Nexus Repository Professional Features
Sonatype Nexus Repository Community Edition provides a solid foundation for any organization getting started with fully managing its software supply chain. As usage grows and your teams require more mature capabilities, we recommend upgrading to the Nexus Repository Professional edition to unlock the features needed to fully support your critical infrastructure.
The following features as some of the benefits you unlock when you upgrade to Pro. Click here to start your free trial.
World Class Enterprise Support
Sonatype Nexus Repository Pro users receive access to our world-class support organization. This highly skilled group works with you to resolve issues encountered while using the product.
Details are found in our Support Policy.
Customer Success
Sonatype invests in every enterprise customer through our Customer Success team. This team is unique in that they proactively and continuously collaborate with you to ensure you derive ongoing value from your investment.
Ask them about training in repository management for your teams and providing a Repository Health Check to perform a details review of your development while providing guidance to help your organization mature.
High Availability and Resilient Deployments
Nexus Repository is mission-critical for your business. Highly available (HA) deployments protect your business in the event of disaster or outages. We include a growing list of resilient deployment architectures and recovery tools to protect your investment.
Nexus Repository Pro protects your data from risk while reducing your recovery time and meeting recovery point objectives.
SAML Authentication and Single Sign-On
Nexus Repository Pro integrates with many identity providers for centralized identity management. Using SAML, Nexus Repository acts as a service provider that receives users' authentication and authorization information from external identity providers.
User Token Support
Sonatype Nexus Repository Pro’s user token feature establishes a two-part token for the user. Usage of the token acts as a substitute method for authentication that would normally require passing your username and password in plain text.
User tokens reduce the risk of exposing your enterprise credentials when using external tools such as CI build services, automation tools, development environments, and scripting with the REST APIs. Administrators may reset and rotate keys from within the Nexus Repository as part of their security policies.
Content Replication
Teams today rarely work from a single location, so why should artifacts be stuck in one? Content replication allows you to make artifacts readily available across distributed teams. With content replication, you can manage what binaries are copied from one instance and pre-emptively pulled via HTTP to other instances. Here's how it works:
New assets are published to the Nexus Repository source instance
The replication task runs on the target instance on a schedule (each minute) to identify new assets
The replication task issues proxy requests for each new asset to replicate them to the target instance
Users on the target instance now have access to newly added artifacts on the target instance
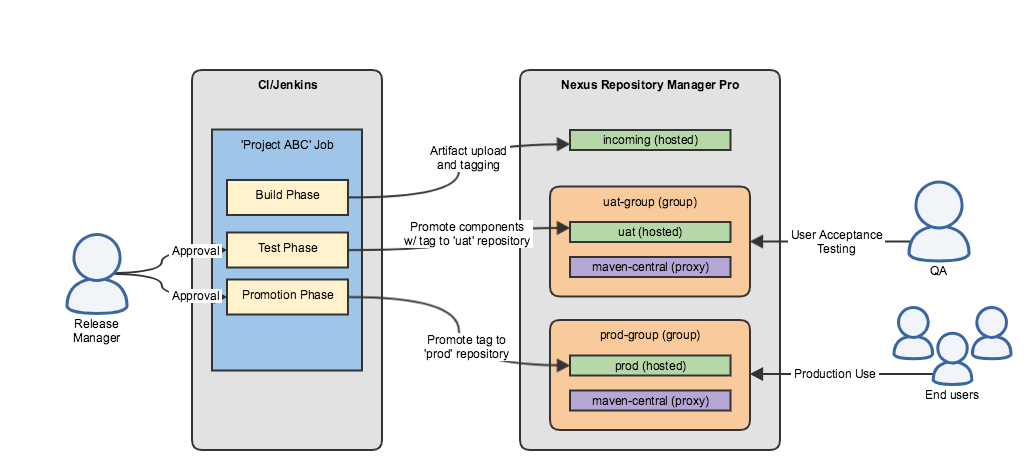
Staging and Build Promotion
Nexus Repository Pro provides Staging and Build Promotion capabilities to ensure the integrity and quality of software components before they are released. This feature allows organizations to implement controlled workflows for validating, testing, and promoting artifacts through different lifecycle stages.
With staging, users can temporarily hold newly published components in an isolated repository before making them available in a release repository. This approach helps prevent the accidental deployment of incomplete or unverified artifacts. Build promotion further enhances this process by enabling teams to transition artifacts from one repository to another based on validation criteria, ensuring that only approved versions reach production.
By integrating Staging and Build Promotion into their software development lifecycle, teams can enforce quality gates, reduce deployment risks, and maintain better governance over their repositories.
For more details, refer to the Staging documentation.
 |
Tagging
Nexus Repository Pro includes a Tagging feature that allows users to assign metadata tags to repository components, simplifying asset organization, tracking, and management. By applying tags, teams can efficiently categorize and reference specific artifacts across different repositories, enabling better version control and lifecycle management.
With Tagging, users can:
Identify and group related components for streamlined retrieval.
Track artifacts across different development and deployment stages.
Integrate tagging into automated workflows for enhanced DevOps processes.
This feature is particularly useful for managing artifacts in large-scale environments, where clear identification and traceability are essential for governance and compliance. The implementation is highly flexible to include any metadata you need to track with the components.
For more details, refer to the Tagging documentation.
Retain Select Versions for Cleanup Policies
Nexus Repository Pro includes the Retain Select Versions feature as part of its cleanup policies, providing greater control over artifact retention. This feature allows users to specify and preserve particular versions of components while automatically removing older or unnecessary versions based on defined cleanup rules.
By leveraging Retain Select Versions, organizations can ensure that critical versions remain available while optimizing storage usage and maintaining repository hygiene. This capability is especially beneficial for teams that need to keep specific releases for compliance, rollback, or long-term support purposes while still automating repository cleanup.
For more details, refer to the Cleanup Policies documentation.
Import and Export Repositories
Importing and exporting repositories is a common enterprise capability to move a large number of components between repositories or repository managers. Use cases to utilize import and export include:
Migrating content from Nexus Repository 2
Consolidating deployed repository managers into a single instance
Transfer components between disconnected instances
Consolidating multiple repositories into a single repository
These tasks keep track of the last run results and if run again, they will skip files that were processed previously. These tasks work with HA-C setup.
A temporary file system location is needed for these tasks to export to and import from. Please also ensure the Sonatype Nexus Repository instance running the task has sufficient disk space for export and blob storage for import before running this task to avoid disk full issues.
Google Cloud Blob Store
The Google Cloud Storage Blob Store allows assets to be stored in a Google Cloud Storage (GCS) bucket. Nexus Repository Pro can take advantage of the storage features that Google Cloud provides, such as redundancy options, configurable storage classes, and access control when running within the Google Cloud environment.
Azure Blob Store
The Azure Blob Store allows assets to be stored in an Azure Storage Account container. Nexus Repository Pro can take advantage of the storage features that Azure provides such as replication, configurable performance profiles, and access control when running from within the Azure cloud.
Group Blob Stores
A group blob store combines multiple blob stores to function as a single location for your repositories. Members of the group can be added or removed. Fill Policies are selectable algorithms that determine to which group member a blob is written. These features significantly increase the flexibility customers have in using and upgrading their storage. More information can be found in the Storage Guide.
Change Repository Blob Store
Change repository blob store is a task that allows changing the blob store of a given repository. It moves the blobs from the chosen repository to a different blob store.
Some common use cases to utilize the Change Repository Blob Store task:
A blob store reaching maximum capacity. You could use this task to move repository content freeing up space for other repositories in the original blob store.
Decommissioning of a blob store.
Docker Subdomain Connector
Nexus Repository Pro supports the Docker Subdomain Connector, allowing users to configure a dedicated subdomain for their Docker repositories. This feature simplifies repository access by enabling fully qualified domain names (FQDNs) for Docker registries, eliminating the need to specify a port number when pulling or pushing images.
By using the Docker Subdomain Connector, organizations can improve usability, align with industry best practices, and integrate seamlessly with Docker clients and automation tools. This functionality is particularly useful in environments where security policies restrict non-standard ports or where multiple Docker repositories require clear separation by domain.
For more details, refer to the Docker Subdomain Connector documentation.
Deployment to Group Repositories
Nexus Repository Pro supports Deployment to Group Repositories for npm and Docker registries, allowing users to publish artifacts to a group repository. When configuring the group, a hosted repository is set to store published artifacts. This feature simplifies artifact management by enabling deployment to a single endpoint while ensuring that the artifact is available to all member repositories within the group.
This capability enhances repository management efficiency and is particularly beneficial for teams that require centralized artifact deployment while maintaining access through a unified repository group.
Reduced the required docker ports
Using a single endpoint to pull and publish means fewer exposed docker connector ports are required.
Reduced storage
Docker groups reuse layers published across mutiple repositories reducing the required storage. Published images only require that the proprietary layers are pushed.
Simple client configuration
Docker doesn't provide a way to specify different endpoints for pushing and pulling content complicating the build process. This feature lets you configure a single endpoint.
Repository Health Check (RHC)
Nexus Repository users can automatically identify open-source security risks at the earliest stages of their DevOps pipeline. Specifically, the RHC feature empowers software development teams with important capabilities:
Prioritizes the list of vulnerable components by severity and impact, detailing how many times each component was downloaded from the repository manager by developers in the past 30 days.
Provides actionable guidance on which components housed in the repository manager should be upgraded or replaced.
Atlassian Crowd Support
Atlassian Crowd is a single sign-on and identity management product that many organizations use to consolidate user accounts and control which users and groups have access to which applications. Atlassian Crowd support is a feature preinstalled and ready to configure in Nexus Repository Pro. Nexus Repository contains a security realm that allows you to configure Nexus Repository to authenticate against an Atlassian Crowd instance.