GitHub Configuration
Creating an Access Token in GitHub
Supported GitHub Authentication
You can use either classic personal access tokens or fine-grained personal access tokens. For more information on the differences between these token types, refer to the GitHub Docs.
Basic authentication (username and password) is not supported. This method is less secure and GitHub has deprecated its use for authenticating Git operations since August 13, 2021.
Required Token Permissions
Feature | GitHub |
|---|---|
repo:status | |
repo | |
repo | |
repo | |
user:email read:user |
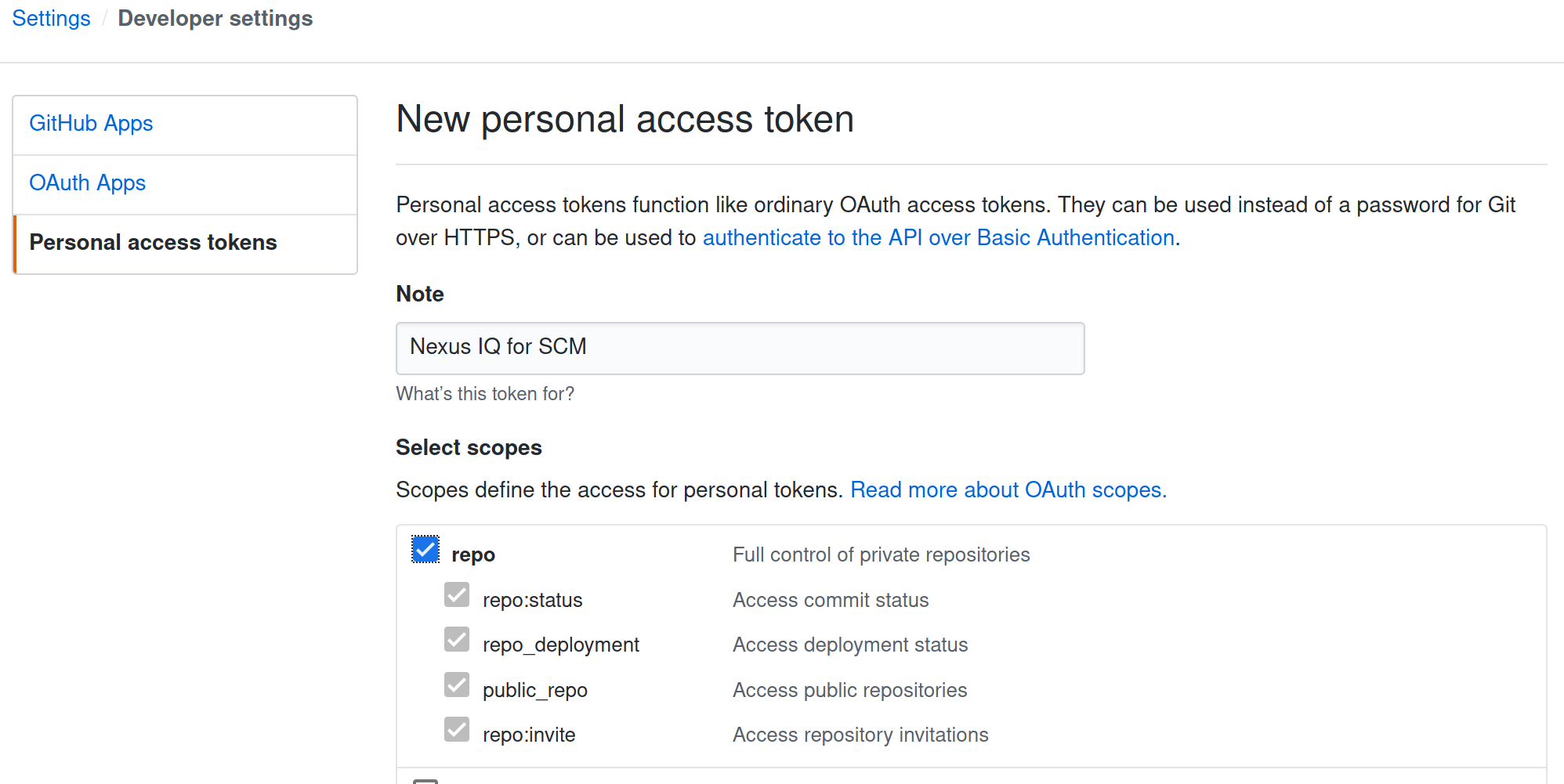
Create the access token:
Log in to GitHub.
In the upper-right corner click your avatar and select Settings.
In the left menu click Developer Settings.
In the left menu click Personal Access Tokens.
Click the Generate new token button.
Configure the token with the Required Token Permissions
Save the personal access token. You will not be able to view this token again.
 |
Creating a fine-grained personal access token in GitHub
Repository Permissions | Access |
|---|---|
Repository Access | All repositories or a subset |
Administration | Read-only |
Commit statuses | Read and write |
Contents | Read and write |
Deployments | Read-only |
Metadata | Read-only |
Pull requests | Read and write |
Create the access token
Log in to GitHub.
In the upper-right corner click your avatar and select Settings.
In the left menu click Developer Settings.
In the left menu select Fine-grained Tokens.
Click the Generate new token button.
Configure the token with the Required Token Permissions
Save the personal access token. You will not be able to view this token again.
Protecting the Target Branch in GitHub
You can prevent users from merging Pull Requests with failing IQ Policy Evaluations with a Branch Protection Rule. IQ Policy Evaluations must be set to Fail at the Source Stage.
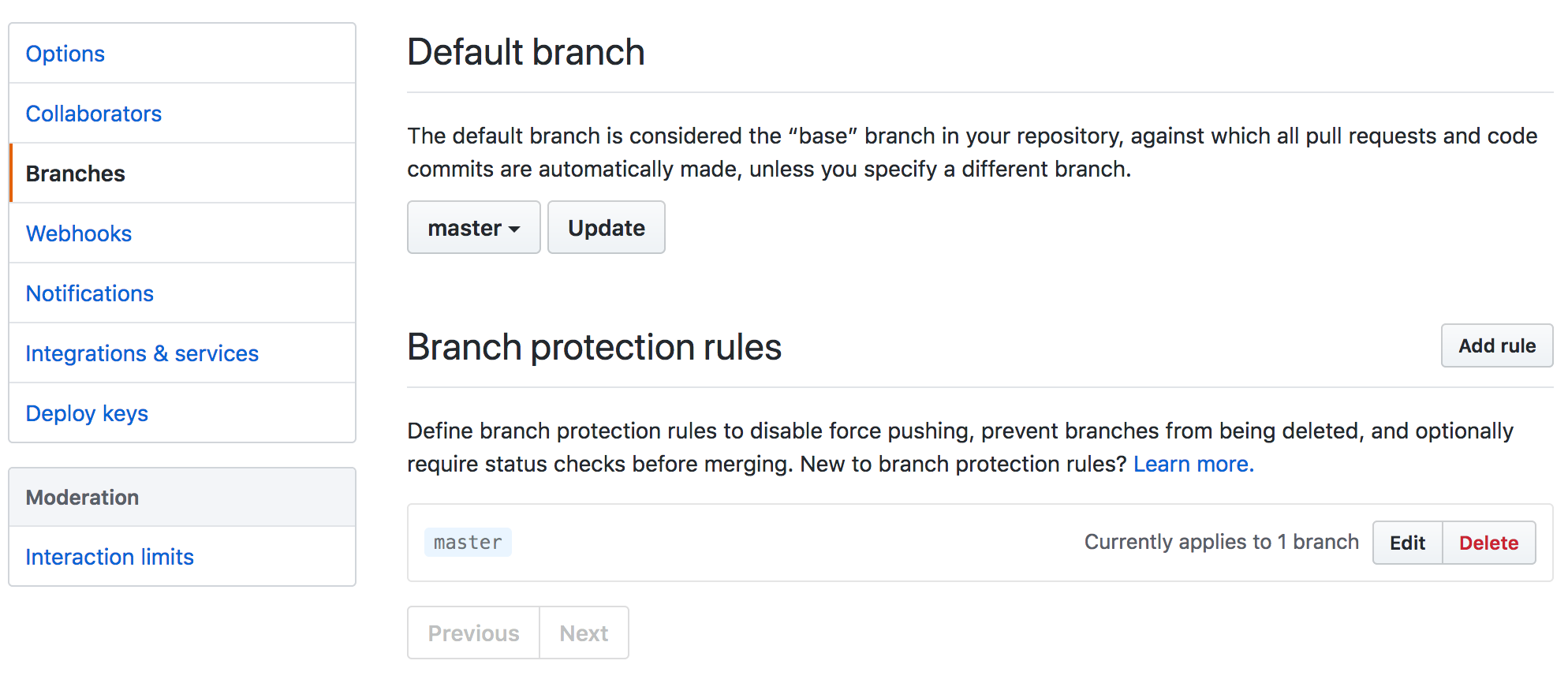
To protect a branch:
Select a Repository.
Click Settings.
Select Branches from the sidebar.
Click Add rule or edit an existing rule.
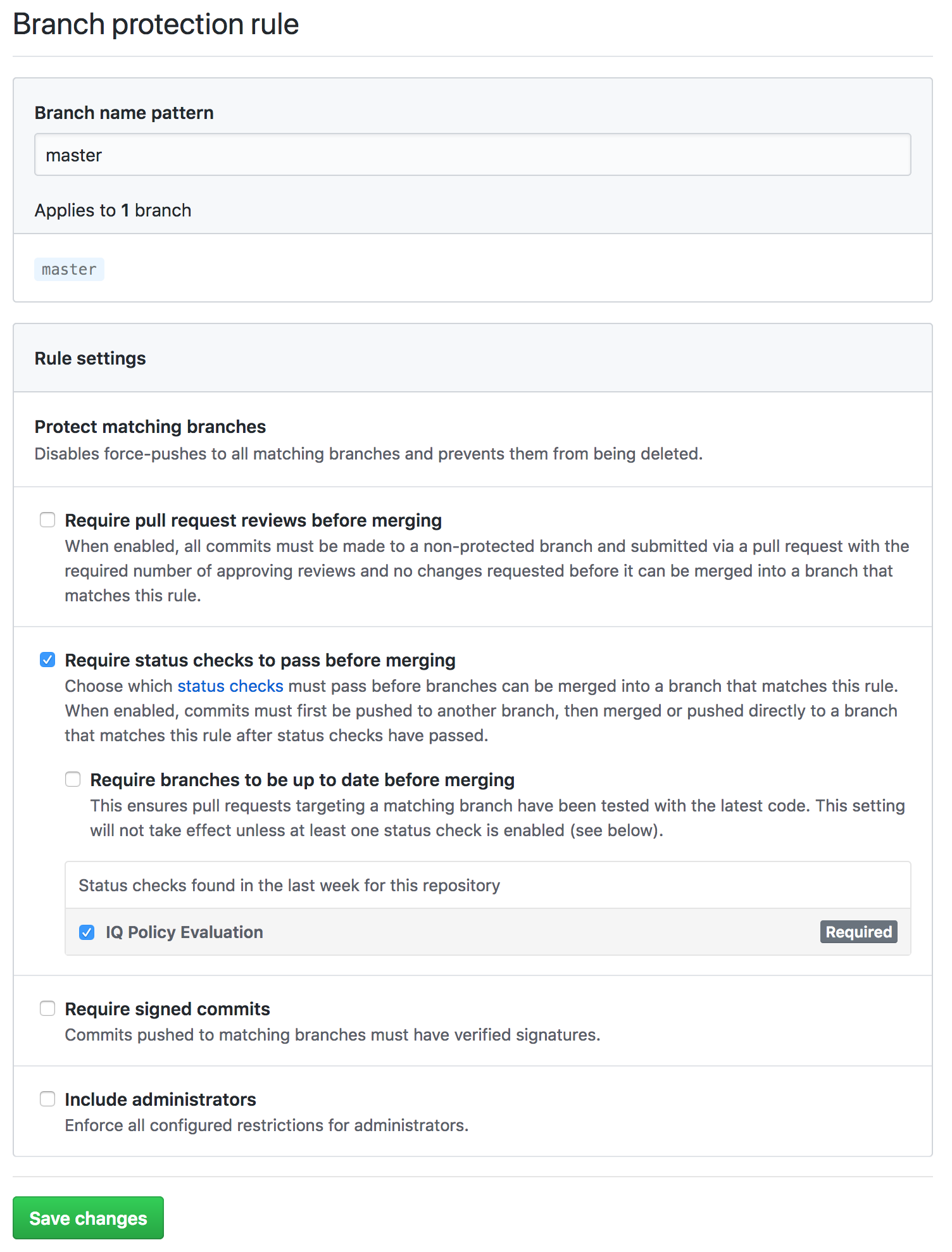
Check to Require status checks to pass before merging.
Check IQ Policy Evaluation.
Save Changes
 |
Note
The IQ Policy Evaluation status check will not appear in the list of status checks found in the last week for this repository until the first policy evaluation status has been added to the repository.
 |