Legacy Violations
To streamline the process of onboarding new applications with existing policy violations, the Legacy Violation feature allows you to defer policy violations to remediate later. When enabled for an application or an application's parent organization, eligible policy violations are be marked as Legacy Violations on the first evaluation of an application. Legacy Violations will not be treated as active violations, no notifications will be sent and Lifecycle will not take policy actions against them. If desired, these legacy violations can also be revoked to return to normal policy violation behavior.
What are Legacy Violations?
This Lifecycle feature lets you acknowledge existing issues found in newly onboarded applications. The main objective of Legacy Violations is to provide an easier route to automated enforcement of new risks, which is difficult to achieve if there’s a large backlog of existing issues. When violations are marked as Legacy, existing violations won’t cause a policy action, but if a new violation is introduced the policy action is still applied.
Here’s an example of how new application onboarding might work with Legacy Violations enabled:
A policy administrator configures policies with a build action of fail and enables Legacy Violations at the root organization level.
An application is scanned for the first time, showing components A and B, revealing violations A2 and B2. Since Legacy Violations is enabled, these violations are automatically deferred. No policy action is taken during this first scan, allowing the build to pass.
Component C is added later or upgraded to a newer version, and that shows new violations and fails the build.
In the above example, the first evaluation is used to assess an application. Although there are violations, they represent existing risks and are marked as Legacy Violations. The build continues to pass with these violations until the new component is added revealing new violations that fail the build.
Note
By default, Legacy Violations do not defer violations of severity 9 or 10 because these violations represent significant risks.
Difference Between Waivers and Legacy Violations
A good way to think about Legacy Violations is that it lets you exempt existing risks you had before adopting Lifecycle. On the other hand, waivers are a way to individually exempt new risks after Lifecycle is deployed.
With Legacy Violations enabled, you won’t get overwhelmed with violations, but you will be aware that the violations exist. It’s different from waiving in this way. Waivers acknowledge a variance in policy for a specific component, whereas Legacy Violations is a way to acknowledge the existing state of the application prior to onboarding with Lifecycle. With Legacy Violations, you can easily get to a logical, approachable scope when you get started and have time to remediate risk.
Configuring Legacy Violations for Organizations and Applications
By default, Legacy Violations feature is disabled on the Root Organization, and this setting is inherited by all child organizations and applications. However, the default Legacy Violation configuration for the Root Organization also permits overrides by child organizations and applications, so this setting can be overridden. You can enable or disable Legacy Violations for an organization or an application if there are no inherited restrictions on overriding the setting.
To enable or disable Legacy Violations for an application or organization:
Select the organization or application that you wish to edit from the sidebar.
Scroll down to the Policies sectionand click on Legacy Violations .
The options will vary slightly depending on whether you are editing the Root Organization, a child organization, or an application.
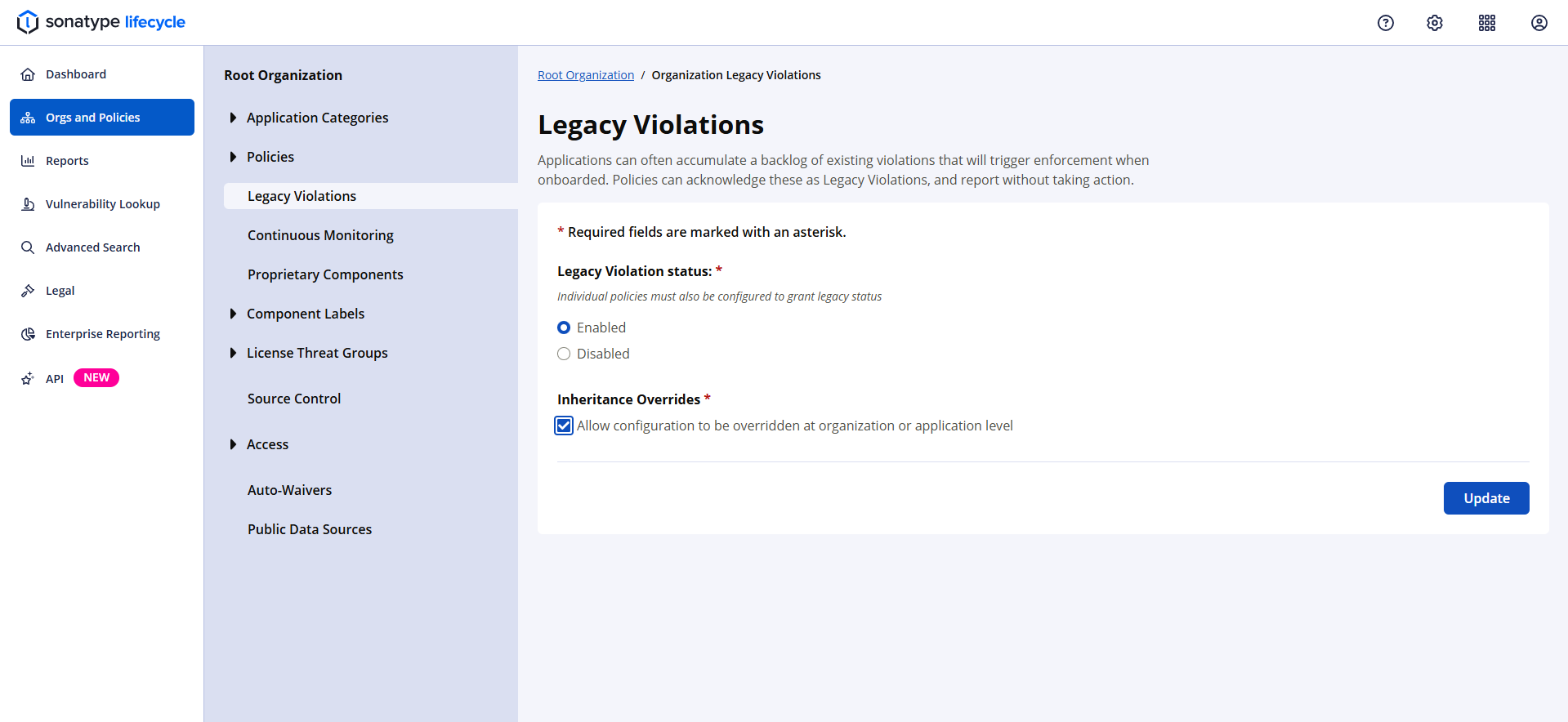
For the Root Organization, you can select whether or not Legacy Violation status is enabled or disabled, and whether or not child organizations and applications can override this setting.
For child organizations, you can select whether or not Legacy Violation status is enabled, disabled, or inherited from the parent, as well as whether or not applications can override this setting.
For applications, you can select whether or not Legacy Violation status is enabled or disabled.
If a parent organization has disabled overrides then the settings from that parent will be inherited and the user interface for editing the configuration will be disabled with a message indicating the reason.
Configuring Legacy Violations for Policies
You will also need to enable or disable Legacy Violations on individual policies. To do so, follow the directions in Configuring Policies for editing a policy.
For new installs, Legacy Violations are enabled in the reference policies for threat levels less than or equal to 8.
Note
For any policy violations to be managed as Legacy Violations, it must also be enabled by configuring the application or parent organization.
Viewing Legacy Violations
Information regarding Legacy Violations is displayed in several locations within the Sonatype Lifecycle.
Application Composition Report
The number of Legacy Violations will be displayed in the Application Composition Report.
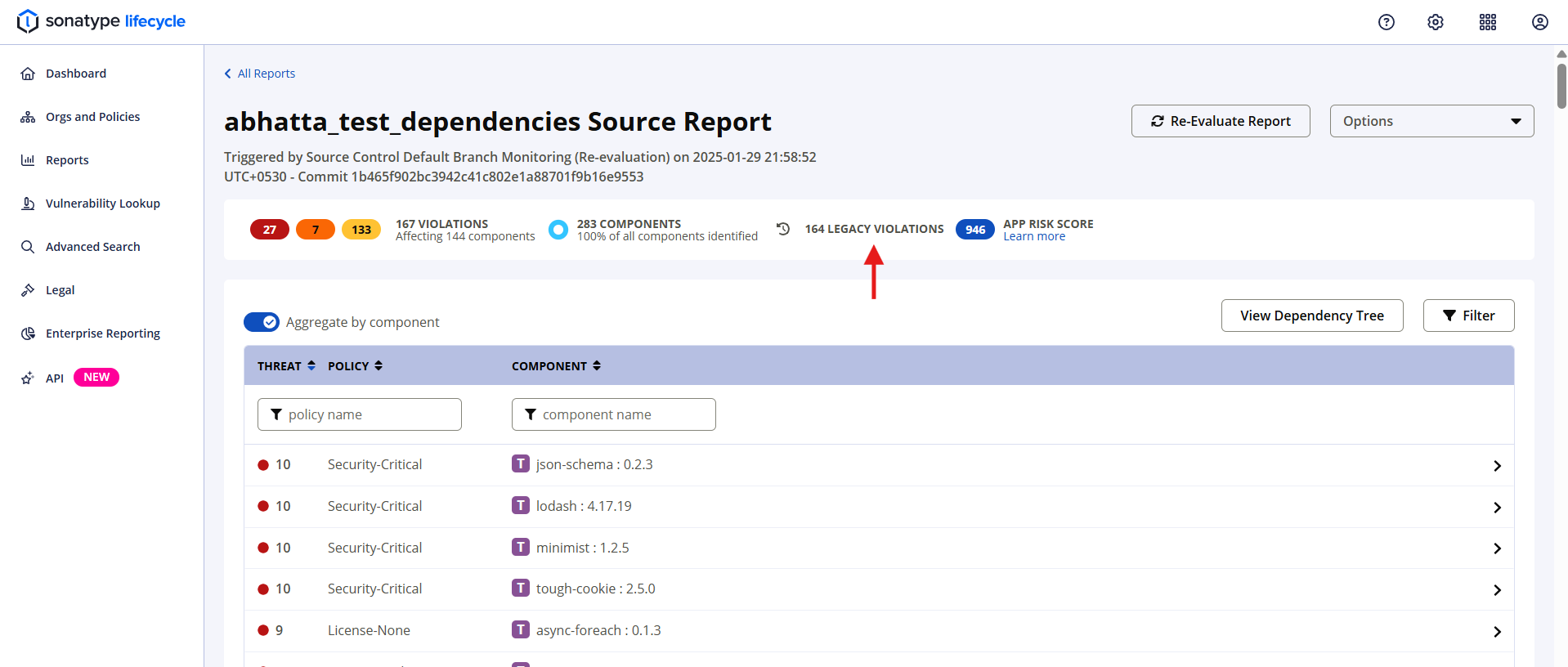
Individual legacy violations are also displayed on the Policy Violations table when reviewing a report. The Legacy filter can be used to limit results to Legacy Violations.
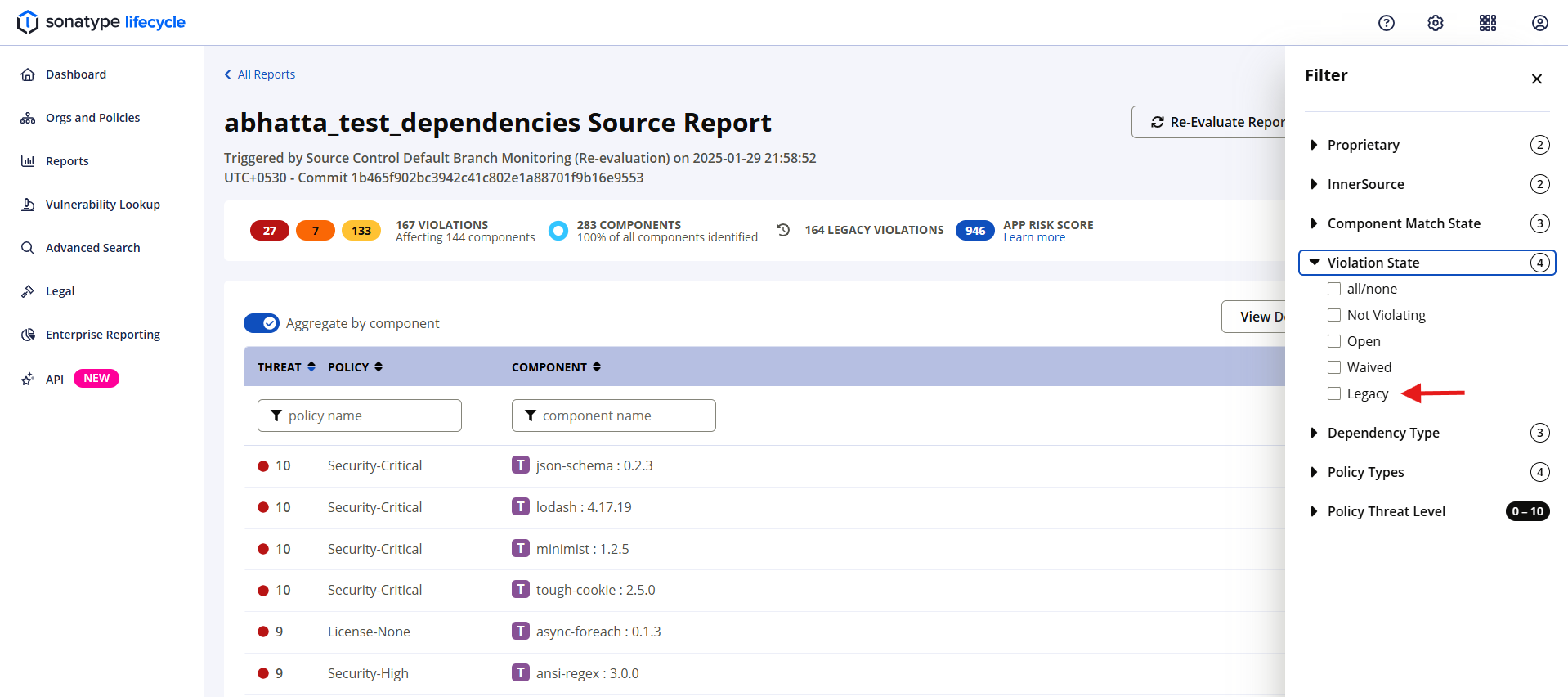
Please note that that Legacy Violations are not displayed when the report's Aggregated view is enabled (the default), so aggregation should be disabled when attempting to view the Legacy Violations.
Dashboard
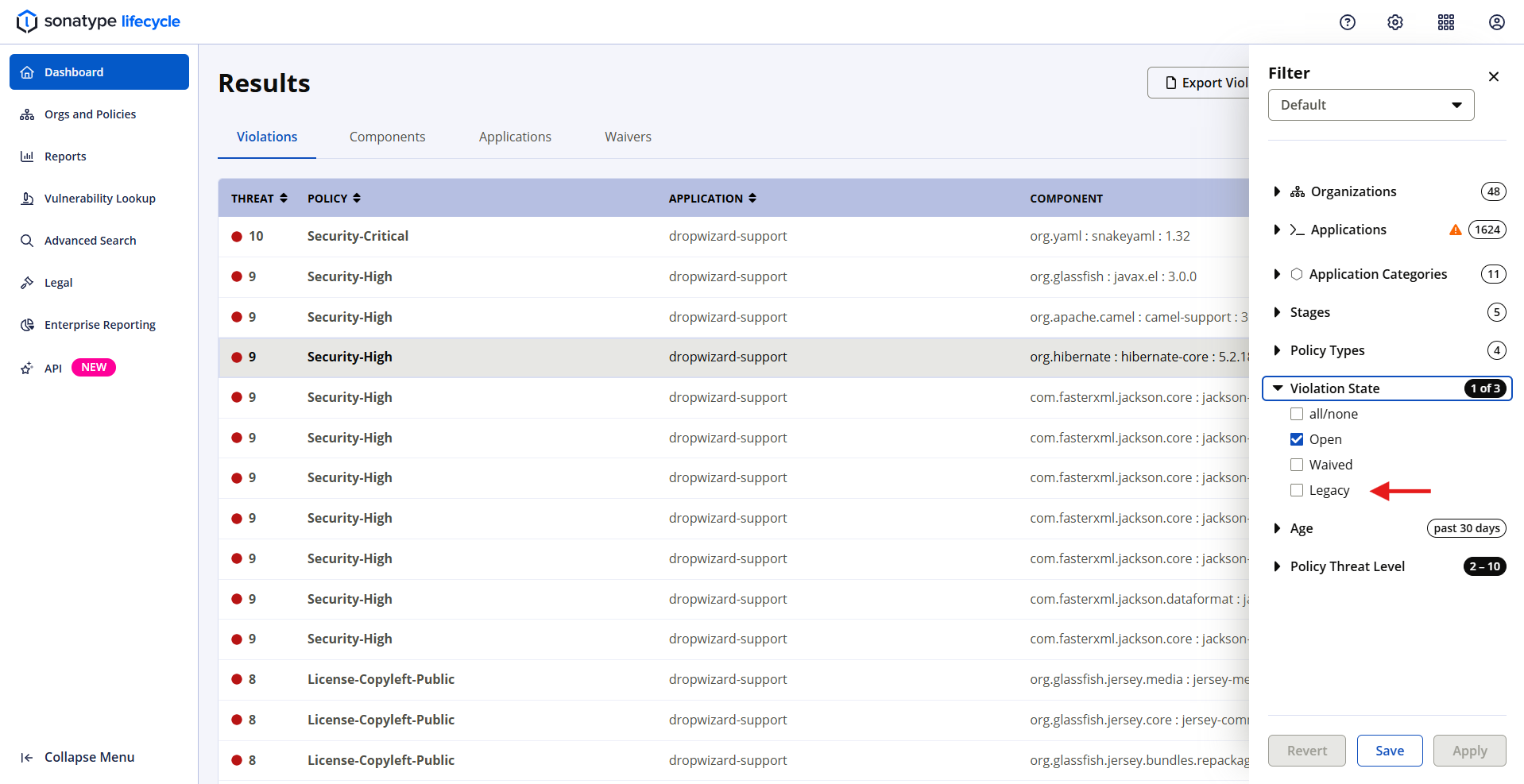
Legacy Violations can also be viewed using the filters on the Dashboard. Select the Violation State filter in the sidebar and select the Legacy checkbox to include Legacy Violations in dashboard results.
PDF Report
The number of Legacy Violations appears in the PDF Report under the Scope of Analysis section.
Notification Emails
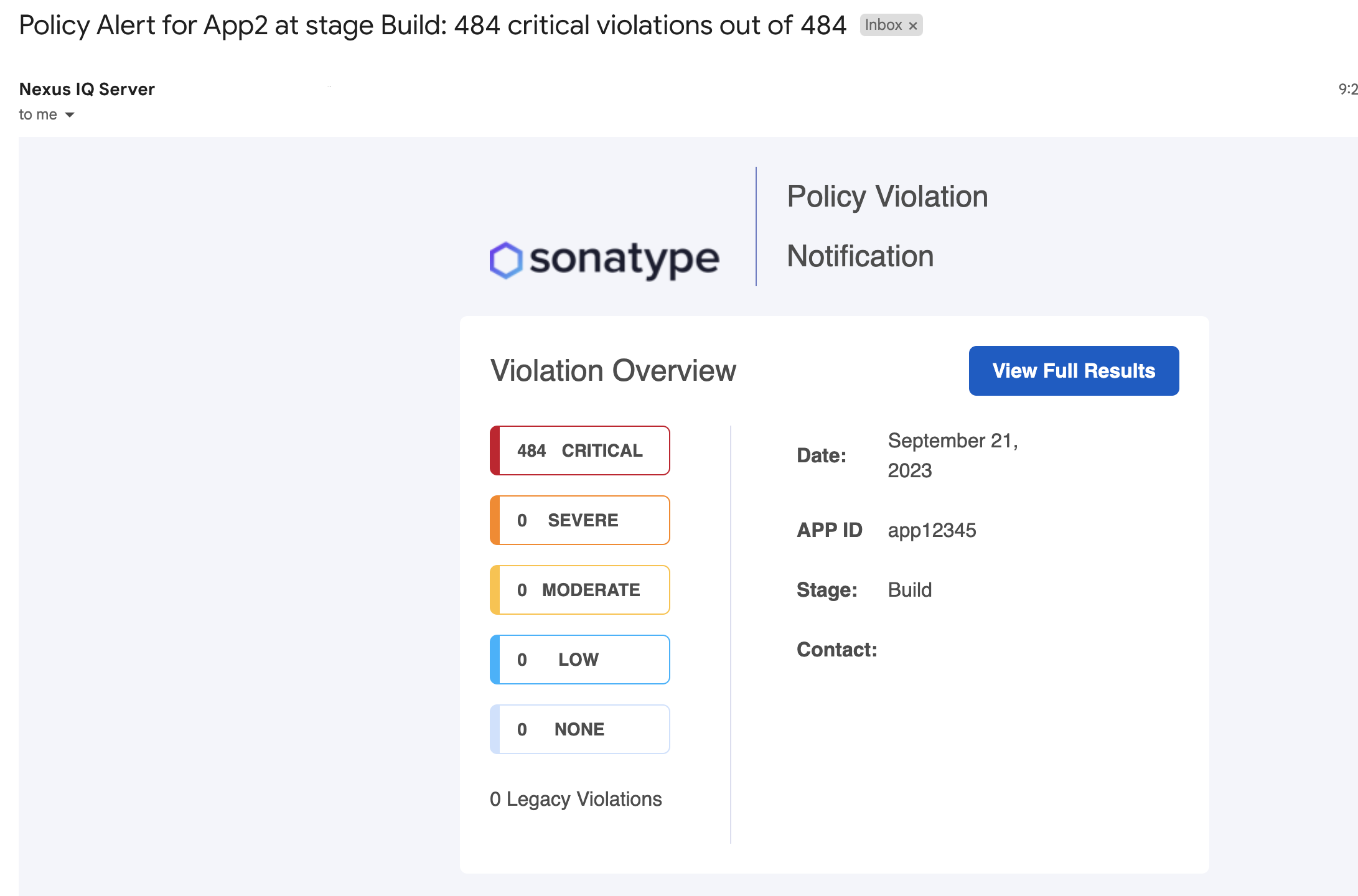
Notification emails that are sent for policy violations will contain the number of Legacy Violations.
 |
Assigning Existing Policy Violations as Legacy Violations
Existing policy violations can be set as Legacy Violations at the application level. Subsequent evaluations will treat these policy violations as Legacy Violations, but this action does not perform a new evaluation. This action will only be available if Legacy Violation is enabled or inherited for the application.
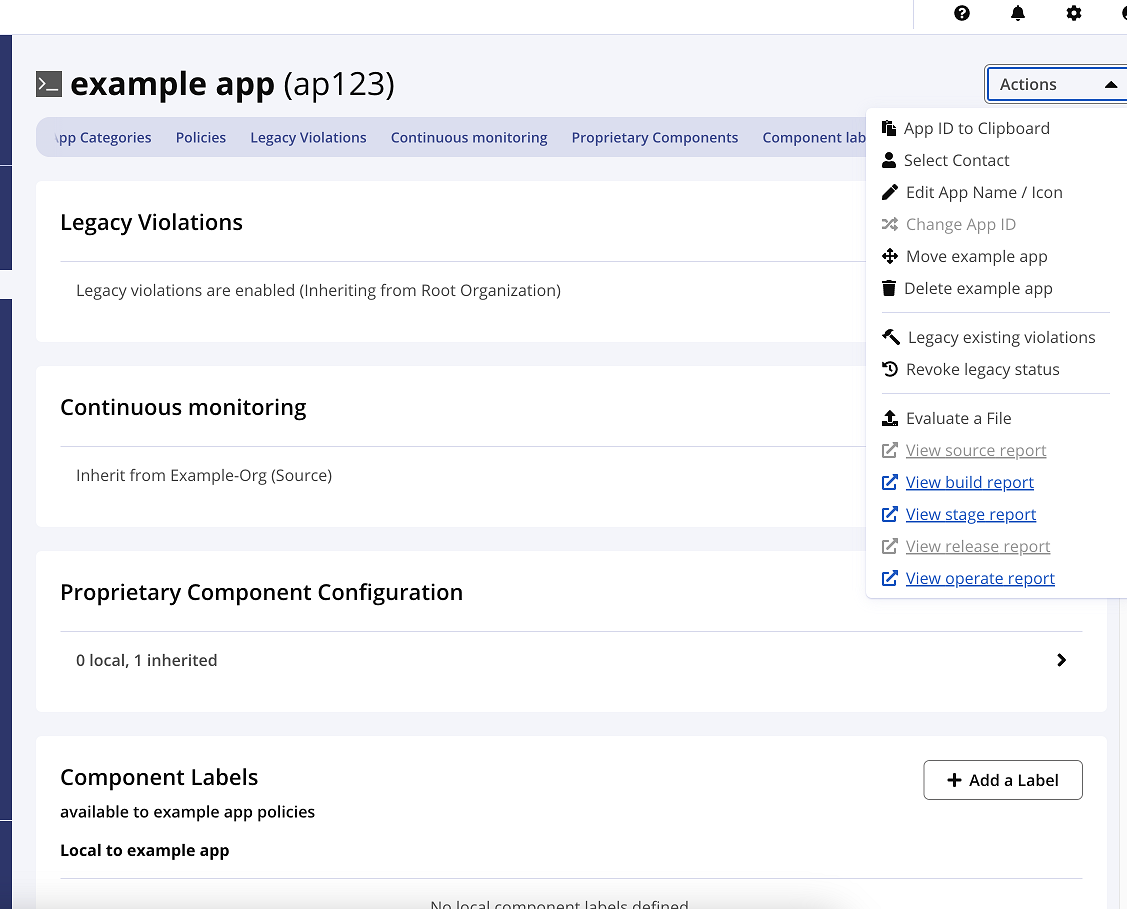
For existing policy violations for an application:
Select the application from the sidebar.
Click the Legacy Violations <application name> item in the Actions menu.
 |
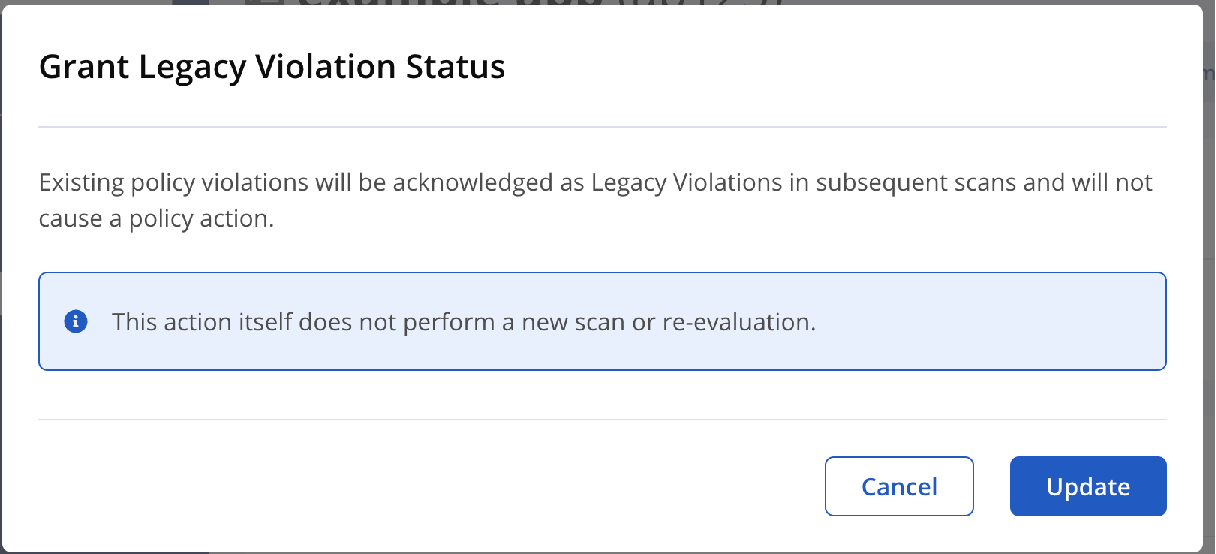
A modal dialog will ask you to confirm the action before proceeding.
 |
Revoking Legacy Violation status
Violations for applications that have been assigned Legacy Violation status can be revoked. Subsequent scans and re-evaluations will include these policy violations if applicable, but existing reports will not change.
To revoke Legacy Violation status for an application:
ClickOrgs and Policieson the left sidebar.
Select the application.
Click the Actions menu in the top right and select Revoke legacy status.
Click Revoke in the dialog box.
 |