Java Runtime Agent (Experimental)
The Java Runtime Agent detects vulnerable Java methods or classes loaded during runtime to enhance the priority of policy remediation.
Vulnerable components are labeled when the vulnerable classes are loaded and when the vulnerable methods are called during your integration test coverage as part of your build.
Lifecycle policy uses the labels to prioritize the risk found in open-source components by lowering the threat level when not directly referenced by your application during runtime.
Developers better manage their open-source workload with fewer false critical violations and broken builds.
Warning
This is an experimental feature that will change in the future. We do not know the performance impact of running this tool against the Lifecycle at any scale. We insist that this is not run on production environments until this functionality has been hardened.
For assistance or to provide feedback with this experimental feature, contact our data-insights-pm@sonatype.com
How it works
The Java Runtime Agent detects class loading and calls to vulnerable methods then notifies the Lifecycle server using components labels.
The agent detects the loading of a vulnerable method and notifies Lifecycle
The agent also detects and labels when the classes are loaded
The agent labels all components in the application bill of material with a runtime-enabled label
Lifecycle policy constraints will make judgments on these labels in combination with other risk data
For applications with thorough test coverage, every method and class from the open-source components are labeled as being loaded and/or called. Vulnerable methods or classes that are not referenced in the application are deprioritized as less risk.
Learn more about Java Instrumentation and Java Agents
Prerequisites for using Java Runtime Agent
Run the Java Runtime Agent on a non-production server. The agent injects bytecode to intercept calls to vulnerable methods, with minimal impact.
The Lifecycle server must be accessible to the system where the Java Runtime Agent is running
The runtime agent depends on Java 17
The application ID and user access will need to be in the Lifecycle server
Component labels and policy constraints should be configured before running the agent
User tokens and token passwords are recommended
Steps to use the Java Runtime Agent
Download the Java Runtime Agent: runtime-agent-1.0.10.jar
Create component labels and update policies with the runtime prioritization
The Java Runtime Agent uses component labels to trigger custom policies depending on when methods and classes are loaded from vulnerable components.
Add the agent at the root of the project to run during your test coverage build
The jar must be placed in the classpath of the client’s application and run with the Java agent JVM option. The agent is configured using either JVM system properties or environment variables.
View the Report
Go to the application report in Lifecycle. Components found by the agent have labels indicating if the classes are loaded and if the vulnerable method signatures are loaded and/or called.
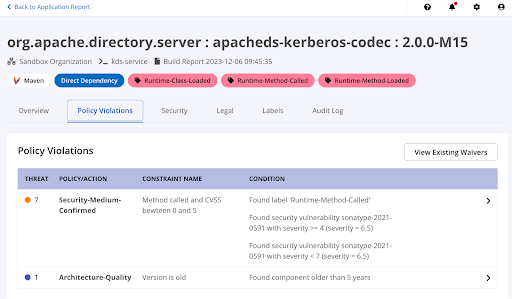
Runtime Java Agent custom policy configuration
The runtime agent uses a custom set of policies to prioritize security vulnerabilities based on the component labels applied to the components during the evaluation. These policies may be loaded using a sample policy set or manually created using the tables below as a reference.
Important
Loading the sample policy set deletes current data in the Lifecycle policy configuration. We insist this policy set is not loaded into production systems as you may lose violation and waiver details for all of your configured applications. All existing policies and license threat groups will be erased.
You may find the sample policy set from this github project: runtime agent policy.
Once you configure the policies and labels, the runtime agent uses them in the following workflow.
The runtime agent applies the
Runtime-Enabledlabel to components.The standard security policies are modified to not trigger when the component has this label. The standard security policies are used when the application is not scanned with the runtime agent.
The
Runtime-Method-Calledlabel is added when the vulnerable method is called during runtime. This triggers the security policies that the vulnerability has beenSecurity-Confirmed. The vulnerability keeps the designated threat level.The
Runtime-Class-Loadedlabel is added when the vulnerable class is loaded during runtime. If theRuntime-Method-Loadedlabel is not added, then theSecurity-Partial-Confirmedpolicies is triggered to identify potential risk. This happens when the vulnerable method is not known at the time.When either the class is not loaded or both the class and methods are loaded but the method is not called, then the violation triggers the
Security-Downgradepolicy to indicate that the application is not at risk do to the vulnerability.
Add the following component labels:
Runtime-Enabled, Runtime-Class-Loaded, Runtime-Method-Loaded, Runtime-Method-Called
Make the following changes to your Lifecycle security policies. Each severity category will need the 4 policies below.
The first is the original policy that needs to be modified while the other 3 must be created new.
The 4 severity categories follow the CVSS v3.0 scoring scale: Critical, High, Medium, Low.
Policy Name | Modifications |
|---|---|
Security-{severity} | With the 'All' operator, add the condition:
The existing |
Security-{severity}-Confirmed | With the 'All' operator, add the condition:
Use the same threat level and severity range condition as the original severity policy. |
Security-{severity}-Partial-Confirmed | With the 'All' operator, add the 2 conditions:
Use the severity range condition as the original severity policy though you may with to reduce the threat level. |
Security-{severity}-Downgrade | The downgrade policy uses to constraints both with the 'All' operator and the same severity range condition as above. The threat level should be lowered depending on your priority as the application is not currently at risk to this vulnerability.
|
Runtime Java Agent with Spring’s Pet Clinic
This demo simulates vulnerable method calls to show what the runtime agent can do. This example uses a public folk of the maven project spring pet clinic to include the agent during integration tests. The steps may be duplicated for other Java projects.
Follow the prerequisites and steps above to prepare your Lifecycle server.
Clone the demo repository for spring-petclinic-runtime-agent
Copy the runtime agent to the level up of the path of the project or adjust the agent config below
../runtime-agent-1.0.10.jar
Update the project
pom.xmlSet the maven plugin configuration in the pom
<properties>sectionAdd/update the following from lines 19-22 in the pom.xml
<clm.maven.plugin.version>2.45.0-01</clm.maven.plugin.version> <clm.serverUrl>http://ec2.compute-1.amazonaws.com:8070/</clm.serverUrl> <clm.serverId>ec2.compute-1.amazonaws.com</clm.serverId> <clm.stage>stage-release</clm.stage>
The maven plugin is added to the plugins section starting at line 157.
<applicationId>${artifactId}</applicationId> <stage>stage-release</stage>This project uses the artifactId
spring-petclinic-runtime-agentas the applicationId to use in the Lifecycle analysis. This application should be added before running the demo.The runtime agent is added to the configuration at line 190 for the
maven-surefire-pluginwhich is used for unit tests in this project. Update the plugin version and Lifecycle server in this section. Credentials should be passed as environment variables.<configuration> <argLine> -javaagent:../runtime-agent-1.0.10.jar -Dsonatype.runtime.agent.enabled=true -Dsonatype.runtime.agent.debugMode=false -Dsonatype.runtime.agent.iq.protocol=http -Dsonatype.runtime.agent.iq.host=ec2.compute-1.amazonaws.com -Dsonatype.runtime.agent.iq.port=8070 -Dsonatype.runtime.agent.iq.user=${env.IQ_USER} -Dsonatype.runtime.agent.iq.password=${env.IQ_PASSWORD} -Dsonatype.runtime.agent.iq.applicationId=${artifactId} -Dsonatype.runtime.agent.isIqApplicationIdPublic=true -Dsonatype.runtime.agent.blockedRunOnStartup=true -Dsonatype.runtime.agent.scanClasspath=false -Dsonatype.runtime.agent.fetchVulnerableClassesFromIQ=true -Dsonatype.runtime.agent.vulnerableMethodDetectionEnabled=true -Dsonatype.runtime.agent.runtimeEnabledLabel=true -Dsonatype.runtime.agent.removeRuntimeLabelsOnStartup=true </argLine> </configuration>NOTE: the
-Dsonatype.runtime.agent.runtimeEnabledLabel=truemay need to be added to the configuration if not present. This is used to set theRuntime-Enabledlabel on all components.
Update your local maven
${HOME}/.m2/settings.xmlwith the clm.serverId property.<settings xmlns="http://maven.apache.org/SETTINGS/1.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/SETTINGS/1.0.0 http://maven.apache.org/xsd/settings-1.0.0.xsd"> <servers> <server> <id>ec2.compute-1.amazonaws.com</id> <username>USER</username> <password>PASSWORD</password> </server> </servers> </settings>
Set environment variable for Lifecycle server authentication
export IQ_USER=USER export IQ_PASSWORD=PASSWORD
Run the agent with integration tests
./mvnw clean package
Confirm components have been labeled in the Lifecycle report
The following components should have been discovered as part of the test coverage and labeled by the runtime agent.
ch.qos.logback:logback-core:1.4.11 ch.qos.logback:logback-classic:1.4.11 org.springframework:spring-core:6.1.1
Manually running the agent
The runtime agent may be used to label components that are called during testing. Run the following command with the required properties updated. You may wish to remove the component labels before running if the previous demo has been done.
java -javaagent:../runtime-agent-1.0.8.jar \
-Dsonatype.runtime.agent.enabled=true \
-Dsonatype.runtime.agent.debugMode=false \
-Dsonatype.runtime.agent.iq.protocol=http \
-Dsonatype.runtime.agent.iq.host=ec2-107-23-150-171.compute-1.amazonaws.com \
-Dsonatype.runtime.agent.iq.port=8070 \
-Dsonatype.runtime.agent.iq.user=${IQ_USER} \
-Dsonatype.runtime.agent.iq.password=${IQ_PASSWORD} \
-Dsonatype.runtime.agent.iq.applicationId=spring-petclinic-runtime-agent \
-Dsonatype.runtime.agent.isIqApplicationIdPublic=true \
-Dsonatype.runtime.agent.blockedRunOnStartup=true \
-Dsonatype.runtime.agent.scanClasspath=false \
-Dsonatype.runtime.agent.fetchVulnerableClassesFromIQ=true \
-Dsonatype.runtime.agent.vulnerableMethodDetectionEnabled=true \
-Dsonatype.runtime.agent.runtimeEnabledLabel=true \
-jar target/*.jarAfter the app starts, navigate to the following URL. It invokes vulnerable method calls and the runtime agent will set the appropriate labels in Lifecycle.
http://localhost:8080/vets.html
The runtime agent will log the action to the console.
Sonatype Runtime Agent - [TIME]: *** Vulnerable CLASS LOADED [className=org/springframework/core/io/buffer/DefaultDataBuffer] by the JVM Sonatype Runtime Agent - [TIME]: Assigning label 'Runtime-Class-Loaded' to component 22d73bef97aff8a74a99 in application: a50576c3cd894d20b24dc0d98eea084b ... Sonatype Runtime Agent - [TIME]: *** Class with vulnerable METHOD LOADED [className=org/springframework/core/io/buffer/DefaultDataBuffer, methodName=split, methodDescriptor=(I)Lorg/springframework/core/io/buffer/DataBuffer;] by the JVM ... Sonatype Runtime Agent - [TIME]: Assigning label 'Runtime-Method-Loaded' to component 22d73bef97aff8a74a99 in application: a50576c3cd894d20b24dc0d98eea084b Sonatype Runtime Agent - [TIME]: *** Vulnerable METHOD CALLED [className=org/springframework/core/io/buffer/DefaultDataBuffer, methodName=split, methodDescriptor=(I)Lorg/springframework/core/io/buffer/DataBuffer;] ... Sonatype Runtime Agent - [TIME]: Assigning label 'Runtime-Method-Called' to component 22d73bef97aff8a74a99 in application: a50576c3cd894d20b24dc0d98eea084b
Samples for Running the Agent
java \
-cp "$CLASSPATH" \
-javaagent:/sample/lib/runtime-agent.jar \
-Dsonatype.runtime.agent.iq.protocol=https \
-Dsonatype.runtime.agent.iq.host=${IQ_HOST} \
-Dsonatype.runtime.agent.iq.port=${IQ_PORT} \
-Dsonatype.runtime.agent.iq.user=${IQ_USER_TOKEN} \
-Dsonatype.runtime.agent.iq.password=${IQ_USER_TOKEN_PASSWORD} \
-Dsonatype.runtime.agent.iq.applicationId=${IQ_APPLICATION_ID} \
-Dsonatype.runtime.agent.scanClasspath=false \
com.sonatype.sample.SampleApplicationjava \
-cp "$CLASSPATH" \
-javaagent:/sample/lib/runtime-agent.jar \
-Dsonatype.runtime.agent.enabled=true \
-Dsonatype.runtime.agent.debugMode=false \
-Dsonatype.runtime.agent.iq.protocol=https \
-Dsonatype.runtime.agent.iq.host=${IQ_HOST} \
-Dsonatype.runtime.agent.iq.port=${IQ_PORT} \
-Dsonatype.runtime.agent.iq.user=${IQ_USER_TOKEN} \
-Dsonatype.runtime.agent.iq.password=${IQ_USER_TOKEN_PASSWORD} \
-Dsonatype.runtime.agent.iq.applicationId=${IQ_APPLICATION_ID} \
-Dsonatype.runtime.agent.isIqApplicationIdPublic=true \
-Dsonatype.runtime.agent.iq.label=Runtime \
-Dsonatype.runtime.agent.iq.connectionTimeoutSeconds=30 \
-Dsonatype.runtime.agent.iq.requestTimeoutSeconds=120 \
-Dsonatype.runtime.agent.blockedRunOnStartup=true \
-Dsonatype.runtime.agent.scanClasspath=false \
-Dsonatype.runtime.agent.vulnerableMethodDetectionEnabled=true \
-Dsonatype.runtime.agent.fetchVulnerableClassesFromIQ=true \
-Dsonatype.runtime.agent.executor.initialDelaySeconds=500 \
-Dsonatype.runtime.agent.executor.delaySeconds=500 \
-Dsonatype.runtime.agent.removeRuntimeLabelsOnStartup=false \
-Dsonatype.runtime.agent.httpMaxThreads=10 \
com.sonatype.sample.SampleApplicationENV SONATYPE_RUNTIME_AGENT_ENABLED true
ENV SONATYPE_RUNTIME_AGENT_DEBUG_MODE false
ENV SONATYPE_RUNTIME_AGENT_IQ_PROTOCOL https
ENV SONATYPE_RUNTIME_AGENT_IQ_HOST ${IQ_HOST}
ENV SONATYPE_RUNTIME_AGENT_IQ_PORT ${IQ_PORT}
ENV SONATYPE_RUNTIME_AGENT_IQ_USER ${IQ_USER_TOKEN}
ENV SONATYPE_RUNTIME_AGENT_IQ_PASSWORD ${IQ_USER_TOKEN_PASSWORD}
ENV SONATYPE_RUNTIME_AGENT_IQ_APPLICATION_ID ${IQ_APPLICATION_ID}
ENV SONATYPE_RUNTIME_AGENT_IS_IQ_APPLICATION_ID_PUBLIC true
ENV SONATYPE_RUNTIME_AGENT_IQ_LABEL Runtime
ENV SONATYPE_RUNTIME_AGENT_IQ_CONNECTION_TIMEOUT_SECONDS 30
ENV SONATYPE_RUNTIME_AGENT_IQ_REQUEST_TIMEOUT_SECONDS 120
ENV SONATYPE_RUNTIME_AGENT_BLOCKED_RUN_ON_STARTUP true
ENV SONATYPE_RUNTIME_AGENT_SCAN_CLASSPATH false
ENV SONATYPE_RUNTIME_AGENT_FETCH_VULNERABLE_CLASSES_FROM_IQ true
ENV SONATYPE_RUNTIME_AGENT_EXECUTOR_INITIAL_DELAY_SECONDS 500
ENV SONATYPE_RUNTIME_AGENT_VULNERABLE_METHOD_DETECTION_ENABLED true
ENV SONATYPE_RUNTIME_AGENT_EXECUTOR_DELAY_SECONDS 500
ENV SONATYPE_RUNTIME_AGENT_REMOVE_RUNTIME_LABELS_ON_STARTUP false
ENV SONATYPE_RUNTIME_AGENT_HTTP_MAX_THREADS 10
java \
$JAVA_OPTS \
-cp "$CLASSPATH" \
com.sonatype.sample.SampleApplicationJava Runtime Agent with Tomcat
Either the agent system properties or environment variables must be used. The properties can be set in CATALINA_OPTS in the shell script usually found in the following location:
${TOMCAT_HOME}/bin/setenv.sh# Using agent system properties
# export CATALINA_OPTS="$CATALINA_OPTS
-Dsonatype.runtime.agent.enabled=true
-Dsonatype.runtime.agent.debugMode=false
-Dsonatype.runtime.agent.iq.protocol=http
-Dsonatype.runtime.agent.iq.host=${IQ_HOST}
-Dsonatype.runtime.agent.iq.port=${IQ_PORT}
-Dsonatype.runtime.agent.iq.user=${IQ_USER_TOKEN}
-Dsonatype.runtime.agent.iq.password=${IQ_USER_TOKEN_PASSWORD}
-Dsonatype.runtime.agent.iq.applicationId=${IQ_APPLICATION_ID}
-Dsonatype.runtime.agent.isIqApplicationIdPublic=true
-Dsonatype.runtime.agent.iq.label=Runtime
-Dsonatype.runtime.agent.iq.connectionTimeoutSeconds=30
-Dsonatype.runtime.agent.iq.requestTimeoutSeconds=120
-Dsonatype.runtime.agent.blockedRunOnStartup=true
-Dsonatype.runtime.agent.scanClasspath=false
-Dsonatype.runtime.agent.vulnerableMethodDetectionEnabled=true
-Dsonatype.runtime.agent.fetchVulnerableClassesFromIQ=true
-Dsonatype.runtime.agent.executor.initialDelaySeconds=500
-Dsonatype.runtime.agent.executor.delaySeconds=500
-Dsonatype.runtime.agent.runtimeEnabledLabel=true
-Dsonatype.runtime.agent.removeRuntimeLabelsOnStartup=false
-Dsonatype.runtime.agent.httpMaxThreads=10
# Using agent environment variables
export SONATYPE_RUNTIME_AGENT_ENABLED=true
export SONATYPE_RUNTIME_AGENT_DEBUG_MODE=false
export SONATYPE_RUNTIME_AGENT_IQ_PROTOCOL=http
export SONATYPE_RUNTIME_AGENT_IQ_HOST=${IQ_HOST}
export SONATYPE_RUNTIME_AGENT_IQ_PORT=${IQ_PORT}
export SONATYPE_RUNTIME_AGENT_IQ_USER=${IQ_USER_TOKEN}
export SONATYPE_RUNTIME_AGENT_IQ_PASSWORD=${IQ_USER_TOKEN_PASSWORD}
export SONATYPE_RUNTIME_AGENT_IQ_APPLICATION_ID=${IQ_APPLICATION_ID}
export SONATYPE_RUNTIME_AGENT_IS_IQ_APPLICATION_ID_PUBLIC=true
export SONATYPE_RUNTIME_AGENT_IQ_LABEL=Runtime
export SONATYPE_RUNTIME_AGENT_IQ_CONNECTION_TIMEOUT_SECONDS=30
export SONATYPE_RUNTIME_AGENT_IQ_REQUEST_TIMEOUT_SECONDS=120
export SONATYPE_RUNTIME_AGENT_BLOCKED_RUN_ON_STARTUP=true
export SONATYPE_RUNTIME_AGENT_SCAN_CLASSPATH=false
export SONATYPE_RUNTIME_AGENT_VULNERABLE_METHOD_DETECTION_ENABLED true
export SONATYPE_RUNTIME_AGENT_FETCH_VULNERABLE_CLASSES_FROM_IQ=true
export SONATYPE_RUNTIME_AGENT_EXECUTOR_INITIAL_DELAY_SECONDS=500
export SONATYPE_RUNTIME_AGENT_EXECUTOR_DELAY_SECONDS=500
export SONATYPE_RUNTIME_AGENT_RUNTIME_ENABLED_LABEL=true
export SONATYPE_RUNTIME_AGENT_REMOVE_RUNTIME_LABELS_ON_STARTUP=false
export SONATYPE_RUNTIME_AGENT_HTTP_MAX_THREADS=10Property | Value |
|---|---|
sonatype.runtime.agent.enabled | Enabled / Disabled (default: true) |
sonatype.runtime.agent.debugMode | Debug mode (default: false) |
sonatype.runtime.agent.iq.protocol | IQ server protocol (default: https) |
sonatype.runtime.agent.iq.host | IQ server host (default: localhost) |
sonatype.runtime.agent.iq.port | IQ server port (default: 8070) |
sonatype.runtime.agent.iq.user | IQ user (default: admin) |
sonatype.runtime.agent.iq.password | IQ password (no default) |
sonatype.runtime.agent.iq.applicationId | IQ application ID (no default) |
sonatype.runtime.agent.isIqApplicationIdPublic | IQ Application ID public or internal (default: true) |
sonatype.runtime.agent.iq.connectionTimeoutSeconds | IQ server connection timeout in seconds (default: 30) |
sonatype.runtime.agent.iq.requestTimeoutSeconds | IQ server REST API request timeout (default: 120) |
sonatype.runtime.agent.blockedRunOnStartup | Block application start until first processing (default: true) |
sonatype.runtime.agent.scanClasspath | Scan classpath for components (default: true) |
sonatype.runtime.agent.fetchVulnerableClassesFromIQ | Fetch vulnerable components/classes from IQ report (default: true) |
sonatype.runtime.agent.vulnerableMethodDetectionEnabled | Method level detection (default: true) |
sonatype.runtime.agent.executor.initialDelaySeconds | Agent schedule - initial delay in seconds (default: 1) |
sonatype.runtime.agent.executor.delaySeconds | Agent schedule - delay between each processing in seconds (default: 3600) |
sonatype.runtime.agent.runtimeEnabledLabel | Set Runtime-Enabled label for all components in the application (Default: false) |
sonatype.runtime.agent.removeRuntimeLabelsOnStartup | false |
sonatype.runtime.agent.httpMaxThreads | 10 |
Environment Variable | Value |
|---|---|
SONATYPE_RUNTIME_AGENT_ENABLED | Enabled / Disabled (default: true) |
SONATYPE_RUNTIME_AGENT_DEBUG_MODE | Debug mode (default: false) |
SONATYPE_RUNTIME_AGENT_IQ_PROTOCOL | IQ server protocol (default: https) |
SONATYPE_RUNTIME_AGENT_IQ_HOST | IQ server host (default: localhost) |
SONATYPE_RUNTIME_AGENT_IQ_PORT | IQ server port (default: 8070) |
SONATYPE_RUNTIME_AGENT_IQ_USER | IQ user (default: admin) |
SONATYPE_RUNTIME_AGENT_IQ_PASSWORD | IQ password (no default) |
SONATYPE_RUNTIME_AGENT_IQ_APPLICATION_ID | IQ appliction ID (no default) |
SONATYPE_RUNTIME_AGENT_IS_IQ_APPLICATION_ID_PUBLIC | IQ Application ID public or internal (default: true) |
SONATYPE_RUNTIME_AGENT_IQ_CONNECTION_TIMEOUT_SECONDS | IQ server connection timeout in seconds (default: 30) |
SONATYPE_RUNTIME_AGENT_IQ_REQUEST_TIMEOUT_SECONDS | IQ server REST API request timeout (default: 120) |
SONATYPE_RUNTIME_AGENT_BLOCKED_RUN_ON_STARTUP | Block application start until first processing (default: true) |
SONATYPE_RUNTIME_AGENT_SCAN_CLASSPATH | Scan classpath for components (default: true) |
SONATYPE_RUNTIME_AGENT_FETCH_VULNERABLE_CLASSES_FROM_IQ | Fetch vulnerable components/classes from IQ report (default: true) |
SONATYPE_RUNTIME_AGENT_VULNERABLE_METHOD_DETECTION_ENABLED | Method level detection (default: true) |
SONATYPE_RUNTIME_AGENT_EXECUTOR_INITIAL_DELAY_SECONDS | Agent schedule - initial delay in seconds (default: 1) |
SONATYPE_RUNTIME_AGENT_EXECUTOR_DELAY_SECONDS | Agent schedule - delay between each processing in seconds (default: 3600) |
SONATYPE_RUNTIME_AGENT_RUNTIME_ENABLED_LABEL | Set Runtime-Enabled label for all components in the application (Default: false) |
SONATYPE_RUNTIME_AGENT_REMOVE_RUNTIME_LABELS_ON_STARTUP | false |
SONATYPE_RUNTIME_AGENT_HTTP_MAX_THREADS | 10 |
The following Component Labels are used to flag components loaded and called by the runtime agent. See Component Labels to add component labels to the Lifecycle instance.
Label | Color | Description |
|---|---|---|
| light-purple | Component available for runtime agent |
| dark-red | The runtime class is loaded by the class loader |
| dark-red | The vulnerable class has a vulnerable method signature |
| dark-red | The vulnerable runtime method was called within the vulnerable class |
The following Policies are used to prioritize the security risk found by the runtime agent.
Policy | Threat | Constraint | CVSS | Labels |
|---|---|---|---|---|
Security-Critical | 10 | Critical risk | > 9 | NOT |
Security-Critical-Confirmed | 10 | Method called | > 9 |
|
Security-Critical-Partial-Confirmed | 9 | Class loaded | > 9 |
NOT |
Security-Critical-Downgrade | 5 | Class not loaded | > 9 |
NOT |
-- 2nd constraint | -- | Method not called | > 9 |
NOT |
Security-High | 9 | High risk | 7 to 9 | NOT |
Security-High-Confirmed | 9 | Method called | 7 to 9 |
|
Security-High-Partial-Confirmed | 8 | Class loaded | 7 to 9 |
NOT |
Security-High-Downgrade | 4 | Class not loaded | 7 to 9 |
NOT |
-- 2nd constraint | -- | Method not called | 7 to 9 |
NOT |
Security-Medium | 7 | Medium risk | 4 to 7 | NOT |
Security-Medium-Confirmed | 7 | Method called | 4 to 7 |
|
Security-Medium-Partial-Confirmed | 6 | Class loaded | 4 to 7 |
NOT |
Security-Medium-Downgrade | 3 | Class not loaded | 4 to 7 |
NOT |
-- 2nd constraint | -- | Method not called | 4 to 7 |
NOT |
Security-Low | 3 | Low risk | < 4 | NOT |
Security-Low-Confirmed | 3 | Method called | < 4 |
|
Security-Low-Partial-Confirmed | 2 | Class loaded | < 4 |
NOT |
Security-Low-Downgrade | 1 | Class not loaded | < 4 |
NOT |
-- 2nd constraint | -- | Method not called | < 4 |
NOT |