Sonatype for Azure DevOps
The Sonatype for Azure DevOps extension integrates with the Azure DevOps pipeline to run policy evaluations in the build workspace. It adds a new step within the build, during which Sonatype IQ Server scans applications to identify any open-source security, license, or quality policy violations. It can be configured to fail the build or generate a warning. This allows the build maintainers to understand the reasons for build failures and plan a remediation strategy.
This extension wraps the Sonatype IQ CLI.
 The Sonatype for Azure DevOps extension is available on the Visual Studio Marketplace.
The Sonatype for Azure DevOps extension is available on the Visual Studio Marketplace.
Main Features
Perform a Sonatype IQ Server policy evaluation on files in the build workspace.
Display scan results within Azure DevOps pipeline report.
Provide a link to a comprehensive Sonatype Lifecycle policy evaluation report indicating violation details and remediation recommendations.
Installation and Configuration
Go to the Installation and Configuration page for steps to install and set up Sonatype IQ in your Azure DevOps pipelines.
Evaluating Policies
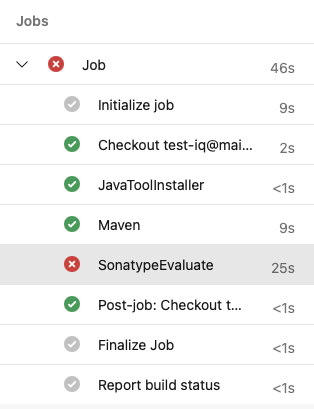
The "SonatypeEvaluate" task appears in the jobs list during a build:
Accessing/Viewing Results
Open SonatypeEvaluate to view a console output with the results of the evaluation:
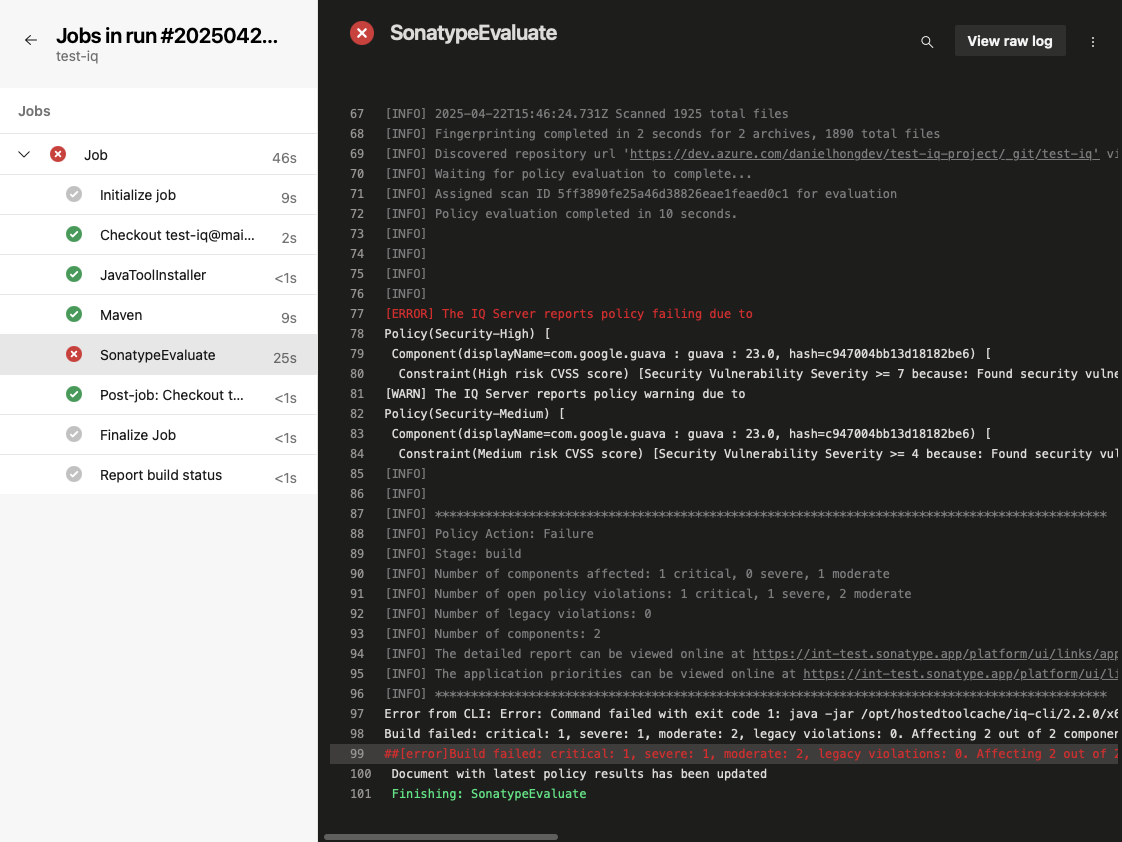
The console output contains a summary of the policy evaluation and a link to the detailed report in IQ Server.
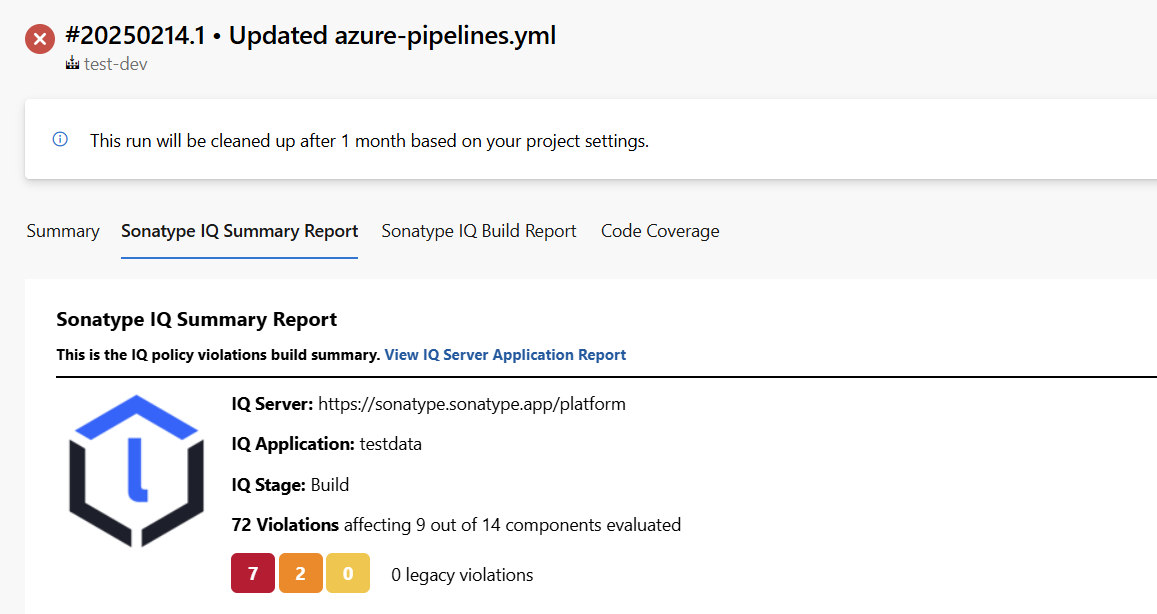
Select the Sonatype IQ Summary Report tab on the build to see a summary report of the policy evaluation for the scanned components:
 |
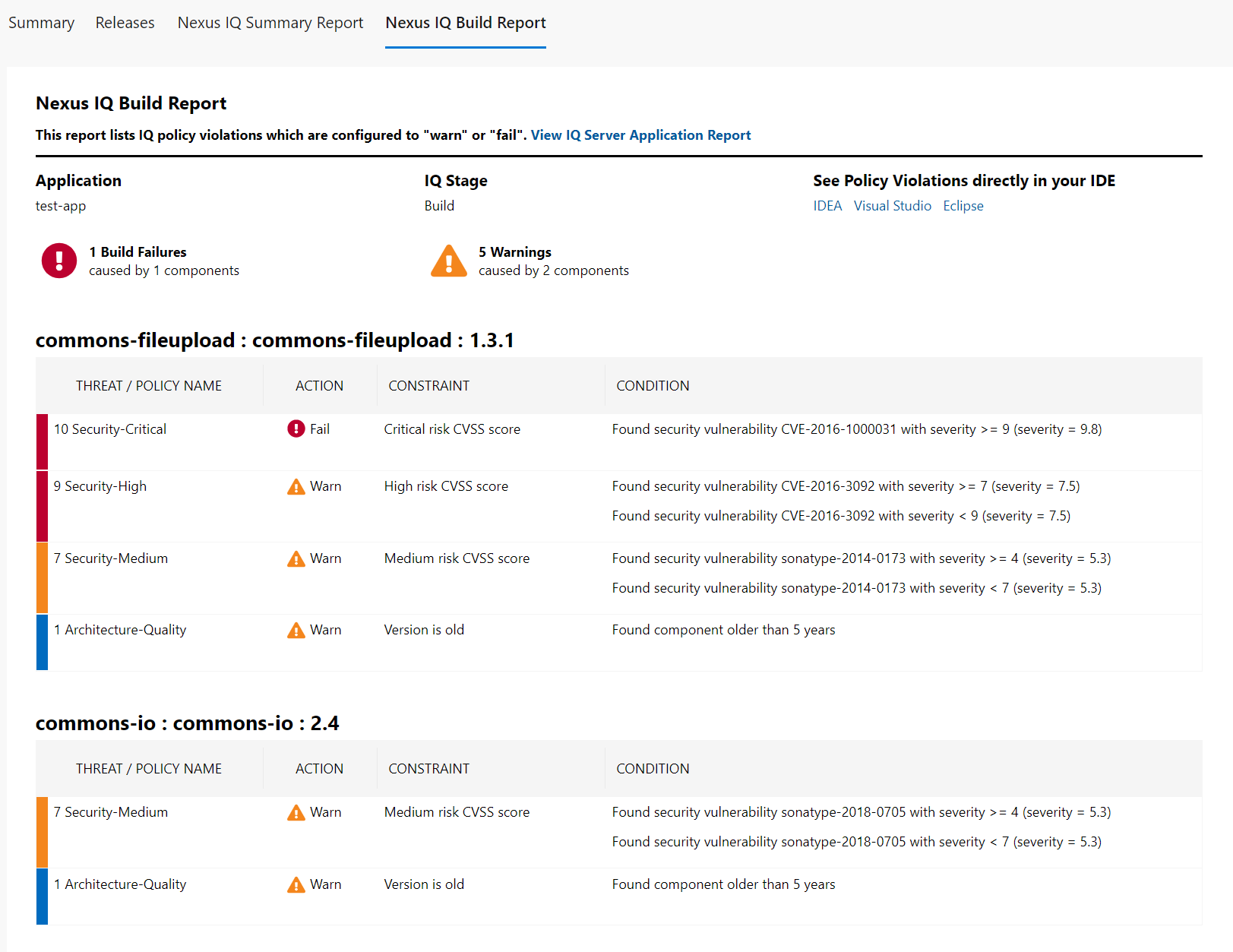
Select the Sonatype IQ Build Report tab on the build for a detailed report with all the components and their correspondent violations:
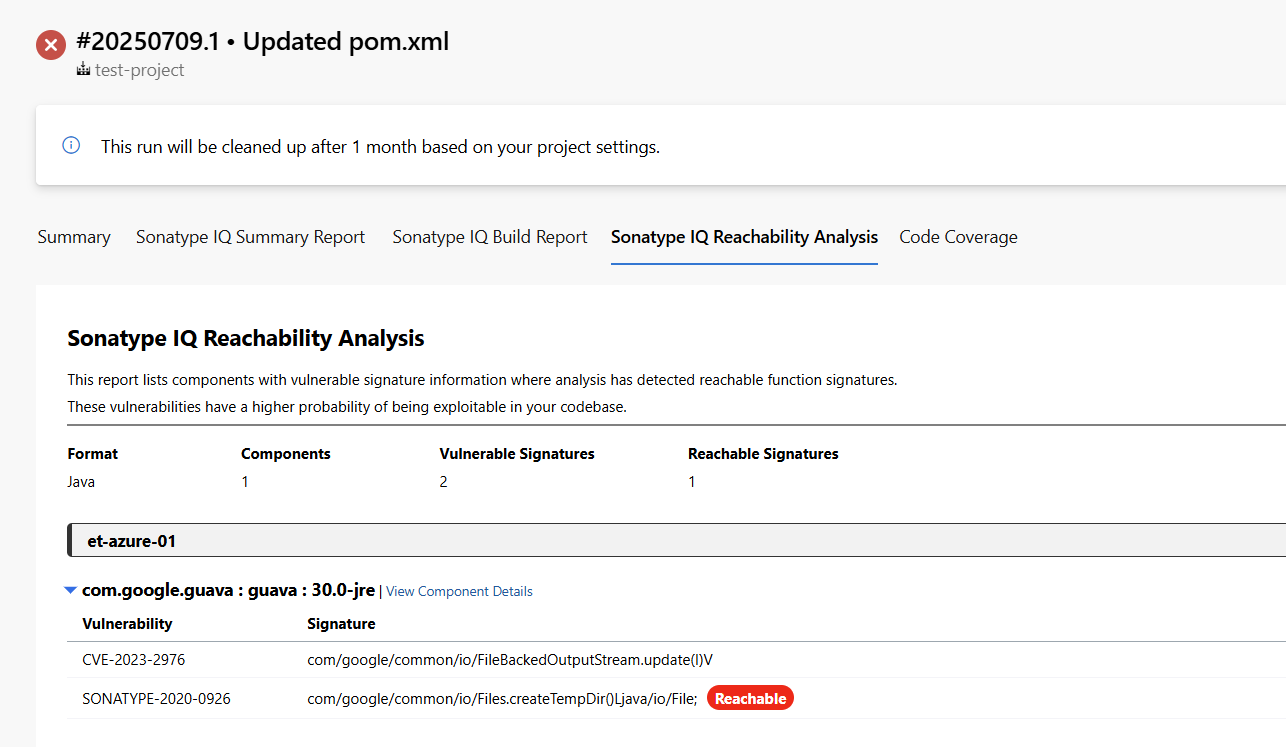
If reachability analysis is enabled, select the Sonatype IQ Reachability Analysis tab for a detailed report of components with vulnerable methods and which of those methods are actually reachable in your code. This tab also lets you navigate, at the component level, between the Reachability Analysis and Build Report tabs.
Note
NexusIqPipelineTask is still supported, but it has been deprecated and may be removed in a future version.
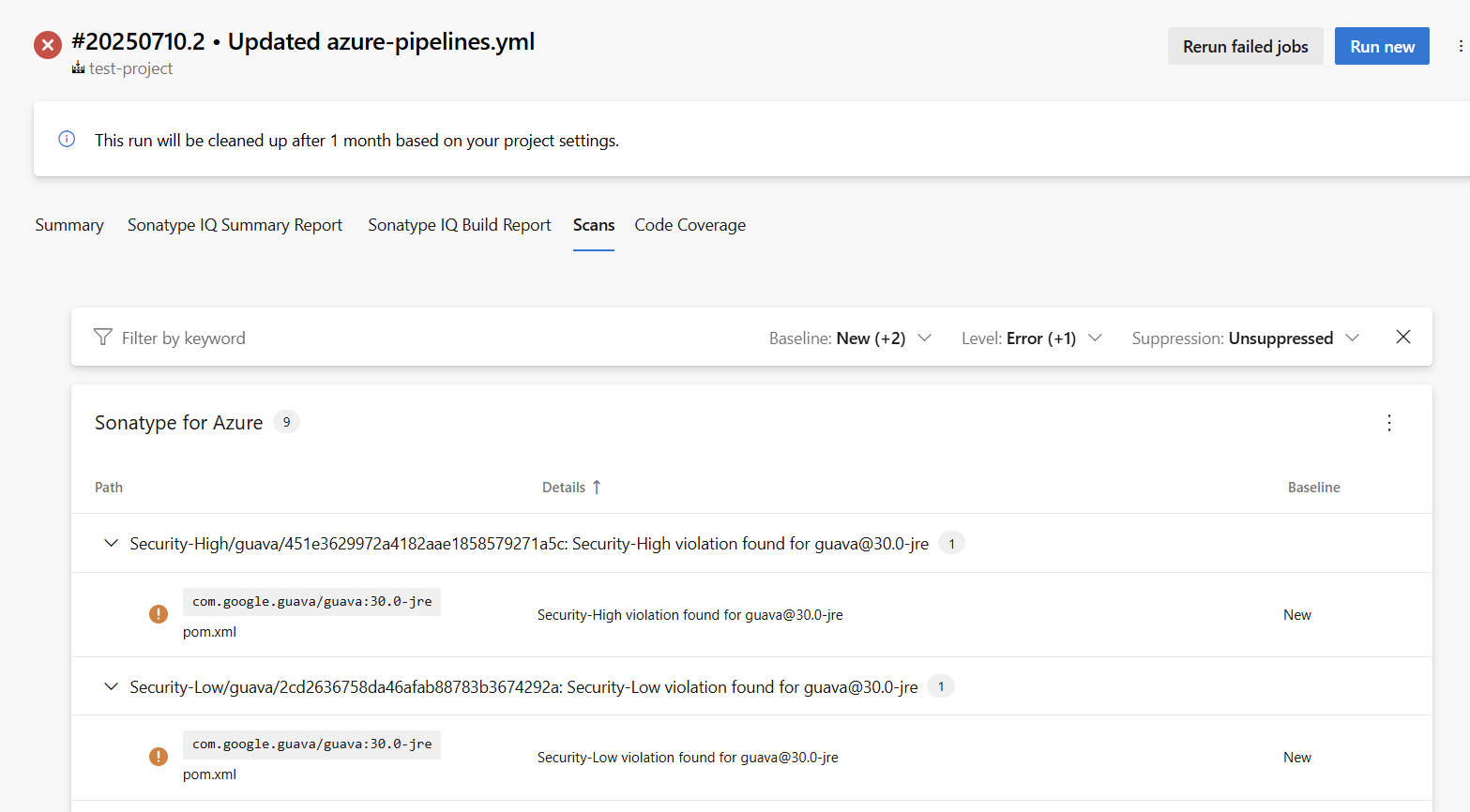
SARIF File Generation
When the sarifFile input parameter is set, the SonatypeEvaluate task will emit a SARIF report named as you specify, containing all identified vulnerabilities. The path to the generated file is exposed via the task’s sarifFile output variable, which you can reference in downstream steps.
You can then publish that SARIF file as a pipeline artifact with the PublishBuildArtifacts task and view it in your build summary by installing the SARIF SAST Scans Tab extension, which adds a Scans tab to the build results UI.
Here’s an example pipeline snippet:
- task: SonatypeEvaluate@2
name: sonatypePolicyEvaluation
inputs:
nexusIqService: 'IQ-SERVICE-CONNECTION'
applicationId: 'app-01'
stage: 'Build'
scanTargets: '**/target/*.jar'
sarifFile: 'result.sarif'
- task: PublishBuildArtifacts@1
inputs:
PathtoPublish: '$(sonatypePolicyEvaluation.sarifFile)'
ArtifactName: 'CodeAnalysisLogs'
publishLocation: 'Container'
condition: succeededOrFailed()After your pipeline completes, open the Scans tab on the build summary to review the vulnerabilities in the SARIF report.
Add dashboard widgets for Sonatype IQ
For ease of use, the following widgets for Sonatype IQ can be added to the Azure DevOps dashboard.
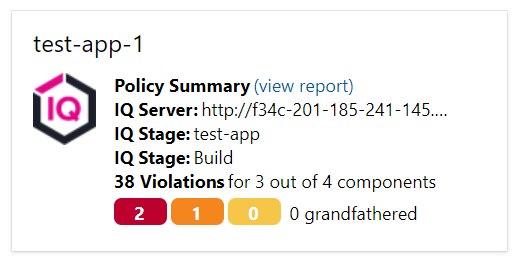
Sonatype IQ Policy Evaluation widget: shows the policy evaluation results for the latest build.
Trends for Sonatype IQ Policy Evaluation: shows a historical trend of Sonatype IQ Policy evaluations of the last 5 builds.
How to add Sonatype IQ widgets to the Azure DevOps Dashboard:
Go to "Overview" → "Dashboards" and click the "Edit" button.
On the right-hand side, under "Add Widget", search for "Sonatype IQ":

Select the appropriate widget and click the "Add" button at the bottom right corner of the page. Click the "Done editing" button.
Sonatype IQ widget now displays the dashboard showing the results summary for the latest build and the historical summary for the last 5 builds.
Running Sonatype IQ in Azure Self-Hosted Agents
If you’re using an HTTP proxy within your infrastructure and Azure self-hosted build agents, you can specify the Azure DevOps agent’s proxy settings. These settings will then be automatically applied when connecting to IQ. For more information, refer to Microsoft’s documentation.
In the Azure-provided sample command:
./config.sh --proxyurl http://127.0.0.1:8888 --proxyusername "myuser" --proxypassword "mypass"
This would appear in the scan output as it is passed through to the IQ scan client:
... -p 127.0.0.1:8888 -U myuser:*** ...
Fetch SBOM Task Properties
Fetch SBOM is a task for retrieving an SBOM (Software Bill of Materials) file associated with a previous Lifecycle evaluation. It supports both the CycloneDX and SPDX standards. For configuration steps, see the Installation and Configuration page.
Parameter | Required/Optional | Description |
|---|---|---|
| Required | Sonatype IQ service connection to use. |
| Required | Must match the |
| Required | Scan identifier produced by the Evaluation step. Pass it as |
| Required | SBOM standard: |
| Optional | Version of the SBOM standard. Available CycloneDX versions: |
| Optional | Output file format: |
| Optional | Accept self-signed TLS certificates from IQ Server. Default: |
Note
The reference name you assign to each task (e.g., sonatypePolicyEvaluation, sonatypeFetchSbomTask) becomes the prefix for its output variables. Adjust the variable references accordingly.
Reachability Analysis
See Reachability Analysis with Sonatype for Azure DevOps for how to enable Reachability in Java/JVM builds covering required permissions, the parameters, a usage example, and the default entry point strategy with tips on narrowing scope via namespaces.
Git/jgit Configuration and Permissions
The Azure DevOps extension uses the Sonatype IQ CLI to perform scans.
During the scanning process, the CLI uses Git to detect the repository URL, commit hash, and branch name.
If native Git is available on the build agent, the CLI will use it; otherwise, it falls back to jgit (Java-based Git). When jgit is used, it attempts to create configuration files in the current user’s $HOME directory. If it doesn’t have permission to do so, you may see ERROR-level log messages—these are not critical to the scan and can be safely ignored. To avoid them, make sure native Git is installed on the build agent, or set the XDG_CONFIG_HOME environment variable to a directory that the build agent user can write to.