Role Management
Roles provide sets of permissions that grant access to functionality in the user interface, through the integrations, and when using the REST APIs. Permissions are granted by assigning users or groups to the system roles or at the various levels in the organizational hierarchy: root organization, repository managers, organizations, and applications.
Roles are assigned to individual users or groups managed by your identity managing tools such as SAML or LDAP.
Authenticated Users Group
Lifecycle has a built-in group called Authenticated Users that contains any authenticated user.
Role Hierarchy
The scope of permissions granted to a role is governed by where that role is assigned in the system hierarchy.
In the Lifecycle solution roles are assigned at the following levels:
Root Organization - Grants permissions to all organizations, applications, and repositories.
Organization - Grants permissions to that organization and all organizations and applications under it in the hierarchy.
Application - Grants permissions only to the individual application.
The Repository Firewall solution has additional entities to which roles can be assigned:
Repository Managers - Grant permissions to the configuration for the repository manager and all of the repositories managed there.
Repositories - Grants permissions to specific repository reports.
Built-in Roles
The built-in roles will meet most common use cases. Custom roles may be created to match your organizational requirements.
Built-in Admin User
The built-in Admin user account is assigned to both the System Administrator and Policy Administrator roles.
Administrator Roles
System Administrator - Manages system configuration and users, which includes LDAP and product license management as well as the ability to assign other users to the System Administrator role.
Policy Administrator - Provides full control over organizations, applications, policies, policy violations, and custom roles.
Permissions | System Administrator | Policy Administrator |
|---|---|---|
Administrator Permissions | ||
Edit System Configuration and Users |
|
|
Edit Custom Roles |
|
|
View All Roles |
|
|
Lifecycle Permissions | ||
Edit Proprietary Components |
|
|
Claim Components |
|
|
Edit IQ Elements |
|
|
View IQ Elements |
|
|
Edit Access Control |
|
|
Evaluate Applications |
|
|
Evaluate Individual Components |
|
|
Add Applications |
|
|
Manage Automatic Application Creation |
|
|
Manage Automatic Source Control Configuration |
|
|
Remediation Permissions | ||
Waive Policy Violations |
|
|
Change Licenses |
|
|
Change Security Vulnerabilities |
|
|
Review Legal obligations for component licenses |
|
|
Organizational Roles
Owner - Manages assigned organizations, applications, policies, and policy violations.
Developer - Views all information for their assigned organization or application.
Application Evaluator - Minimum access to scan the application via the CI integrations. Evaluate applications and view policy violation summary results within the CI.
Component Evaluator - Evaluates individual components and views policy violation results for a specified application within the IDE integrations.
Legal Reviewer - Reviews legal obligations for component licenses.
Permissions | Owner | Developer | Application Evaluator | Component Evaluator | Legal Reviewer |
|---|---|---|---|---|---|
Administrator Permissions | |||||
Edit System Configuration and Users |
|
|
|
|
|
Edit Custom Roles |
|
|
|
|
|
View All Roles |
|
|
|
|
|
Lifecycle Permissions | |||||
Edit Proprietary Components |
|
|
|
|
|
Claim Components |
|
|
|
|
|
Edit IQ Elements |
|
|
|
|
|
View IQ Elements |
|
|
|
|
|
Edit Access Control |
|
|
|
|
|
Evaluate Applications |
|
|
|
|
|
Evaluate Individual Components |
|
|
|
|
|
Add Applications |
|
|
|
|
|
Manage Automatic Application Creation |
|
|
|
|
|
Manage Automatic Source Control Configuration |
|
|
|
|
|
Remediation Permissions | |||||
Waive Policy Violations |
|
|
|
|
|
Change Licenses |
|
|
|
|
|
Change Security Vulnerabilities |
|
|
|
|
|
Review Legal obligations for component licenses |
|
|
|
|
|
Edit Proprietary Components
Proprietary components are those that are unique to your organization. Lifecycle will flag them as "Unknown" components. This permission allows you to configure these components to change the match state to "Exact" during the next scan or re-evaluation.
Claim Components
This permission allows you to alter the match state of the component from the Application Composition Report.
Edit IQ Elements
Edit IQ Elements is a wide-reaching permission that enables most add/edit/delete operations that are not governed by a more specific permission for the following items:
organizations
applications, except adding them
application categories
policies
continuous monitoring
policy violation grandfathering (As part of our inclusive language initiatives, we have renamed this feature to Legacy Violations starting with release 167.)
license threat groups
component labels
data retention policies
quarantined repository components
repositories
source control entries
View IQ Elements
View IQ Elements grants read-only access to most properties of a respective organization/application/repository to view the current configuration and policy evaluation state.
View IQ Elements is the minimum permission required for users to be able to browse organization/application/repository-related web pages, including application composition reports.
Edit Access Control
This permission allows you to manage access control for applications, organizations, and repositories only. For managing all other access controls, use Edit IQ Elements permission. All roles that have Edit IQ Elements permission also have the 'Edit Access Control' permission.
Evaluate Applications
This permission lets users evaluate or scan applications. Users also need this permission to the target application.
Evaluate Individual Components
This permission lets users evaluate individual components. It's intended for use with our IDE integrations such as Intellij or Eclipse. This permission is also required to evaluate components processed by Sonatype Repository Firewall at the repository level.
Add Applications
This permission allows users to create or import applications (using Automatic Source Control Configuration feature) within the scope of an organization.
Manage Automatic Source Control Configuration
This permission allows users to enable or disable automatic source control configuration using the Automatic Source Control Configuration system preference.
Waive Policy Violations
This permission allows users to:
Release quarantined components by waiving policy violations
Unblock components to go ahead with a build or release
Lower violation counts to reduce noise
Change Licenses
This permission allows users to override the effective license at the component level and set its status to open (default), acknowledged, overridden, selected or confirmed.
Change Security Vulnerabilities
This permission allows users to change the status of a security vulnerability to open, acknowledged, applicable or confirmed, at the component level.
Review Legal Obligations for Component Releases
This permission allows users to review licenses at the application/component level.
Viewing Roles
Users need to be assigned to the System Administrator role to manage roles.
Select the System Preferences icon on the Lifecycle toolbar.
Select Roles
 |
Built-in Role Permissions
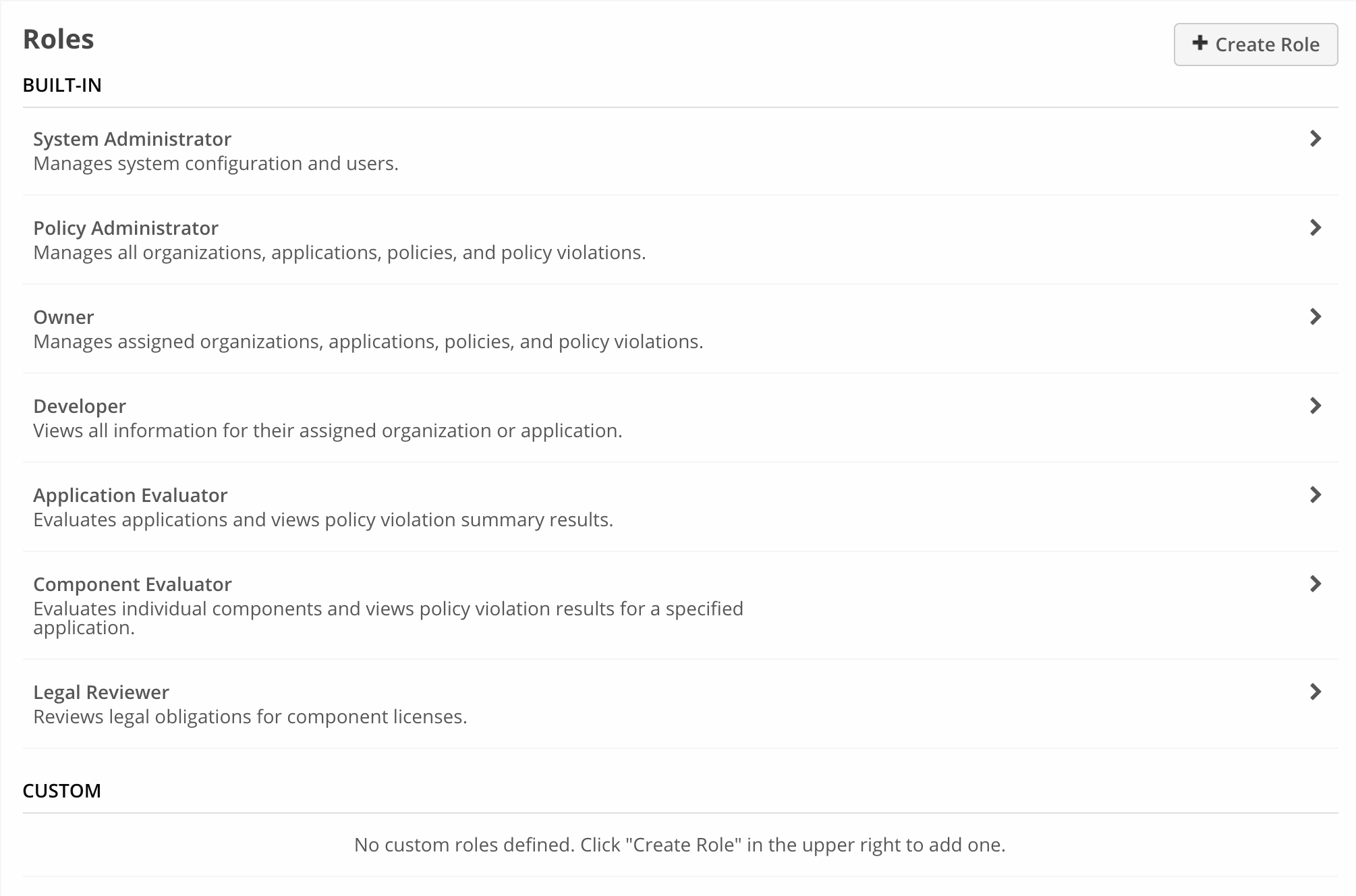
To view permissions assigned to built-in roles:
Click the System Preferences icon on the Lifecycle toolbar.
Click Roles on the System Preferences submenu. A list of roles is displayed.
Click the arrow next to a specific role to view its details and permissions.
The built-in roles have the permissions shown below.
Managing Administrator Roles
To manage administrator roles, you must authenticate as a user assigned to the System Administrator role.

Viewing Administrator Roles
Click the System Preferences icon
Click Administrators. A list of administrator roles and assigned members is displayed.
Assigning Users to Administrator Roles
Click the System Preferences icon
Click Administrators. The administrator's view is displayed.
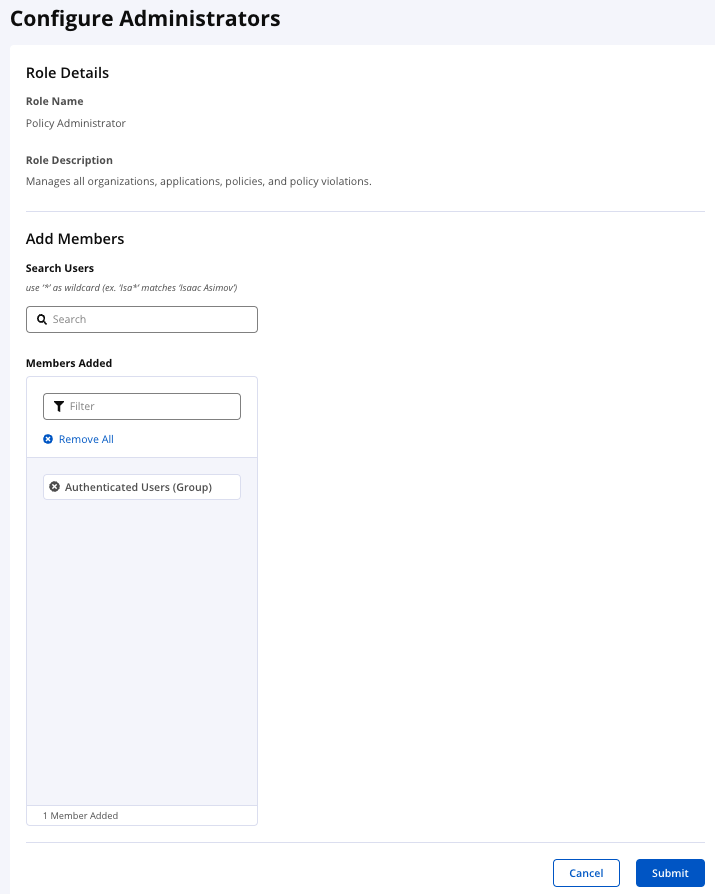
Click the row for the role to which you want to add users. The administrator's view is updated to display the role and its members.
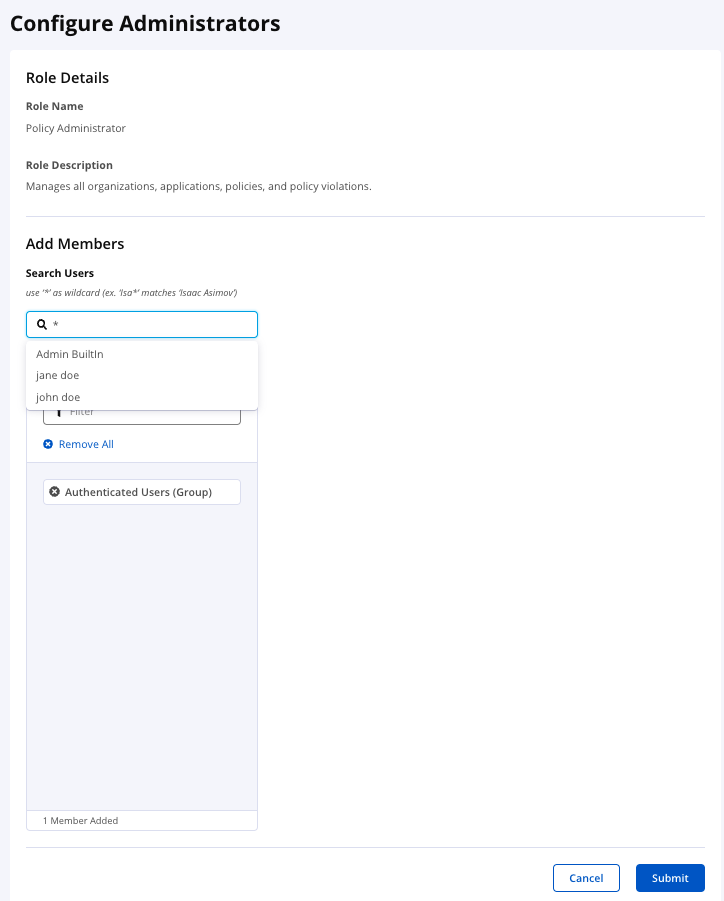
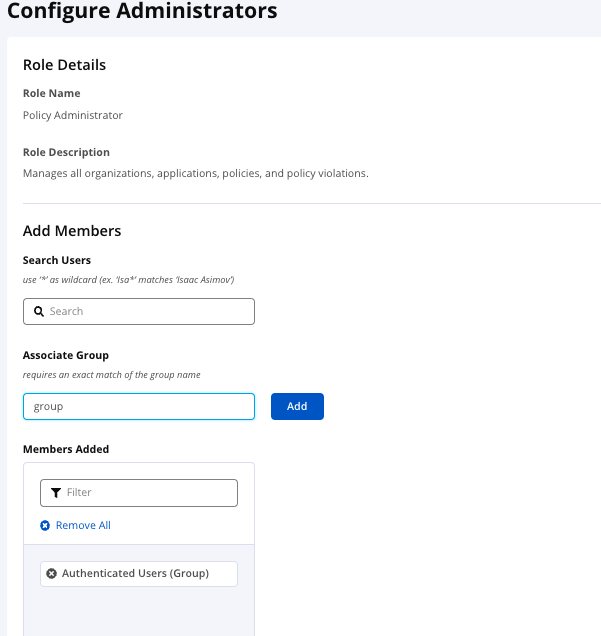
Search for a user you want to add to the role by entering a full name or part of a name with an asterisk into the search box, the search list will be updated automatically as you type in. You can use an asterisk as a wildcard at the beginning or end of a character string. For example, isa*, *mov, and *asi* will all match the name, "Isaac Asimov." Any matching names are displayed in the Available list.
To add a user to the role, click a user’s name in the dropdown menu with the results of the search, the name will be added to the Members Added list.
To remove a user from a role, click a user’s name in the Members Added.
You can filter the list of Added Members with the filter field, the list will be updated automatically as you type in.
If you have LDAP configured, and you don't have set the Group Search Enabled option, you can add groups by name without fetching them in the search field, just type in the name of the group in the Associate Group field and click add.
Click Submit to save the role assignment(s).
 |
 |
 |
Managing Organizational Roles
To manage organizational roles, you must log in to Lifecycle as a user assigned to the Policy Administrator role, Owner role, or a custom role that has the Edit Access Control permission. By default, the built-in Admin user account is assigned to the Policy Administrator role.
Viewing Organizational Role Assignments
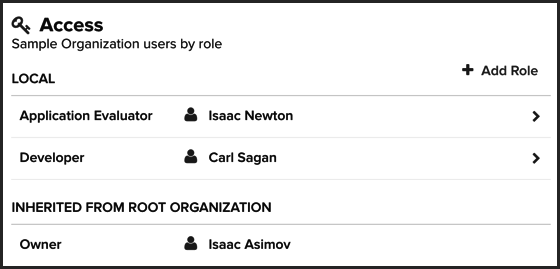
To view organizational role assignments:
Click the Organization & Policies icon
Select an entity (organization, application, or Repository) in the sidebar.
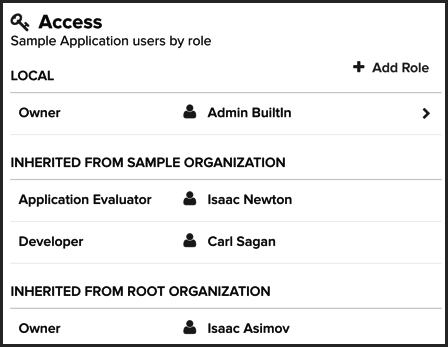
Click Access in the menu bar at the top of the page to scroll to the Access section. Assigned roles are grouped as follows:
Local - Role assignments with a scope that’s specific to the selected organization or application.
Inherited - Role assignments derived from an organization that’s higher in the system hierarchy than the currently selected organization or application.
 |
Assigning Users to Organizational Roles
To assign a user to an organizational role:
Click the Organization & Policies icon
Select an entity (organization, application, or Repositories) in the sidebar.
Click Access in the menu bar at the top of the page to scroll to the Access section.
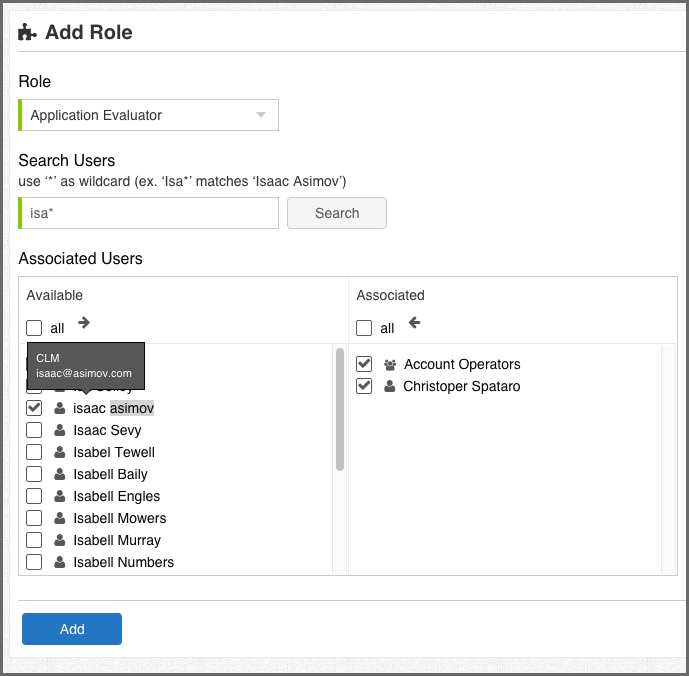
Click the Add Role button. The Access editor is displayed.
In the Role box, select a user role.
In the Search Users box, search for a user by entering a full name or part of name with an asterisk, then click Search. You can use an asterisk as a wildcard at the beginning or end of a character string. For example, isa*, *mov, and *asi* will all match the name, "Isaac Asimov." Any matching names are displayed below in the Associated Users list.
In the Associated Users list, select a user in the Available column on the left, then click the right arrow button to move the user to the Associated column on the right. If you accidentally add a wrong user, select the user in the Associated column, then click the left arrow to return the user to the Available column.
Click Add.
Note
If you integrated an LDAP server with Lifecycle, the LDAP users and groups are also displayed in the search results. If you hover over a list item, the LDAP realm and email address are displayed when available.
 |
Tip
If you want to continue adding role assignments for the selected organization, application or Repositories, click Add Role in the sidebar.
Editing Organizational Role Assignments
To edit an organizational role assignment:
Click the Organization & Policies icon
In the sidebar, select the entity (organization, application or Repositories) in which the role is assigned.
Click Access in the menu bar at the top of the page to scroll to the Access section.
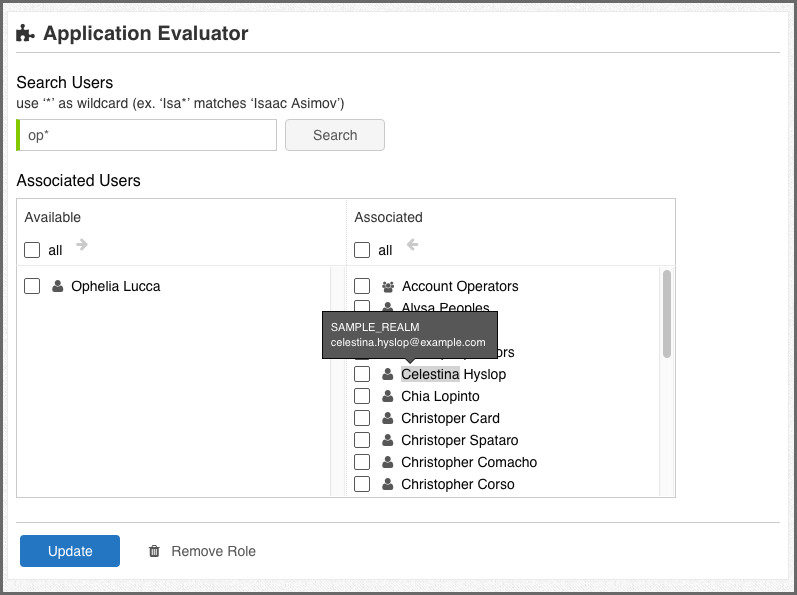
Click a listed role (or the chevron next to its name) to display the Access editor.
In the Search Users box, search for a user by entering a full name or part of name with an asterisk, then click Search. You can use an asterisk as a wildcard at the beginning or end of a character string. For example, isa*, *mov, and *asi* will all match the name, "Isaac Asimov." Any matching names are displayed below in the Associated Users list.
In the Associated Users list, you can add a user to a role by selecting the user in the Available column on the left and clicking the right arrow button to move the user to the Associated column. To remove a user from a role, select the user in the Associated column, then click the left arrow to return the user to the Available column.
Click Update.
Note
If you integrated an LDAP server with Lifecycle, the LDAP users and groups are also displayed in the search results. If you hover over a list item, the LDAP realm and email address are displayed when available.
 |
Tip
If you want to continue adding role assignments for the selected organization, application or Repositories, click Add Role in the sidebar.
Removing Organizational Role Assignments
To remove organizational role assignments:
Click the Organization & Policies icon
In the sidebar, select the entity (organization, application or Repositories) in which the role is assigned.
Click Access in the menu bar at the top of the page to scroll to the Access section.
Click a listed role (or the chevron next to its name) to display the Access editor.
Click the Remove Role button, then click Continue to remove the role or click Cancel to keep the role.
Note
This is the equivalent of removing or disassociating all users from a role.
Custom Roles
Custom roles allow you to fine-tune security permissions for different users. You must have permission to Edit Custom Roles if you want to create a custom role.
The following permissions are available for custom roles:
Administrator Roles:
View All Roles
Edit Proprietary Components
Organizational Roles:
Claim Components
Edit IQ Elements
View IQ Elements
Edit Access Control
Evaluate Applications
Evaluate Individual Components
Add Applications
Manage Automatic Application Creation
Manage Automatic Source Control Configuration
Waive Policy Violations
Change Licenses
Change Security Vulnerabilities
Review Legal obligations for components licenses
Tip
To achieve desired behavior in the user interface, you may need to assign View IQ Elements along with other permissions. For example, to allow a user to create applications in an organization but not edit the organization, you should add View IQ Elements and Add Applications to the role.
To create a custom role:
Click the System Preferences icon and then click Roles.
Click the Create Role button.
Enter a name and description for the role.
Click the Can/Cannot slider to enable or disable permissions as desired.
Click the Save button.
Note
Whenever a user assigned to a custom role with Add Applications permission creates an application, that user is automatically assigned to the Owner role for that application.
Assigning Groups to Roles without Searching
If you have an LDAP configuration that uses dynamic groups and disabled group search, then the Access editor will have an additional section called Associate Group. You can use this section to enter manually a group name and add it to a role.
To assign groups to roles without searching:
Click the Organization & Policies icon
In the sidebar, select an entity (organization, application or Repositories).
Click Access in the menu bar at the top of the page to scroll to the Access section.
Open the Access editor by clicking Add Role or the chevron next to an existing role.
In the Associate Group box, enter the group name. The text must be an exact match.
Click Add. The group name is added to the Associated column without performing a search of users and groups.
Role Assignments
To view role assignments:
Click the Organization & Policies icon
Select an organization or application in the sidebar. A page of customizable settings is displayed.
Click Access in the menu bar at the top of the page to scroll to the Access section. Users are displayed by their assigned roles for the selected entity (i.e. organization or application). The information is grouped by where the role assignments were made: locally in the current entity or inherited from an entity higher in the system hierarchy.
 |