Public Data Sources for CPE Vulnerabilities
Common Platform Enumeration Vulnerability Detection
The relationship between CPE (Common Platform Enumeration) identifiers and CVEs (Common Vulnerabilities and Exposures) is crucial for effective vulnerability management. When a vulnerability (CVE) is discovered, the National Vulnerability Database (NVD) is updated by NIST to indicate which CPE identifiers (product names and versions) are vulnerable.
Sonatype's vulnerability database ingests all CPE-CVE mappings from the public data sources (NVD feed), to allow detection of additional vulnerabilities, outside of the vulnerabilities detected from the proprietary vulnerability detection system.
Sonatype Lifecycle can identify the CPE names from the ingested SBOMs and trigger policy evaluations.
CPE-based matching for C/C++ is available starting in IQ 193, but whether it’s enabled by default depends on your setup: fresh IQ 193+ installations enable it by default, while upgrades from IQ 192 or earlier require manual enablement; availability also varies by whether your plan is SBOM Manager–only, Lifecycle–only, or multi-solution. See CPE Matching Experience per Solution table and C/C++ Application Analysis for details.
Configuring Lifecycle to Use Public Data Sources
Users can configure Lifecycle to use public data sources for detection of vulnerabilities. This includes the CPE product dictionary that contains official CPE names.
Steps to configure Public Data Sources:
Click on Orgs and Policies in the left navigation bar.
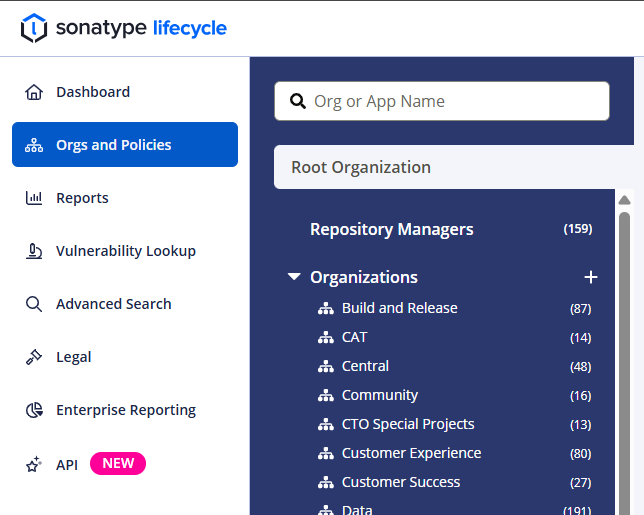
Select root organization or the organization/application for which you want to enable the inclusion of public data sources for policy evaluations.
Click on Public Data Sources in the top navigation bar.
Scroll down to the Public Data Sources section.
Click on the right arrow to access the Public Data Sources configuration.
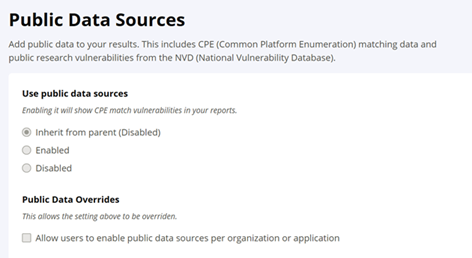
NOTE: The Inherit from parent option is available for all organizations and applications (except for root organization) and can be used to enable Public Data Sources for all organizations and applications lower in the organization hierarchy.
Check the box under Public Data Overrides to allows users to selectively enable the public data sources for a specific organization or application.
NOTE: This section will not be available at the application level.
How It Works:
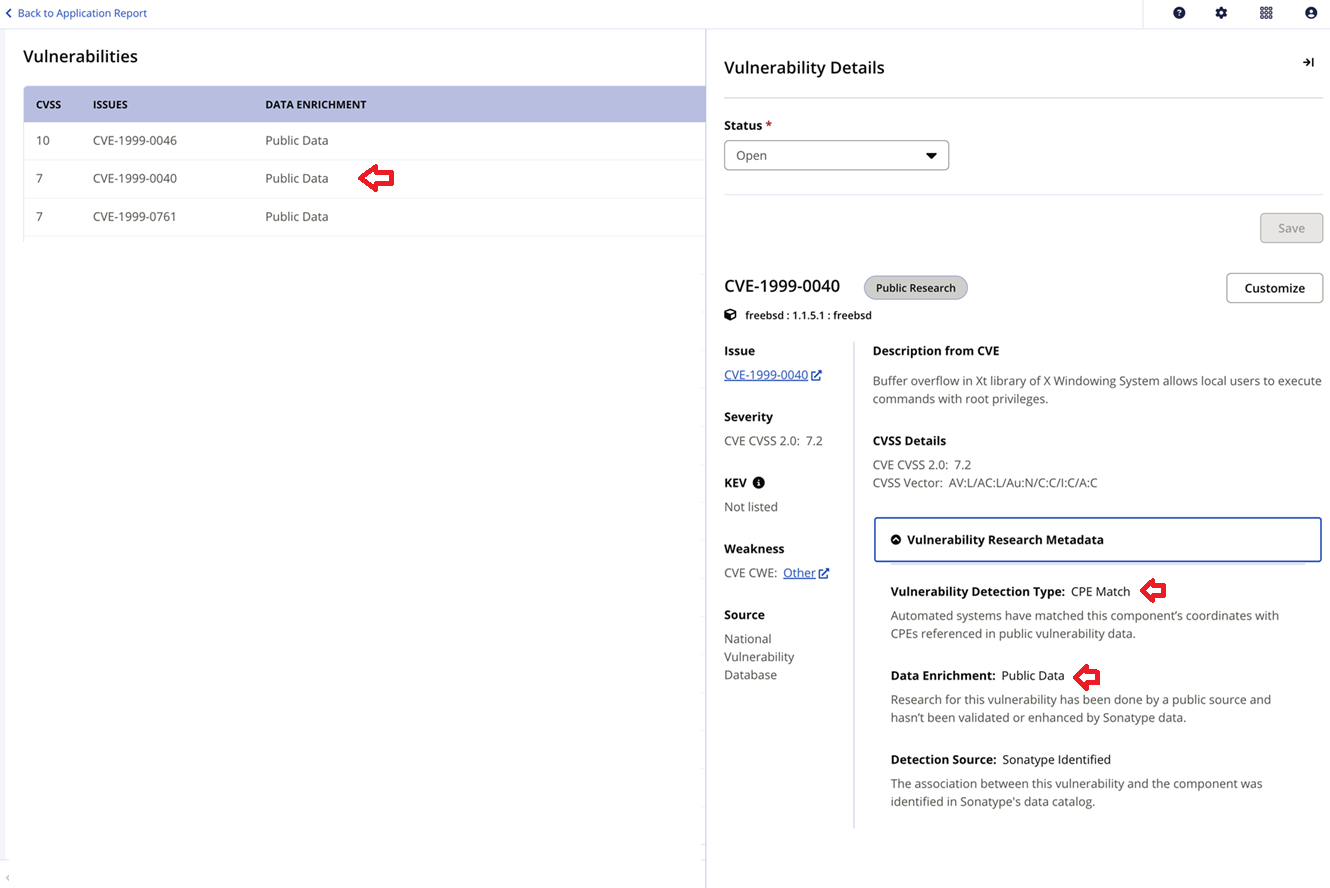
The application evaluation report will show the vulnerabilities detected from public data sources.
Click on the Security tab on the Component Details Page and scroll down to the Vulnerabilities table.
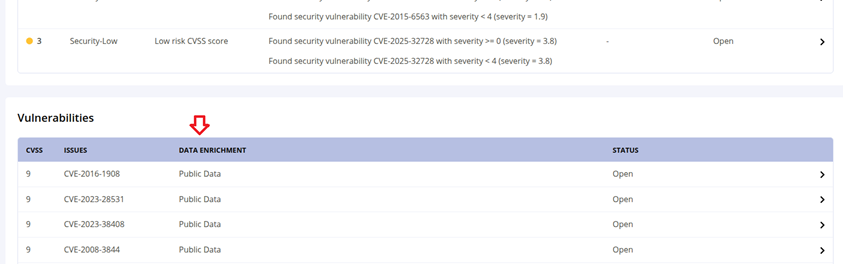
The Data Enrichment column indicates Public Data for vulnerabilities detected from public data sources.
Click on a row to view the Vulnerability Details.