you to assign and manage labels to the component.
Claim Tab
If a component found during a scan is given a match state of Unknown or Similar, you can use the Claim tab to manually add details about it.
Audit Log Tab
When a user makes changes to the Status of a security vulnerability or the Status of a component’s license within the scope of a particular application, that information is recorded in the Audit Log.
Typically, resolving policy violations by changing a component's Status is riskier than using Waivers, because status changes are more difficult to track. When possible, use Waivers to accept the risk of a policy violation.
Next Component/Previous Component
At the bottom of the Component Details Page and frozen to the bottom of your browser window are buttons to take you to the next or previous component listed in the Application Composition Report, just as if you had used your browser's Back button and manually selected the next or previous component in the list.
Moving through the list of components in this way duplicates the "Aggregate by component" filtering option. This means that components only appear on the list once, regardless of how many policy violations they're associated with.