Azure DevOps Configuration
Create an Access Token in Azure DevOps
Supported Azure DevOps Authentication
For secure authentication with Azure DevOps, we strongly recommend using Personal Access Tokens (PATs). PATs offer more granular control and are the preferred method for integrations and automation. For more information, refer to the official Azure DevOps documentation on Personal Access Tokens.
Alternate credentials authentication (including username and password) was fully deprecated in Azure DevOps in January 2024. Personal Access Tokens are the required method for secure and continued access.
Required Token Permissions
Feature | Azure DevOps |
|---|---|
Code: Read & Write | |
Code: Read & Write | |
Code: Read & Write | |
Not Applicable for AzureDevOps | |
Not Applicable for AzureDevOps |
To create a personal access token:
Log in to your organization in Azure DevOps
Open your user settings
Select Personal access tokens from the User Settings menu.
Click the + New Token button
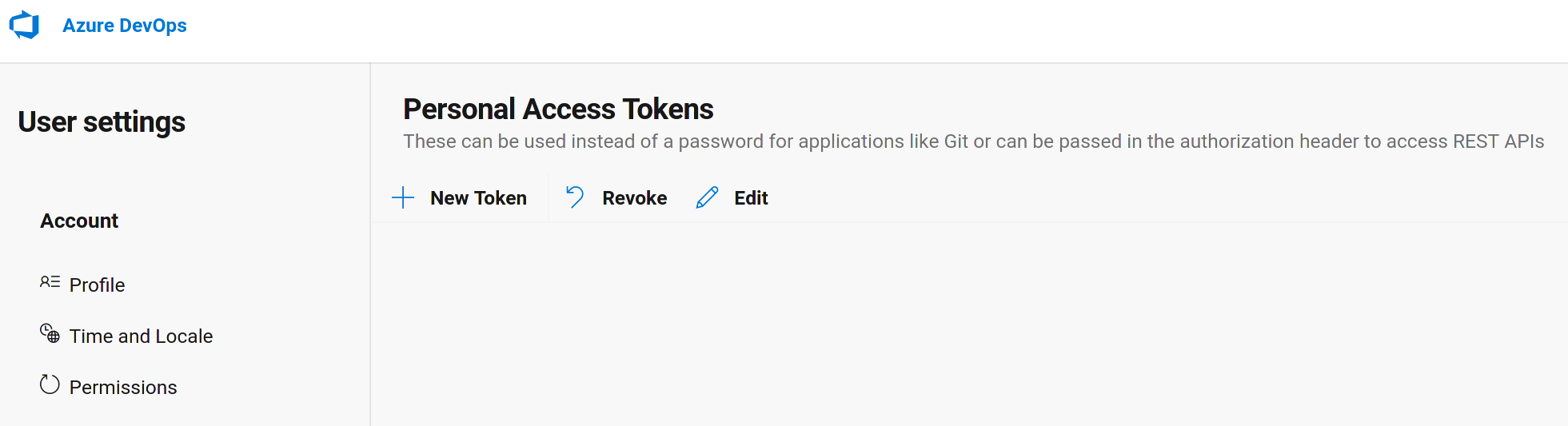
Name your token and select All accessible organizations. Choose an expiry date for your token.
Warning
Important! If you do not select All accessible organizations, the Easy SCM Onboarding feature will not work.
To enable automated pull requests and automated commit feedback:
Select the scopes for this token to authorize for your specific tasks. For the full features of IQ SCM support enable Code: Read & Write and then select Create.
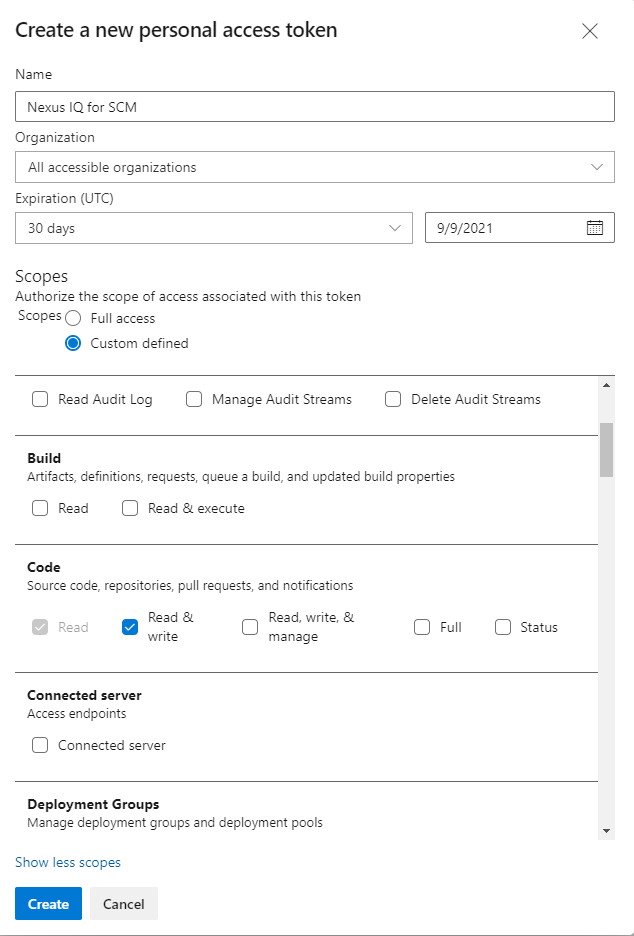
For Azure DevOps scopes details, refer to the Azure DevOps documentation.
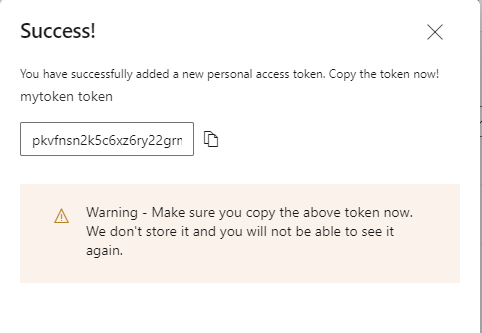
Save the personal access. You will not be able to view it again.
Protecting the Target Branch
You can prevent users from merging Pull Requests with failing IQ Policy Evaluations. IQ Policy Evaluations must be set to Fail at the Source Stage.
Create and configure a Branch Policy to protect your target branch:
1. Navigate to Repos → Branches in the left menu, and select a branch to protect (typically main or develop). Select Branch policies from the menu.
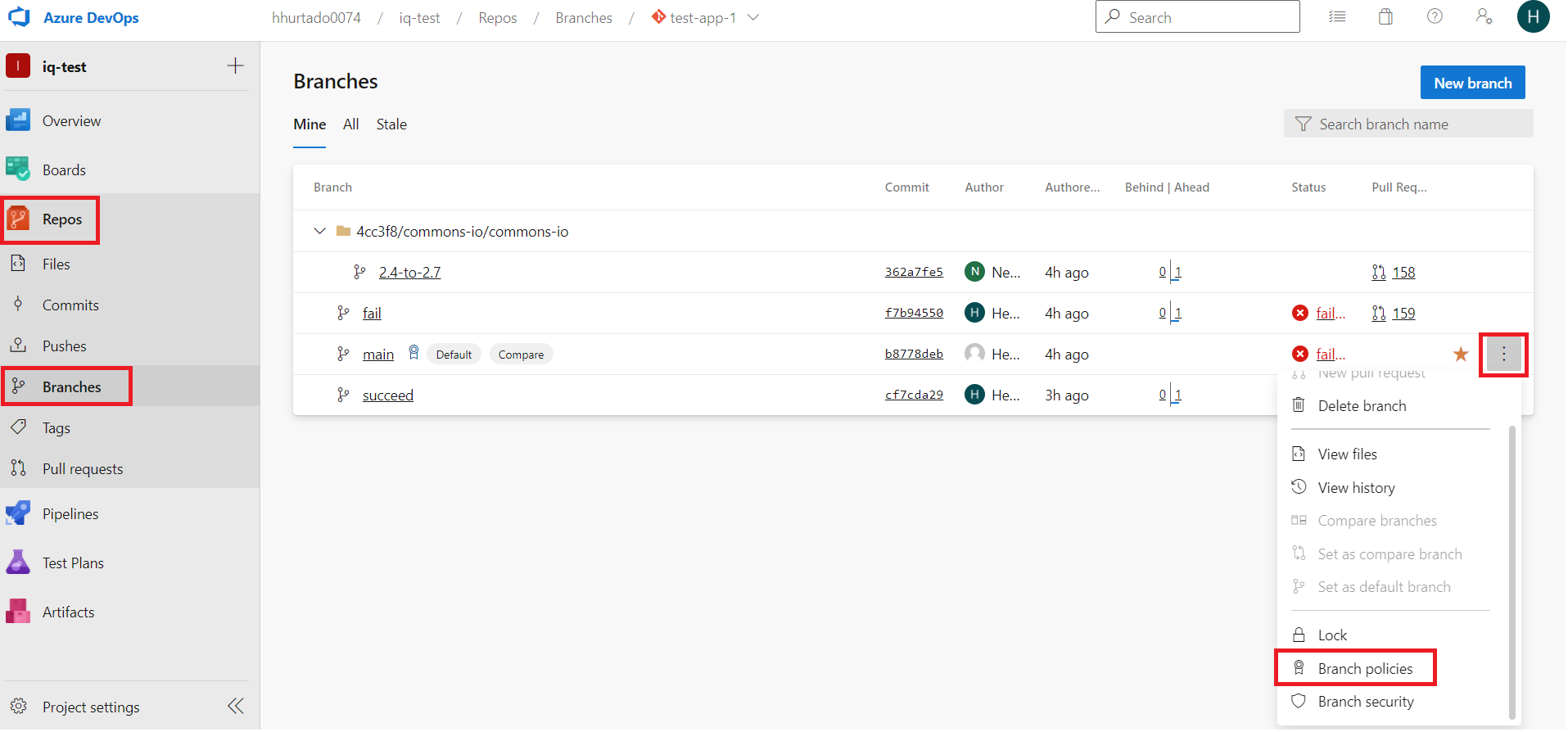 |
2. Find Status checks and click the + button
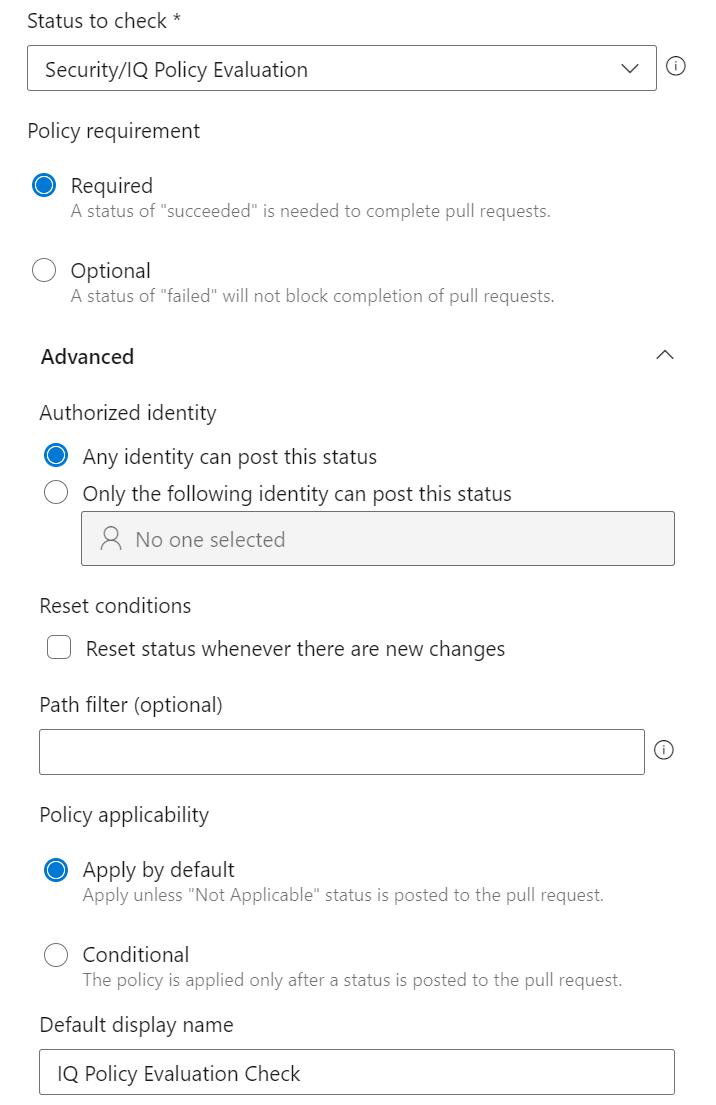
3. Fill out the form
Status to check * → Security/IQ Policy Evaluation
Policy requirement → Required
The rest of the values can use the default options
 |
See this page for more information on branch policy configuration.